Professional Documents
Culture Documents
Secure Data Aggregation
Uploaded by
aishwarya waghCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Secure Data Aggregation
Uploaded by
aishwarya waghCopyright:
Available Formats
Secure Data Aggregation in WSN using Iterative
Filtering algorithm
Ekta Choudhari Ketan D. Bodhe Snehal M. Mundada
Dept. Of Computer Enginerring Dept. Of Computer Technology Dept. of Computer Engineering
DYPCOE Akurdi, PIET DYPCOE Akurdi,
Pune India Nagpur, India Pune, India
ektachoudhari5@gmail.com ketanbodhe@gmail.com Snehalmundada89@gmail.com
Abstract— In WSN Aggregation is considered as the most
susceptible to node compromising attacks, as wireless sensor
networks are not more secured so they are more vulnerable to
this type of attacks. For WSN it is essential to check the
trustworthiness of the data & reputation of sensor nodes. To
handle this issue Iterative Filtering acts as a best option. In
Iterative filtering algorithm (IF) the data is aggregated
concurrently from multiple sources & IF also render trust
assessment of these sources. The trust assessment is in the form of
similar weight factors assigned to data supplied by each source.
Considering the security as major issue in WSN, In this paper we
proposed an advancement for IF method by providing
approximation which will make them collusion robust and is
converging fast. Advancement in the Iterative Filtering algorithm
will enhance the performance of the system with good potential
for implementation in WSN, IF algorithm is stretched with Fig. 1: A data aggregation process in theWSN[1].
novel method for collusion detection & revocation based on an
initial approximation of the aggregate values as well as In these years, various IF algorithms have been proposed for
distribution of differences of each sensor readings. The proposed trust & reputation systems those algorithms demonstrate richer
system performance is checked through extensive simulation in robustness equated to the simple averaging methods; however,
C#. The simulation demonstrates the improved results. The RMS those algorithms have not been designed by conceiving more
value in the graphs for series 2(0.1, 0.18, 0.22, 0.22, 0.22, 0.3, 0.36, sophisticated collusion attack scenarios. Attacker can launch
0.38) with standard deviation ranging from 0.5 to 4 shows that more savvy attacks on the WSNs if they have the idea about
the proposed system performance is better as compare to existing
system.
the aggregation algorithm and its parameters. They can launch
the attack on WSN by exploiting false data injection through a
number of compromised nodes.
Keywords— Iterative Filtering, Data aggregation, Wireless sensor
network, Collusion attack . In Wireless Sensor Networks (WSNs) Trust & reputation
I. INTRODUCTION have been proposed as an efficient security mechanism.
Assessing trustworthiness of reported data from distributed
Currently, wireless sensor networks (WSNs) have been used sensors is a challenging task as sensor networks are being
in many applications, like military target tracking & more and more deployed in many application domains.
surveillance, wildlife monitoring & natural disaster relief.In a Iterative Filtering (IF) algorithms is the best alternative for
normal wireless sensor network, the sensor nodes have WSN as they render answers for data aggregation & data
determined resources such as battery power, computing trustworthiness assessment & using single iterative procedure.
capability, and memory. Communication is a rife source of This differs importantly from such estimate are assigned less
energy ingestion in the WSNs. Hence, the general method is to trustworthiness & accordingly in the aggregation procedure in
collectively process the sensor data, yielded by the various the current iteration their values are given a lower weight.
sensor nodes while carrying it to the base station. This
procedure is known as a data aggregation process. By suing, In this paper we proposed a novel advanced collusion
adding, & filtering the sensor data, the data aggregation attack scenario against a number of existing IF algorithms
process cuts a number of data transmissions & mends the based on false data injection. Due to the initial estimation of
bandwidth energy utilization in the WSNs. the IF algorithms is robust against such a sophisticated
WSN are usually redundant as need for robustness of collusion attack. We believe, more robust under significantly
monitoring & low cost of nodes. Multiple sensor sends the more general circumstances. This contrast to the conventional
data which is aggregated at an aggregator node & which then non iterative statistical sample estimation technique which is
is forwarded to the base station only the aggregate values.
not robust against false data injection by a number of The main contribution of authors in [11] is to propose a
compromised nodes & severely skewed in presence of system which collectively combines trust mechanism,
complete sensor failure. IF algorithm with a novel approach aggregation of data, and tolerance of faults to increase
for collusion detection & sensor node revocation is added. trustworthiness of data in Wireless Multimedia Sensor
Networks (WMSNs). Author [12] proposed a framework to
The remainder of this paper is organized as follows. We discover attacked or faulty nodes in WSN. They stated that the
provide an deep literature survey on the existing methods of IF revocation of discovered nodes cannot be done due to danger
for data aggregation in Section II. Section III describes the of false positive in the proposed scheme.
