Professional Documents
Culture Documents
Exchange Security Best Practices
Uploaded by
tousifaslam0 ratings0% found this document useful (0 votes)
17 views4 pagesCopyright
© Attribution Non-Commercial (BY-NC)
Available Formats
DOCX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Attribution Non-Commercial (BY-NC)
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
17 views4 pagesExchange Security Best Practices
Uploaded by
tousifaslamCopyright:
Attribution Non-Commercial (BY-NC)
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
You are on page 1of 4
Exchange Server Security Guidelines
Do not install Exchange Server 2003 on a domain controller.
Load the operating system and secure it before loading Exchange onto the platform.
It is important to realize that the system cannot be considered to be secured until the operating system has
first been secured. If the operating system is not secured, Exchange functionality might be secure but the
platform as a whole will be vulnerable.
Ensure the following services have been started before attempting to install Exchange:
o NNTP
o HTTP
o SMTP
o World Wide Web
o .NET Framework
Ensure that all relevant operating system security patches have been applied.
Ensure that all relevant Exchange security patches have been applied.
Exchange Administrator should require a User’s network/domain username to be different than their email
alias. The possible threat in not following this recommendation: once a malicious user has access to your
email address, they now have a valid network/domain username to conduct malicious activity.
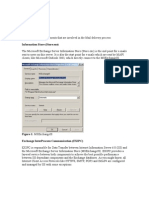
Subscribe to the Windows Security mailing list at:
http://www.microsoft.com/technet/security/bulletin/notify.mspxMode vs. Mixed
Mode
Exchange Server 2003 can operate in two modes: native mode and mixed mode. Native mode does not
allow Exchange 2003 to interoperate with Exchange 5.5 systems.
Configure log files so that they are written to partitions that are separate from the partitions used by the
Exchange Stores.
Implement an anti-virus solution for email scanning.
Remove all unnecessary services; this can be done easily by SCW provided in win2003 SP1.
Apply the latest service packs and all subsequent hot fixes.
Messaging Security
o Create lists of approved IP addresses and domain names
o Enable logging and monitor your servers regularly
o Prevent SMTP relay on your servers
Using Application Filtering to protect traffic to and from exchange server.
o Advanced firewalls can provide advanced inspection at the application protocol level.
This inspection allows the firewall to perform functions such as filtering RPC interfaces
and validating HTTP request syntax. Application filtering is the main reason why using an
advanced firewall in your topology provides the most security.
Regularly check DNS-based Blacklists to check if your server is spamming, like
o http://www.mxtoolbox.com/blacklists.aspx
Run Microsoft best practices analyzer tool after completing the installation/configuration
process.
Strengthen security by using Front-end/Back-end server configuration. Exchange 2003 supports front-end
and back-end server architectures. The front-end server is a server running Exchange 2003 that does not
host mailboxes or public folder stores. The front-end server forwards client requests to the back-end server
for processing. Mailboxes and/or public folder stores are hosted on the back-end server(s) that are running
Exchange 2003. The advantages of using front-end/back-end server topology are as follows:
o A single namespace for each user.
o Offload processing.
o Strengthened security: Front-end server can be positioned as the single point of access and located
after a firewall(s).
Scalability: As an enterprise expands, adding additional front-end and back-end servers can assist in the
expansion as well as address load balancing issues.
Figure below depicts the recommended Exchange front-end and back-end server architecture.
Configuring the Firewalls for Front/backend Firewalls
Configure the Internet firewall (between the Internet and the front-end servers)
o Open TCP ports on the Internet firewall for the mail protocols:
443 for HTTPS
993 for SSL-enabled IMAP
995 for SSL-enabled POP
25 for SMTP (including TLS)
If using a front-end server in a perimeter network, configure the intranet firewall:
o Open TCP ports on the intranet firewall for the protocols you are using:
80 for HTTP
143 for IMAP
110 for POP
25 for SMTP
691 for Link State Algorithm routing protocol
o Open ports for Active Directory Communication:
TCP port 389 for LDAP to Directory Service
UDP port 389 for LDAP to Directory Service
TCP port 3268 for LDAP to Global Catalog Server
TCP port 88 for Kerberos authentication
UDP port 88 for Kerberos authentication
o Open the ports required for access to the DNS server:
TCP port 53
UDP port 53
o Open the appropriate ports for RPC communication:
TCP port 135 - RPC endpoint mapper
TCP ports 1024+ - random RPC service ports
Roles and services.
Exchange 2003 Servers can be configured to function with a specific role. That is, as an HTTP Server, IMAP4
Server, POP3 Server, NNTP Server or SMTP Server. Table below identifies services on the server that must be
enabled and started for a role to function. For example, if your server was configured as a POP3 server, both
Microsoft Exchange POP3 service and the IIS Manager Service should be started. The SMTP service must be
running on every Exchange Server 2003, because the entire Exchange Server 2003 messaging system depends on it.
