Professional Documents
Culture Documents
Communication Systems - Chap14 To 15
Uploaded by
Hansika RajapakshaOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Communication Systems - Chap14 To 15
Uploaded by
Hansika RajapakshaCopyright:
Available Formats
Chapter 21
Networking
and
Internetworking
Devices
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-1
Connecting Devices
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-2
Connecting Devices and the OSI Model
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-3
A Repeater in the OSI Model
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-4
A Repeater
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-5
Function of a Repeater
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-6
A Bridge in the OSI Model
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-7
A Bridge
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-8
Function of a Bridge
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-9
Multiport Bridge
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-10
A Router in the OSI Model
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-11
Routers in an Internet
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-12
A Gateway in the OSI Model
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-13
A Gateway
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-14
McGraw-Hill
Single-Protocol versus
Multiprotocol Router
The McGraw-Hill Companies, Inc., 2001
Figure 21-15
McGraw-Hill
Brouter
The McGraw-Hill Companies, Inc., 2001
Figure 21-16
Switch
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-17
Example of an Internet
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-18
McGraw-Hill
The Concept of Distance
Vector Routing
The McGraw-Hill Companies, Inc., 2001
Figure 21-19
Distance Vector Routing Table
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-20
Routing Table Distribution
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-21
Updating Routing Table for Router A
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-22
McGraw-Hill
Final Routing Tables
The McGraw-Hill Companies, Inc., 2001
Figure 21-23
McGraw-Hill
Example 21.1
The McGraw-Hill Companies, Inc., 2001
Figure 21-24
McGraw-Hill
Concept of Link State Routing
The McGraw-Hill Companies, Inc., 2001
Figure 21-25
Cost in Link State Routing
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-26
Link State Packet
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-27
Flooding of As LSP
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-28
Link State Database
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-29
Costs in the Dijkstra Algorithm
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-30, Part I
Shortest Path Calculation, Part I
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-30, Part II
Shortest Path Calculation, Part II
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-30, Part III
Shortest Path Calculation, Part III
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-30, Part IV
Shortest Path Calculation, Part IV
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-30, Part V
Shortest Path Calculation, Part V
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-30, Part VI
Shortest Path Calculation, Part VI
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-31, Part VII
Shortest Path Calculation, Part VII
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-31, Part I
Shortest Path Calculation, Part VIII
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-31, Part II
Shortest Path Calculation, Part IX
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-31, Part III
Shortest Path Calculation, Part X
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-31, Part IV
Shortest Path Calculation, Part XI
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-31, Part V
Shortest Path Calculation, Part XII
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-31, Part VI
Shortest Path Calculation, Part XIII
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 21-32
Routing Table for Router A
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Chapter 23
Upper
OSI
Layers
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-1
Session Layer Dialog
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-2
Session-to-Transport Layer Communication
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-3
Synchronization Points
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-4
SPDU
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-5
Presentation Layer Functions
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-6
Direct and Indirect Methods of Translation
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-7
Concept of Encryption and Decryption
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-8
Encryption/Decryption Methods
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-9
Monoalphabetic Substitution
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-10
Polyalphabetic Substitution
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-11
Transpositional Encryption
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-12
Encoding/Decoding
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-13
Permutation
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-14
Substitution
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-15
Product
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-16
Exclusive OR
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-17
Rotation
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-18
DES
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-19
McGraw-Hill
Subkey Generation in DES
The McGraw-Hill Companies, Inc., 2001
Figure 23-20
One of the 16
Steps in DES
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-21
Public Key Encryption
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-22
RSA
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-23
RSA Encryption and Decryption
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-24
Security of RSA
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-25
Signature Authentication
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-26
Data Compression Methods