architecture of the proposed system and working of the
proposed system with the implementation details is explain in The main idea of detecting faulty aggregator in the scheme
Section IV and Conclusion is then given in Section V. proposed in [13] is to use multiple monitoring nodes which are
used for aggregation and providing a MAC value of their
results as a part of MAC in the value calculated by the cluster
II. RELATED WORK aggregator. Authors in [14] proposed a game-theoretical
Aggregating data is a concern in WSNs and there are a strategy to sensor guard nodes and to assure a high level of
number of papers investigating data injection by taking with trustworthiness for the data sensed . Author designed a game-
the help of adversary models. There are three parts of work: theoretic defense strategy to defend detector nodes from
Filtering algorithms, trust and reputation systems for WSNs, attacks & to confirm a high level of trait for detected
and securing data aggregation in WSNs. Increasing amount of information. we have a tendency to use a distinct time model,
work has been done on iterative filtering technique and and that we take into account that there's a restricted attack
reputation based systems. budget that bounds the potential of the assailant in every
spherical. The defense strategy objective is to confirm that
The Basic idea of the algorithm proposed in [2] is to calculate adequate detector nodes area unit protected in every spherical
correlation coefficients between users and objects, which such the discrepancy between price accepted and also the
gives credence to users whose ratings correlate properly with truthful detected value is below a particular threshold. They
the estimated ratings of objects. An Filtering algorithm based have a tendency to model the attack-defense interaction as a
on a weighted averaging technique which the weights are Stackelberg game, and that we derive the equilibrium
computed by examining its distance of value generated from condition that's adequate to confirm that the detected
the actual or expected value is proposed in[3]. Authors in [4] information area unit truthful inside a nominal error sure.
proposed six algorithms, which are all iterative and are of Moreover, there is much more research published in the area
same kind. Only the aggregation function is changed. A of secure aggregation in WSNs [15], [16], [17].
different algorithm iterative in nature is shown in [5]. In which
1) the importance or significance of ratings decreased with In the WSN First, trust & reputation systems play
time and 2) all the bad raters are saved in a black list. Authors vital role as a approach of settling a number of important
in [6] proposed an iterative algorithm which is not only using problems, like secure routing, false data detection,
the rating matrix, also uses the social network of users. compromised node detection, secure data aggregation, cluster
head election, outlier detection, [18]. Second, sensors those
The main objective of author in [6] is to bring in a “Bias- are spread in unfriendly & neglected environments are
smoothed tensor model", which is instead a too complexity extremely liable to node compromising attacks [19]. While
Bayesian model. A trust framework for nodes in networks in offering better protection than the simple averaging, our
which each node develops a trust estimation for neighbor simulation results demonstrate that indeed current IF
nodes which make a reputed community for nodes in that algorithms are vulnerable to such new attack strategy. A
network is shown in [8]. Author in [9] proposed PRESTO, a systematic method Provenance-based trustworthiness
model based architecture for Hierarchical nodes. PRESTO is a assessment in sensor networks for assessing the
two tier framework for managing nodes in sensor networks. trustworthiness of data items is shown in [20]. This approach
Authors in [10] proposed an relationship in nodes and data for uses the data provenance as well as their values in computing
assessing their reputation scores based on a framework. trust scores, that is, quantitative measures of trustworthiness.
Systematic methodology for assessing the trustiness of Authors in [21] proposed IF algorithm for computing
knowledge things. Their approach uses the information reputation of objects and raters in a rating system. Also a
beginning further as their values in computing trust scores, correlation based ranking algorithm proposed in [22], in
that is, quantitative measures of trustiness. to get trust scores, which, trustworthiness of each sensor is gained depending on
they need propose a cyclic framework that well reflects the the correlation coefficient among the sensors readings & the
inter-dependency property: the trust score of the information current estimate of the true value of the signal. In other words,
affects the trust score of the network nodes that created and this method gives credit to sensor nodes whose readings
manipulated the information, and vice-versa correlate well with the estimated true value of the signal.
The literature survey lights on detecting false aggregation A. Methodology
operations by a foe, i.e., on data aggregator nodes acquiring Our proposed method renders a robust initial estimation of the
data from source nodes & giving wrong aggregated values. trustworthiness of sensor nodes to be used in the first iteration
Accordingly, they cover neither the problem of false data of the IF algorithm which will improve the functioning of IF
being furnished by the data sources nor the problem of algorithms against the aforementioned attack scenario. Sample
collusion. Still, when an adversary adds false data by a mean is use in most of the formal statistical estimation
collusion attack scenario, it can strikes the results of the honest methods for variances. And hence suggesting a robust
aggregators & hence the base station will get inclined variance estimation approach in the case of skewed sample
aggregate value. In this case, the compromised nodes will mean is essential part of our methodology.