Without the SMTP service, Exchange will not function.
You might also like
- Using RPC Over HTTP With Exchange Server 2003 SP1: Author: Bill BoswellDocument19 pagesUsing RPC Over HTTP With Exchange Server 2003 SP1: Author: Bill Boswellzobair123No ratings yet
- Evaluation of Some SMTP Testing, Email Verification, Header Analysis, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsFrom EverandEvaluation of Some SMTP Testing, Email Verification, Header Analysis, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsNo ratings yet
- Unit V: Introduction To: Session, Presentation and APPLICATION LayersDocument47 pagesUnit V: Introduction To: Session, Presentation and APPLICATION LayersNiranjan AcharyaNo ratings yet
- SonicOS Advanced Outlook Web Access (OWA) Configuration With Exchange Across SonicWALL FirewallDocument4 pagesSonicOS Advanced Outlook Web Access (OWA) Configuration With Exchange Across SonicWALL FirewallBeeboopCharlyNo ratings yet
- Planning Your First Exchange ServerDocument8 pagesPlanning Your First Exchange ServerShrey GuptaNo ratings yet
- Evaluation of Some SMTP Testing, SSL Checkers, Email Delivery, Email Forwarding and WP Email Tools: Evaluation of Some SMTP Testing, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsFrom EverandEvaluation of Some SMTP Testing, SSL Checkers, Email Delivery, Email Forwarding and WP Email Tools: Evaluation of Some SMTP Testing, SSL Checkers, Email Delivery, Email Forwarding and WordPress Email ToolsNo ratings yet
- CBT Nuggets-Exchange Server 2003Document47 pagesCBT Nuggets-Exchange Server 2003Vivek MishraNo ratings yet
- Implementing Outlook Web Access With Exchange Server 2003Document8 pagesImplementing Outlook Web Access With Exchange Server 2003api-3747051100% (3)
- Multi SitesDocument28 pagesMulti SitesHari KishanNo ratings yet
- Using ISA Server 2004 With Exchange Server 2003Document39 pagesUsing ISA Server 2004 With Exchange Server 2003Ion DanNo ratings yet
- What Is Exchange ServerDocument16 pagesWhat Is Exchange Serverkmrs_888No ratings yet
- CH 5Document91 pagesCH 5avantikabakshiNo ratings yet
- Chapter 10 - Securing The Web Environment: at A GlanceDocument9 pagesChapter 10 - Securing The Web Environment: at A Glanceghar_dashNo ratings yet
- WIA1005 Network Technology Foundation: Application Layer and Build A Small NetworkDocument33 pagesWIA1005 Network Technology Foundation: Application Layer and Build A Small NetworkAina NajihahNo ratings yet
- Port NumbersDocument10 pagesPort NumbersRamkumar AruchamyNo ratings yet
- Implementing RPC Over HTTPSDocument9 pagesImplementing RPC Over HTTPSapi-19973860No ratings yet
- SMTP Stands For Simple Mail Transfer Protocol. It Is A TCP/IPDocument12 pagesSMTP Stands For Simple Mail Transfer Protocol. It Is A TCP/IPAdanAhmedNo ratings yet
- In Introduction To HTTP BasicsDocument21 pagesIn Introduction To HTTP BasicsAlice StateNo ratings yet
- Free Comptia Network+ Study Guide by MC McseDocument48 pagesFree Comptia Network+ Study Guide by MC McseMalluNo ratings yet
- Materi Review Mtcna 12 TKJ ADocument52 pagesMateri Review Mtcna 12 TKJ ARidaalissandraNo ratings yet
- N+ Short Notes Free CompTIA Network+ Study Guide by MC MCSE)Document23 pagesN+ Short Notes Free CompTIA Network+ Study Guide by MC MCSE)Ye Zeiya SheinNo ratings yet
- List of Common Network Port Numbers: Port Service Name Transport ProtocolDocument6 pagesList of Common Network Port Numbers: Port Service Name Transport ProtocolChakravarthy DoppalapudiNo ratings yet
- Configuration of Postfix Mail Server Supporting Anti Spam and Anti VirusFrom EverandConfiguration of Postfix Mail Server Supporting Anti Spam and Anti VirusNo ratings yet
- Protocols in Application Layer 17.01.2024Document4 pagesProtocols in Application Layer 17.01.2024Aloysius DsouzaNo ratings yet