manifest their false data & therefore the base station thinks
that all reports are from true sensor nodes. Although the
aforementioned research take into account false data injection 1. Finding a new powerful and complicated attack
for a number of simple attack scenarios, & work addresses against IF based reputations systems which brings out
emerge in the case of a collusion attack by compromised a stark exposure in IF algorithms;
nodes in a way which apply high level knowledge about data
aggregation algorithm. Although using the initial reputation 2. A new approach for error estimation of sensors nodes
results given by our approach makes IF algorithms more which is efficient in a wide range of sensor faults &
robust than their master version, the attacker can still change not susceptible to the described attack;
well the reputation results of the IF algorithms. Thus, in this
section we propose a unique attacker detection method in 3. Inspired by MLE we have design an effective &
order to advance lessen the impact of the compromised nodes. robust aggregation approach which employs an
estimate of the noise parameters gained using the
second point;
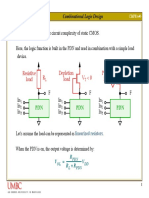
III. PROPOSED SYSTEM
We have considered the network model show in fig 2 for our 4. Our proposed enhanced IF approach is capable of
wireless sensor network. The sensor nodes in the network dealing against the collusion attack by rendering
make clusters, & every cluster has a cluster head which is an initial estimate of trustworthiness of sensors
aggregator. The aggregator collects the data after certain time employing inputs from second & third contributions
period and aggregates the collected data. Our aim is to focus above;
on algorithms which will make the aggregation process more
secure when the single node might be compromised & which 5. A novel collusion detection & revocation technique
can inject false data in to the aggregator. In our model we based on an initial approximation of the aggregate
considered that each data aggregator is has plenty values as well as distribution of differences of each
computational power to run IF algorithm for data aggregation. sensor readings.
A node posing highest energy is selected as cluster head
whereas base station has no energy constrain and is stationary.
Fig. 3: Architecture
Fig. 2: Network model
Algorithm
Input : X,n,m.
Output : Reputation vector r.
1. For every sensor Si (i=1… n) do, check energy
level
If (Esi > Esj)
Si is selected as CH
Else Si acts as normal Sensor nodes.
2. Calculate the initial reputation vector using MLE
3. Calculate Weight based on distance of reading to
initial reputation vector.
4. Iterative filtering with initial weights.
a. l<-0 Fig. 5: Biased Sensor node
b. Compute r(l+1)
c. Compute d
d. Compute w(l+1)
Where l is number of iteration
5. The nodes have less weight are considered as
compromised.
es = xs - r ;
where es is error xs sensor reading and r is the
estimated reputation vector.
6. Reapply step 2 to 4 to produce more accurate
readings.
7. Stop.
IV. RESULTS
Fig. 6: Biased sensor node
As per the proposed system, we have implemented the design
in c# and to test the efficiency of the proposed system we have
carried our extensive simulation & the obtained results are as Series 2 represent the values without collusion detection and
follow. series 3 represent the accuracy with fault detection module i.e
the proposed architecture. Results are calculated on the basis
For the unbiased nodes Series 2 represent the values without of how much the value of the sensor differs from the mean
collusion detection and series 3 represent the accuracy with value. Therefore graph is plotted as standard deviation vs.
collusion detection module. Here X axis represents the RMS (Root Mean Square Error). RMS is a frequently used
Variance and Y axis represents RMS (Root Mean Square Measure of the Differences between values predicted by an
Error). Here the results won’t vary because there is no attack estimator and values actually observed. Filtering with and
and the sensors are not biased. without Fault detection is shown and it clearly explains that
RMS is minimized by this filtering technique with Fault
detection. From the graphs we can see that 0.1, 0.18, 0.22,
0.22, 0.22, 0.3, 0.36, 0.38 is the obtain RMS for our proposed
system with respect to the standard deviation which shows the
performance of our proposes system is better than the existing
system.
V. CONCLUSION AND FUTURE SCOPE
In this paper we proposed a secure data aggregation technique
in WSN in which we have done an advancement in IF
algorithms by providing an initial approximation of the
trustworthiness of sensor nodes. The IF algorithms with a
novel approach for collusion detection & revocation depends
Fig. 4: Unbiased Sensor node on an initial approximation of the aggregate values as well as
differences of each sensor readings are presented. Extensive
simulation is carried out in C# to test out proposed approach.
We have tested our system on biased and unbiased nodes, and [16] Y. Yang, X. Wang, S. Zhu, and G. Cao, “SDAP: a secure hopby- hop
data aggregation protocol for sensor networks,” in MobiHoc, 2006, pp.
the results obtained shows that RMS is minimized by our 356–367.
advancement in the IF with the fault detection. This depicts [17] S. Roy, M. Conti, S. Setia, , and S. Jajodia, “Secure data aggregation in
results generated are better than the existing system wireless sensor networks,” Information Forensics and Security, IEEE
approaches which we studied in the literature survey. The Transactions on, vol. 7, no. 3, pp. 1040–1052, 2012.
main aim of this paper was to make the wireless sensor [18] Y.Yu, Li, w Trust mechanisms in wireless sensor networks: Attack
network more secure. analysis and countermeasures,” Journal of Network and Computer
Applications
In future, more advancement can be done in IF to
[19] K. Hoffman, D. Zage, and C. Nita-Rotaru, “A survey of attack and
enhance the security of data aggregation. Iterative filtering defense techniques for reputation systems,” ACM Comput. Surv., vol.
algorithm is best way to make the WSN secure, so while 42, no. 1, pp. 1:1–1:31, Dec. 2009.
altering this algorithm efficiency should be considered as [20] H.-S. Lim, Y.-S. Moon, and E. Bertino, “Provenance-based
important parameter. trustworthiness assessment in sensor networks,” in Proceedings of the
REFERENCES Seventh International Workshop on Data Management for Sensor
Networks, ser. DMSN 10, 2010, pp. 27.
[21] C. de Kerchove and P. Van Dooren, “Iterative filtering in reputation
[1] Nasridinov, Aziz, Sun-Young Ihm, and Young-Ho Park. "Skyline-based
systems,” SIAM J. Matrix Anal. Appl., vol. 31, no. 4, pp. 18121834, ar.
aggregator node selection in wireless sensor networks." International
2010.
Journal of Distributed Sensor Networks 2013 (2013).
[22] Y. Zhou, T. Lei, and T. Zhou, “A robust ranking algorithm to
[2] Yanbo Zhou, Ting Lei, and Tao Zhou. A robust ranking algorithm to
spamming,” CoRR, vol. abs/1012.3793, 2010.
spamming. CoRR, abs/1012.3793, 2010.
[3] P. Laureti, L. Moret, Y.-C. Zhang, and Y.-K. Yu. Information _ltering
via Iterative Re_nement. EPL (Europhysics Letters), 75:1006{1012,
September 2006.
[4] Rong-Hua Li, Je_rey Xu Yu, Xin Huang, and Hong Cheng. Robust
reputation-based ranking on bipartite rating networks. In SDM'12, pages
612{623, 2012.
[5] Erman Ayday, Hanseung Lee, and Faramarz Fekri. An iterative
algorithm for trust and reputation management. In Proceedings of the
2009 IEEE international conference on Symposium on Information
Theory – Volume 3, ISIT'09, pages 2051{2055, 2009.
[6] H. Liao, G. Cimini, and M. Medo. Measuring quality, reputation and
trust in online communities. ArXiv e-prints, August 2012.
[7] Bee-Chung Chen, Jian Guo, Belle Tseng, and Jie Yang. User reputation
in a comment rating environment. In Proceedings of the 17th ACM
SIGKDD international conference on Knowledge discovery and data
mining, KDD '11, pages 159{167, 2011.
[8] Saurabh Ganeriwal, Laura K. Balzano, and Mani B. Srivastava.
Reputation-based framework for high integrity sensor networks. ACM
Trans. Sen. Netw., 4(3):15:1{15:37, June 2008.
[9] Ming Li, Deepak Ganesan, and Prashant Shenoy. PRESTO: feedback-
driven data management in sensor networks. In Proceedings of the 3 rd
conference on Networked Systems Design & Implementation - Volume
3, NSDI'06, pages 23{23, 2006.
[10] Hyo-Sang Lim, Yang-Sae Moon, and Elisa Bertino. Provenance-based
trustworthiness assessment in sensor networks. In Proceedings of the
Seventh In- ternational Workshop on Data Management for Sensor
Networks, DMSN '10, pages 2{7, 2010.
[11] Yan Sun, Hong Luo, and Sajal K. Das. A trust-based framework for
fault- tolerant data aggregation in wireless multimedia sensor networks.
IEEE Trans. Dependable Secur. Comput., 9(6):785{797, November
2012.
[12] J.-W. Ho, M. Wright, and S. Das, “ZoneTrust: Fast zone-based node
compromise detection and revocation in wireless sensornetworks using
sequential hypothesis testing,” Dependable and Secure Computing,
IEEE Transactions on, vol. 9, no. 4, pp. 494–511, july-aug. 2012.
[13] S. Ozdemir and H. C¸ am, “Integration of false data detection with data
aggregation and confidential transmission in wireless sensor networks,”
IEEE/ACM Trans. Netw., vol. 18, no. 3, pp. 736–749, Jun. 2010.
[14] H.-S. Lim, G. Ghinita, E. Bertino, and M. Kantarcioglu, “A game-
theoretic approach for high-assurance of data trustworthiness in sensor
networks,” in Data Engineering (ICDE), 2012 IEEE 28th International
Conference on, april 2012, pp. 1192 –1203.
[15] H. Chan, A. Perrig, and D. Song, “Secure hierarchical innetwork
aggregation in sensor networks,” in Proceedings of the 13th ACM
Conference on Computer and Communications Security, ser. CCS ’06.
New York, NY, USA: ACM, 2006, pp. 278–287.