- Network+ Exam Cram Study SheetDocument3 pagesNetwork+ Exam Cram Study SheetDan Sheets86% (21)
- Application-Level ServicesDocument26 pagesApplication-Level ServicesalinionutNo ratings yet
- Ccna 1Document40 pagesCcna 1Dragos CraciunNo ratings yet
- ITCNA - Chapter 6 - Supporting Network ServicesDocument52 pagesITCNA - Chapter 6 - Supporting Network ServicesLinda BurgNo ratings yet
- CCNA LabManual NewDocument142 pagesCCNA LabManual Newyashveer100% (1)
- Unix Network Lab ManualDocument37 pagesUnix Network Lab Manualabheeshek_sharmaNo ratings yet
- Imp For InterviewDocument16 pagesImp For InterviewPravin PuriNo ratings yet
- The 7 Layers of The OSI Model Are Shown BelowDocument18 pagesThe 7 Layers of The OSI Model Are Shown BelowraichedNo ratings yet
- Question 1. What Is An Aws Availability Zone?: AnswerDocument13 pagesQuestion 1. What Is An Aws Availability Zone?: Answerlkfdsn fdksljflksNo ratings yet
- UOK NETWORKING - Chapter 3 - TCP - IP MODEL PROTOCOLS (LEONCE 2021)Document46 pagesUOK NETWORKING - Chapter 3 - TCP - IP MODEL PROTOCOLS (LEONCE 2021)rutayisire steveNo ratings yet
- Security/Firewall Requirements: Ports To Be Opened When Monitors Are Behind The FirewallDocument4 pagesSecurity/Firewall Requirements: Ports To Be Opened When Monitors Are Behind The FirewallJason LiuNo ratings yet
- Plesk 10 Pci Compliance GuideDocument10 pagesPlesk 10 Pci Compliance GuideJack JillNo ratings yet
- Starting Guide for Postfix Mail Server Configuration Supporting Anti Spam and Anti VirusFrom EverandStarting Guide for Postfix Mail Server Configuration Supporting Anti Spam and Anti VirusNo ratings yet
- Application Layer ProtocolsDocument3 pagesApplication Layer Protocolsalimghal41No ratings yet
- Network CompTIADocument38 pagesNetwork CompTIApedrazini18100% (1)
- Amjilt HoyrooDocument6 pagesAmjilt HoyrooMunkhbayarNo ratings yet
- Hacking Network Protocols: Unlocking the Secrets of Network Protocol AnalysisFrom EverandHacking Network Protocols: Unlocking the Secrets of Network Protocol AnalysisNo ratings yet
- Comptia-Network Study GuideDocument36 pagesComptia-Network Study GuideJonathan Velez Velazquez100% (3)
- How To Configure RPC Dynamic Port Allocation To Work With Firewalls (KB154596)Document4 pagesHow To Configure RPC Dynamic Port Allocation To Work With Firewalls (KB154596)AldineYapNo ratings yet
- Replicating Traffic Between Domain ControllersDocument3 pagesReplicating Traffic Between Domain ControllersLohith Achar100% (1)
- Lab3 3Document7 pagesLab3 3ruksandradNo ratings yet
- CCNA Resumen SinopticoDocument7 pagesCCNA Resumen SinopticoHeather MillerNo ratings yet
- FTP - Ibm ManualDocument60 pagesFTP - Ibm ManualAkarsh Verma0% (1)
- N+ Study MaterailDocument59 pagesN+ Study MaterailasimalampNo ratings yet
- Switch and Router ConfigurationDocument41 pagesSwitch and Router ConfigurationBroot KalNo ratings yet
- How To Set Up An FTPS Server in Linux - Open SourceDocument5 pagesHow To Set Up An FTPS Server in Linux - Open SourceCecoprod SemarNo ratings yet
- A Bit of HistoryDocument13 pagesA Bit of HistoryPavan KumarNo ratings yet
- Learning Outcomes Questions 1 (30 Marks) 2,3 (35 Marks) : Hardware, Software, Systems & Networks Exam Review AnswersDocument4 pagesLearning Outcomes Questions 1 (30 Marks) 2,3 (35 Marks) : Hardware, Software, Systems & Networks Exam Review AnswersAnishNo ratings yet
- Oracle Database ConnectivityDocument8 pagesOracle Database Connectivitymrn_bdNo ratings yet
- Exchange Interview QuestionsDocument187 pagesExchange Interview QuestionsVipul KumarNo ratings yet
- The Socket InterfaceDocument24 pagesThe Socket InterfaceRavi Srinivas100% (1)