You might also like
- Research Article: A Lightweight Intelligent Intrusion Detection Model For Wireless Sensor NetworksDocument15 pagesResearch Article: A Lightweight Intelligent Intrusion Detection Model For Wireless Sensor NetworksPrakash ArumugamNo ratings yet
- Ijet V3i3p24Document4 pagesIjet V3i3p24International Journal of Engineering and TechniquesNo ratings yet
- Intrusion Detection System Using Gradient Boosted Trees For VANETsDocument7 pagesIntrusion Detection System Using Gradient Boosted Trees For VANETsIJRASETPublicationsNo ratings yet
- Secure Data Accumulation and Certification Procedure For Sensor NetworksDocument4 pagesSecure Data Accumulation and Certification Procedure For Sensor NetworksIOSRJEN : hard copy, certificates, Call for Papers 2013, publishing of journalNo ratings yet
- A Study On Proposed Distributed Attack Detection Algorithm Using Experimental and Simulation AnalysisDocument10 pagesA Study On Proposed Distributed Attack Detection Algorithm Using Experimental and Simulation AnalysisIOSRjournalNo ratings yet
- A Lightweight Secure Scheme For Detecting Provenance Forgery and Packet Drop Attacks in Wireless Sensor NetworksDocument1 pageA Lightweight Secure Scheme For Detecting Provenance Forgery and Packet Drop Attacks in Wireless Sensor NetworksKishore Kumar RaviChandranNo ratings yet
- Intrusion Prevention System Using Convolutional Neural Network For Wireless Sensor NetworkDocument12 pagesIntrusion Prevention System Using Convolutional Neural Network For Wireless Sensor NetworkIAES IJAINo ratings yet
- Distributed and Cooperative Hierarchical Intrusion Detection On ManetsDocument9 pagesDistributed and Cooperative Hierarchical Intrusion Detection On ManetsleloiboiNo ratings yet
- Energy Efficient Outlier Detection in WSNDocument4 pagesEnergy Efficient Outlier Detection in WSNInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- A Survey On Data Collection Techniques in Wireless Sensor NetworksDocument4 pagesA Survey On Data Collection Techniques in Wireless Sensor NetworksNajem IslamNo ratings yet
- Java/J2Ee Project Abstracts: (Big Data,)Document2 pagesJava/J2Ee Project Abstracts: (Big Data,)infinity InfinityNo ratings yet
- (IJCST-V4I4P29) :M Arthi, M JayashreeDocument12 pages(IJCST-V4I4P29) :M Arthi, M JayashreeEighthSenseGroupNo ratings yet
- HST - 0621-657Document7 pagesHST - 0621-657Dr.Nirmala M.BNo ratings yet
- A Hybrid Intrusion Detection System of Cluster-Based Wireless Sensor NetworksDocument6 pagesA Hybrid Intrusion Detection System of Cluster-Based Wireless Sensor NetworksBima Aulia FirmandaniNo ratings yet
- A Study On Supervised Machine Learning Algorithm To Improvise Intrusion Detection Systems For Mobile Ad Hoc NetworksDocument10 pagesA Study On Supervised Machine Learning Algorithm To Improvise Intrusion Detection Systems For Mobile Ad Hoc NetworksDilip KumarNo ratings yet
- Analysis of Intrusion Detection System For Cloud EnvironmentDocument4 pagesAnalysis of Intrusion Detection System For Cloud Environmenteditor_ijcatNo ratings yet
- Toward Energy EfficientDocument5 pagesToward Energy EfficientGanesha GaneshNo ratings yet
- Sensor fusion improves event detection in wireless sensor networksDocument9 pagesSensor fusion improves event detection in wireless sensor networksAshish BhardwajNo ratings yet
- Design of A WSN Platform For Long-Term Environmental Monitoring For Iot ApplicationsDocument5 pagesDesign of A WSN Platform For Long-Term Environmental Monitoring For Iot Applicationsvinoth1128No ratings yet
- Fault Diagnosis in Wireless Sensor Network Using BPNN - RIL ApproachDocument5 pagesFault Diagnosis in Wireless Sensor Network Using BPNN - RIL Approachsrnarayanan_slmNo ratings yet
- Multi Level Trust Calculation With Improved Ant Colony Optimization For Improving Quality of Service in Wireless Sensor NetworkDocument14 pagesMulti Level Trust Calculation With Improved Ant Colony Optimization For Improving Quality of Service in Wireless Sensor NetworkIAES IJAINo ratings yet
- Network Intrusion Detection Combined Hybrid Sampling With Deep Hierarchical NetworkDocument13 pagesNetwork Intrusion Detection Combined Hybrid Sampling With Deep Hierarchical Networkjahangir shaikhNo ratings yet
- Research ArticleDocument13 pagesResearch ArticleMuthuKumar RajendranNo ratings yet
- Group-based intrusion detection improves WSN securityDocument9 pagesGroup-based intrusion detection improves WSN securitysubhadeepsarkarybsNo ratings yet
- A System For Denial-of-Service Attack Detection Based On Multivariate Correlation AnalysisDocument10 pagesA System For Denial-of-Service Attack Detection Based On Multivariate Correlation AnalysisVignesh PeriyasamyNo ratings yet
- Convolutional Neural Network Based Intrusion Detection AlgorithmDocument5 pagesConvolutional Neural Network Based Intrusion Detection Algorithmfuushi97No ratings yet
- Hybrid Approach For Data Aggregation in WSN With Advance Security Protocol inDocument7 pagesHybrid Approach For Data Aggregation in WSN With Advance Security Protocol inrahul sharmaNo ratings yet
- Energy Efficient Cluster Head Selection To Enhance Network Connectivity For Wireless Sensor NetworkDocument5 pagesEnergy Efficient Cluster Head Selection To Enhance Network Connectivity For Wireless Sensor NetworkTiffany BryanNo ratings yet
- Clustering in Distributed Incremental Estimation in Wireless Sensor NetworksDocument25 pagesClustering in Distributed Incremental Estimation in Wireless Sensor Networksrakesh_balija1010No ratings yet
- IEEE_Conference_TemplaDocument4 pagesIEEE_Conference_TemplaAshlesha ShettyNo ratings yet
- Ijaret 10 06 066Document13 pagesIjaret 10 06 066IAEME PublicationNo ratings yet
- Jean de Dieu Et Al 2012 Energy Efficient Secure Path Algorithm For Wireless Sensor NetworksDocument11 pagesJean de Dieu Et Al 2012 Energy Efficient Secure Path Algorithm For Wireless Sensor NetworksEdwardNo ratings yet
- PROIDS: Probabilistic Data Structure Based Intrusion Detection SystemDocument13 pagesPROIDS: Probabilistic Data Structure Based Intrusion Detection SystemAditiNo ratings yet
- A Novel IoT Network Intrusion Detection Approach Based On Adaptive Particle Swarm Optimization Convolutional Neural NetworkDocument16 pagesA Novel IoT Network Intrusion Detection Approach Based On Adaptive Particle Swarm Optimization Convolutional Neural NetworkJames100% (1)
- HCCOM-S-24-00079Document25 pagesHCCOM-S-24-00079Rajanikanth AluvaluNo ratings yet
- Pca-Based Distributed Approach For Intrusion Detection in WsnsDocument20 pagesPca-Based Distributed Approach For Intrusion Detection in WsnsMicah MorrisNo ratings yet
- Research Article Network Intrusion Detection Based On Sparse Autoencoder and IGA-BP NetworkDocument11 pagesResearch Article Network Intrusion Detection Based On Sparse Autoencoder and IGA-BP NetworkRianti AgustinaNo ratings yet
- Fault Detection in Wireless Sensor Network Based On Deep Learning AlgorithmsDocument8 pagesFault Detection in Wireless Sensor Network Based On Deep Learning AlgorithmsAnanthi MehaaNo ratings yet
- Wireless Sensor Network Intrusion Detection System Based On MK-ELMDocument14 pagesWireless Sensor Network Intrusion Detection System Based On MK-ELMkishoreNo ratings yet
- Anomaly Detection Using Fuzzy Q-Learning Algorithm: Shahaboddin Shamshirband, Miss Laiha Mat KiahDocument24 pagesAnomaly Detection Using Fuzzy Q-Learning Algorithm: Shahaboddin Shamshirband, Miss Laiha Mat KiahMiguel QuirogaNo ratings yet
- Wireless NetworkDocument5 pagesWireless NetworkJournalNX - a Multidisciplinary Peer Reviewed JournalNo ratings yet
- Enhanced Three Tier Security Architecture For WSN Against Mobile Sink Replication Attacks Using Mutual Authentication SchemeDocument13 pagesEnhanced Three Tier Security Architecture For WSN Against Mobile Sink Replication Attacks Using Mutual Authentication SchemeJohn BergNo ratings yet
- Research Article: Improved Reliable Trust-Based and Energy-Efficient Data Aggregation For Wireless Sensor NetworksDocument11 pagesResearch Article: Improved Reliable Trust-Based and Energy-Efficient Data Aggregation For Wireless Sensor NetworksCHINNI404No ratings yet
- Communication BreakdownsDocument11 pagesCommunication BreakdownsSanyam JainNo ratings yet
- EVALUATING_MACHINE_LEARNING_ALGORITHMS_F-1Document6 pagesEVALUATING_MACHINE_LEARNING_ALGORITHMS_F-1keerthiksNo ratings yet
- Detection of Attacks in Wireless Networks Using Data Mining TechniquesDocument9 pagesDetection of Attacks in Wireless Networks Using Data Mining TechniquesIAEME PublicationNo ratings yet