- Extended SMTP - Wikipedia enDocument4 pagesExtended SMTP - Wikipedia enNam NguyenNo ratings yet
- Ibrahiem Elbarki FTPDocument18 pagesIbrahiem Elbarki FTPAhmed AboubakrNo ratings yet
- EXP 7 Server - ConfigDocument2 pagesEXP 7 Server - ConfigPriyansh RupaniNo ratings yet
- ASV Program Guide v2Document38 pagesASV Program Guide v2tousifaslamNo ratings yet
- Ericsson Network SecurityDocument14 pagesEricsson Network SecuritytousifaslamNo ratings yet
- ISO 13485 2003 Audit ChecklistDocument38 pagesISO 13485 2003 Audit Checklisttousifaslam100% (1)
- ISO 13485 2003 Audit ChecklistDocument38 pagesISO 13485 2003 Audit Checklisttousifaslam100% (1)
- Full Stack Curriculum.Document8 pagesFull Stack Curriculum.Siladitya MitraNo ratings yet
- PROTEGIDODocument232 pagesPROTEGIDOJose Manuel Catacora Huarachi100% (1)
- AWR Explanation GoodDocument91 pagesAWR Explanation GoodmaleshgNo ratings yet
- Output LogDocument466 pagesOutput LogJoshua OmboyNo ratings yet
- Intelligent Control of Capillary Irrigation System For Water-Saving CultivationDocument3 pagesIntelligent Control of Capillary Irrigation System For Water-Saving CultivationAnonymous 1aqlkZNo ratings yet
- PatelDocument10 pagesPatelArpan PatelNo ratings yet
- Datasheet of DS 7608NI K2 - 8P NVRD - V4.31.610 - 20220412Document4 pagesDatasheet of DS 7608NI K2 - 8P NVRD - V4.31.610 - 20220412SamiraNo ratings yet
- IDM-AD Inetgration - Step by StepDocument6 pagesIDM-AD Inetgration - Step by Steparm_max78No ratings yet
- HVDCT Question BankDocument2 pagesHVDCT Question BankPritesh PandyaNo ratings yet
- Notes - Responsive Designs-2533Document10 pagesNotes - Responsive Designs-2533Mannu GavelNo ratings yet
- Module 4 Software Analysis and DesignDocument14 pagesModule 4 Software Analysis and Designhanif malgundkarNo ratings yet
- Using The Go Programming Language PDFDocument68 pagesUsing The Go Programming Language PDFspywangNo ratings yet
- Chapter5 Unfolding Parhi BookDocument30 pagesChapter5 Unfolding Parhi Bookleonemoe3762No ratings yet
- Fundamentals of 5g Wireless Communications Sachan Book 82 - CompressDocument171 pagesFundamentals of 5g Wireless Communications Sachan Book 82 - CompressBijoy BanerjeeNo ratings yet
- Assignment Automatic Drilling MachineDocument6 pagesAssignment Automatic Drilling MachineSumit KambleNo ratings yet
- Arch 21Document4 pagesArch 21Nishant JaiswalNo ratings yet
- Detailed Course OutlineDocument34 pagesDetailed Course OutlineMuhammad MuniruddinNo ratings yet
- 435USB-NNAU Userguide PDFDocument41 pages435USB-NNAU Userguide PDFi_aordazNo ratings yet
- Cxoneremover Op Inst e 1005Document6 pagesCxoneremover Op Inst e 1005Anggoro Indarto AkbarNo ratings yet
- Especificaciones Tecnicas - SM5100B DatasheetDocument33 pagesEspecificaciones Tecnicas - SM5100B DatasheetEric AliagaNo ratings yet
- Unit 14 p1Document2 pagesUnit 14 p1api-319906681No ratings yet
- Debug 1214Document3 pagesDebug 1214123sudhirNo ratings yet
- Opennms System ReportDocument3 pagesOpennms System ReportDaniel BarreraNo ratings yet
- Product Data Sheet: Wiser For KNX Logic ControllerDocument2 pagesProduct Data Sheet: Wiser For KNX Logic ControllerMohamed AliNo ratings yet
- Project Smart ShoeDocument9 pagesProject Smart ShoeKashif AliNo ratings yet
- ARM7 Based Smart ATM Access SystemDocument3 pagesARM7 Based Smart ATM Access SystemEditor IJRITCCNo ratings yet
- I/A Series Hardware: ® Product SpecificationsDocument20 pagesI/A Series Hardware: ® Product Specificationsrasim_m1146No ratings yet
- Lect4 Stick DiagramDocument23 pagesLect4 Stick Diagrammanicks369601No ratings yet
- Physical LayerDocument20 pagesPhysical LayerVitthal KodgirwarNo ratings yet
- Sagittar SGT-LPN Manual Ver2.5Document92 pagesSagittar SGT-LPN Manual Ver2.5Ramiro MagnayonNo ratings yet