- IEEE_Conference_TemplateDocument4 pagesIEEE_Conference_TemplateAshlesha ShettyNo ratings yet
- 1 s2.0 S0020025520308422 MainDocument20 pages1 s2.0 S0020025520308422 Mainjymcrusher42No ratings yet
- Energy-Efficient Secure Data Aggregation Framework (Esdaf) Protocol in Heterogeneous Wireless Sensor NetworksDocument10 pagesEnergy-Efficient Secure Data Aggregation Framework (Esdaf) Protocol in Heterogeneous Wireless Sensor Networksijire publicationNo ratings yet
- Wireless Sensor Networks Intrusion Detection Based On SMOTEandtheRandomForestAlgorithm PDFDocument15 pagesWireless Sensor Networks Intrusion Detection Based On SMOTEandtheRandomForestAlgorithm PDFjosephNo ratings yet
- Detection and Location of A Cyber Attack in An Active Distribution SystemDocument10 pagesDetection and Location of A Cyber Attack in An Active Distribution SystemInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Energy Efficient Hybrid Intrusion Detection System For Wireless Sensor NetworksDocument5 pagesEnergy Efficient Hybrid Intrusion Detection System For Wireless Sensor Networksram_rattleNo ratings yet
- An Ensemble Design of Intrusion Detection System For Handling Uncertainty Using Neutrosophic Logic ClassifierDocument9 pagesAn Ensemble Design of Intrusion Detection System For Handling Uncertainty Using Neutrosophic Logic ClassifierMia AmaliaNo ratings yet
- Artificial Neural Networks for Intrusion DetectionDocument5 pagesArtificial Neural Networks for Intrusion Detections.pawar.19914262No ratings yet
- Securing Multi-Path Routing Using Trust Management in Heterogeneous Wireless Sensor NetworkDocument32 pagesSecuring Multi-Path Routing Using Trust Management in Heterogeneous Wireless Sensor NetworkVaijayanthiNo ratings yet
- CmseDocument12 pagesCmseRizal Asnawi SihombingNo ratings yet
- Event Detection Services Using Data Service Middleware in Distributed Sensor NetworksDocument19 pagesEvent Detection Services Using Data Service Middleware in Distributed Sensor NetworksStan PlNo ratings yet
- Measurement: S. Lavanya, A. Prasanth, S. Jayachitra, A. ShenbagarajanDocument16 pagesMeasurement: S. Lavanya, A. Prasanth, S. Jayachitra, A. ShenbagarajanTomas JosephNo ratings yet
- Intrusion Detection in Wireless Sensor Networks With An Improved NSA Based On Space DivisionDocument21 pagesIntrusion Detection in Wireless Sensor Networks With An Improved NSA Based On Space DivisionkishoreNo ratings yet
- Uncertainty Theories and Multisensor Data FusionFrom EverandUncertainty Theories and Multisensor Data FusionAlain AppriouNo ratings yet
- Abap MaterialDocument3 pagesAbap Materialaishwarya waghNo ratings yet
- Analysis of Three Iot-Based Wireless Sensors For Environmental MonitoringDocument9 pagesAnalysis of Three Iot-Based Wireless Sensors For Environmental Monitoringaishwarya waghNo ratings yet
- AssignmentDocument1 pageAssignmentaishwarya waghNo ratings yet
- cách kết nối LCD 16x2 với vi điều khiển.Document3 pagescách kết nối LCD 16x2 với vi điều khiển.vansonhuongNo ratings yet
- Data-Flow Modeling (A Practical Introduction To HW/SW Codesign, P. Schaumont)Document25 pagesData-Flow Modeling (A Practical Introduction To HW/SW Codesign, P. Schaumont)aishwarya waghNo ratings yet
- KeyboardDocument16 pagesKeyboardaishwarya waghNo ratings yet
- Lossless In-Network Processing in Wsns For Domain-Specific Monitoring ApplicationsDocument10 pagesLossless In-Network Processing in Wsns For Domain-Specific Monitoring Applicationsaishwarya waghNo ratings yet
- SOC Hardware and Software DesignDocument2 pagesSOC Hardware and Software Designaishwarya waghNo ratings yet
- RCDocument175 pagesRCaishwarya waghNo ratings yet
- DocumentDocument13 pagesDocumentaishwarya waghNo ratings yet
- III. Ratioed Logic CircuitDocument1 pageIII. Ratioed Logic Circuitaishwarya waghNo ratings yet
- Ratioed Circuits: Weak Pull-Up and Strong Pull-Down NetworksDocument5 pagesRatioed Circuits: Weak Pull-Up and Strong Pull-Down Networksnrp_rahulNo ratings yet
- Embedded System Lifecycle ModelsDocument31 pagesEmbedded System Lifecycle Modelsaishwarya waghNo ratings yet
- Embedded Systems Design: A Unified Hardware/Software IntroductionDocument39 pagesEmbedded Systems Design: A Unified Hardware/Software Introductionnandan_asNo ratings yet
- FSM 1Document2 pagesFSM 1aishwarya wagh0% (1)
- Vivado Design SuiteDocument1 pageVivado Design Suiteaishwarya waghNo ratings yet
- Arduino Uno Board with 14 Digital Input/Output PinsDocument23 pagesArduino Uno Board with 14 Digital Input/Output Pinsaishwarya wagh100% (2)
- What Is A Pilot SurveyDocument2 pagesWhat Is A Pilot Surveyaishwarya waghNo ratings yet
- Arduino Uno Board with 14 Digital Input/Output PinsDocument23 pagesArduino Uno Board with 14 Digital Input/Output Pinsaishwarya wagh100% (2)
- Chronology of TLM Event in The PhilippinesDocument3 pagesChronology of TLM Event in The PhilippinesTheus LineusNo ratings yet
- Optimizing RMAN RecoveryDocument61 pagesOptimizing RMAN RecoveryVijay ParuchuriNo ratings yet
- Mars - Andrew D. Basiago - Letter To The Ngs - 12 12 08Document4 pagesMars - Andrew D. Basiago - Letter To The Ngs - 12 12 08Gavin SimmonsNo ratings yet
- Tugas BHS InggrisDocument2 pagesTugas BHS InggrisJust NestNo ratings yet
- Foreclosing Modifications - How Servicer Incentives Discourage Loan ModificationsDocument86 pagesForeclosing Modifications - How Servicer Incentives Discourage Loan ModificationsRicharnellia-RichieRichBattiest-CollinsNo ratings yet
- Gauge Invariance in Classical ElectrodynamicsDocument22 pagesGauge Invariance in Classical ElectrodynamicsArindam RoyNo ratings yet
- Indra NooyiDocument2 pagesIndra NooyiMohan VamsiNo ratings yet
- Tanada, Et Al. Vs Angara, Et Al., 272 SCRA 18, GR 118295 (May 2, 1997)Document3 pagesTanada, Et Al. Vs Angara, Et Al., 272 SCRA 18, GR 118295 (May 2, 1997)Lu CasNo ratings yet
- A Project Report On Market Research & Brand Activation: Submitted in Partial Fulfillment of The RequirementsDocument55 pagesA Project Report On Market Research & Brand Activation: Submitted in Partial Fulfillment of The Requirementskartik chauhan100% (1)
- ARIMA Models in Python Chapter3Document52 pagesARIMA Models in Python Chapter3FgpeqwNo ratings yet
- ChaseDream Business School Guide LBS - ZH-CN - enDocument27 pagesChaseDream Business School Guide LBS - ZH-CN - enRafael LimaNo ratings yet
- Matrix Software User ManuelDocument45 pagesMatrix Software User ManuelHema SantoshNo ratings yet
- Reactions of Hydrocarbons and HaloalkanesDocument6 pagesReactions of Hydrocarbons and HaloalkanesGwynethAdrienneLeighVillapandoNo ratings yet
- Void For Vagueness DoctrineDocument16 pagesVoid For Vagueness Doctrinefatima ramosNo ratings yet
- CSE Qualifications and PointersDocument9 pagesCSE Qualifications and PointersChristopher de LeonNo ratings yet
- 58 58 International Marketing Chapter WiseDocument126 pages58 58 International Marketing Chapter WiseNitish BhaskarNo ratings yet
- CS201 Midterm Solved MCQs With ReferenceDocument4 pagesCS201 Midterm Solved MCQs With Referencegenome companyNo ratings yet
- Living Water by David FeddesDocument44 pagesLiving Water by David FeddesBenjaminFigueroaNo ratings yet
- Dilo SpaDocument2 pagesDilo SpajosefNo ratings yet
- Chapter04 PDFDocument36 pagesChapter04 PDFBabuM ACC FIN ECONo ratings yet
- United States v. Calvin Antonio Spencer, 68 F.3d 462, 4th Cir. (1995)Document4 pagesUnited States v. Calvin Antonio Spencer, 68 F.3d 462, 4th Cir. (1995)Scribd Government DocsNo ratings yet
- Mathematics Course Alagappa UniversityDocument10 pagesMathematics Course Alagappa UniversityTirthajit SinhaNo ratings yet
- Phonology BibliogrDocument6 pagesPhonology BibliogrSnapeSnapeNo ratings yet
- Health Grade 9 1st QuarterDocument1 pageHealth Grade 9 1st QuarterCapila Ron100% (1)
- Climate and Urban FormDocument10 pagesClimate and Urban FormYunita RatihNo ratings yet
- Highly Effective College StudentsDocument8 pagesHighly Effective College StudentsPhoenix Kylix0% (1)
- Mod 1 1 Concepts of Everyday LeadershipDocument26 pagesMod 1 1 Concepts of Everyday LeadershipSaifuzzaman AntorNo ratings yet
- Transportasi Kelembagaan PengantarDocument26 pagesTransportasi Kelembagaan Pengantarade wiraNo ratings yet
- Homework Solutions For Chapter 8Document6 pagesHomework Solutions For Chapter 8api-234237296No ratings yet
- Eight Principles of Ethical Leadership in EducationDocument2 pagesEight Principles of Ethical Leadership in EducationKimberly Rose Nativo100% (1)