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-27
Run-Length Encoding
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-28
MHS
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-29
Message Format in MHS
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-30
Virtual File Storage
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-31
Local Access
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-32
Remote Access
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
Figure 23-33
Virtual Terminal
McGraw-Hill
The McGraw-Hill Companies, Inc., 2001
You might also like
- BS EN 62305 and 61643 Series: BS EN 62305-1 General Principles BS EN 62305-2 Risk ManagementDocument1 pageBS EN 62305 and 61643 Series: BS EN 62305-1 General Principles BS EN 62305-2 Risk ManagementHansika RajapakshaNo ratings yet
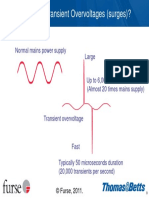
- What Are Transient Overvoltages (Surges) ?: Normal Mains Power Supply LargeDocument1 pageWhat Are Transient Overvoltages (Surges) ?: Normal Mains Power Supply LargeHansika RajapakshaNo ratings yet
- Lightning Characteristics: © Furse, 2011Document1 pageLightning Characteristics: © Furse, 2011Hansika RajapakshaNo ratings yet
- Section 443 - Simple Risk Assessment: © Furse, 2011Document1 pageSection 443 - Simple Risk Assessment: © Furse, 2011Hansika RajapakshaNo ratings yet
- © Furse, 2011Document1 page© Furse, 2011Hansika RajapakshaNo ratings yet
- 1 (17) PDFDocument1 page1 (17) PDFHansika RajapakshaNo ratings yet
- 1 (18)Document1 page1 (18)Hansika RajapakshaNo ratings yet
- © Furse, 2011Document1 page© Furse, 2011Hansika RajapakshaNo ratings yet
- © Furse, 2011Document1 page© Furse, 2011Hansika RajapakshaNo ratings yet
- Is Protection Required? - Section 443 / BS EN 62305: © Furse, 2011Document1 pageIs Protection Required? - Section 443 / BS EN 62305: © Furse, 2011Hansika RajapakshaNo ratings yet
- Section 443 - Simple Risk Assessment: © Furse, 2011Document1 pageSection 443 - Simple Risk Assessment: © Furse, 2011Hansika RajapakshaNo ratings yet
- © Furse, 2011Document1 page© Furse, 2011Hansika RajapakshaNo ratings yet
- Installation Effects - Parallel Protectors: © Furse, 2011Document1 pageInstallation Effects - Parallel Protectors: © Furse, 2011Hansika RajapakshaNo ratings yet
- Section 534 Key Areas - Selection of SPDS: © Furse, 2011Document1 pageSection 534 Key Areas - Selection of SPDS: © Furse, 2011Hansika RajapakshaNo ratings yet
- Questions & Answers: © Furse, 2011Document1 pageQuestions & Answers: © Furse, 2011Hansika RajapakshaNo ratings yet
- EF Pump Range 0.6-1.5 kW PerformanceDocument1 pageEF Pump Range 0.6-1.5 kW PerformanceHansika RajapakshaNo ratings yet
- Where To Protect: Through Both Underground and Overhead CablesDocument1 pageWhere To Protect: Through Both Underground and Overhead CablesHansika RajapakshaNo ratings yet
- SPD Installation: © Furse, 2011Document1 pageSPD Installation: © Furse, 2011Hansika RajapakshaNo ratings yet
- Pages - 4Document1 pagePages - 4Hansika RajapakshaNo ratings yet
- SPD Installation: © Furse, 2011Document1 pageSPD Installation: © Furse, 2011Hansika RajapakshaNo ratings yet
- Installation Effects - Parallel Protectors: © Furse, 2011Document1 pageInstallation Effects - Parallel Protectors: © Furse, 2011Hansika RajapakshaNo ratings yet
- Section 534 Key Areas - Selection of SPDS: © Furse, 2011Document1 pageSection 534 Key Areas - Selection of SPDS: © Furse, 2011Hansika RajapakshaNo ratings yet
- SPD Installation - Parallel Connection: © Furse, 2011Document1 pageSPD Installation - Parallel Connection: © Furse, 2011Hansika RajapakshaNo ratings yet
- GMH2 Produced WW Pumps TrainingDocument1 pageGMH2 Produced WW Pumps TrainingHansika RajapakshaNo ratings yet
- Section 534 Key Areas - Installation of SPDS: © Furse, 2011Document1 pageSection 534 Key Areas - Installation of SPDS: © Furse, 2011Hansika RajapakshaNo ratings yet
- EF Pump Range 0.6 - 1.5 KWDocument1 pageEF Pump Range 0.6 - 1.5 KWHansika RajapakshaNo ratings yet
- Section 534 Key Areas - Selection of SPDS: © Furse, 2011Document1 pageSection 534 Key Areas - Selection of SPDS: © Furse, 2011Hansika RajapakshaNo ratings yet
- EF Pump Range 0.6 - 1.5 KWDocument1 pageEF Pump Range 0.6 - 1.5 KWHansika RajapakshaNo ratings yet
- DP Pump Range 0.9-2.6 kW PerformanceDocument1 pageDP Pump Range 0.9-2.6 kW PerformanceHansika RajapakshaNo ratings yet
- Pages - 4Document1 pagePages - 4Hansika RajapakshaNo ratings yet
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5783)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (890)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (72)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Flight 60T Turbine Operating ManualDocument128 pagesFlight 60T Turbine Operating Manualtravieso112No ratings yet
- Mandi Adamo Resume 1128Document1 pageMandi Adamo Resume 1128madamo272096No ratings yet
- B6 Industrial+Elbe2013-7lrDocument160 pagesB6 Industrial+Elbe2013-7lrhernan dueñasNo ratings yet
- OlxDocument23 pagesOlxPoonam Dimple Ruchwani0% (1)
- Invoice MobileDocument1 pageInvoice MobilePrakash ShuklaNo ratings yet
- Doosan Retrofit ServiceDocument99 pagesDoosan Retrofit Servicestopless_dalian685No ratings yet
- Clerk Cum Data Entry Operator Recruitment 2018Document25 pagesClerk Cum Data Entry Operator Recruitment 2018Pankaj VermaNo ratings yet
- Documents - MX DPV Vertical Multistage Pumps 60 HZ Technical Data DP PumpsDocument80 pagesDocuments - MX DPV Vertical Multistage Pumps 60 HZ Technical Data DP PumpsAnonymous ItzBhUGoi100% (1)
- (X) Selection Guide - PowerFlex Low Voltage Drives - PFLEX-SG002K-En-P - February 2017Document178 pages(X) Selection Guide - PowerFlex Low Voltage Drives - PFLEX-SG002K-En-P - February 2017Nicolás A. SelvaggioNo ratings yet
- 2012 Product CatalogDocument407 pages2012 Product CatalogSe SamnangNo ratings yet
- PDFDocument76 pagesPDFRavishankarNo ratings yet
- Drilling Industry Glossary TermsDocument25 pagesDrilling Industry Glossary Termsahoua100% (1)
- Summer Internship Application for Accounting MajorDocument1 pageSummer Internship Application for Accounting MajorMohammad Jibran ChangiNo ratings yet
- Hammer MillDocument4 pagesHammer MillAnil Kumar KnNo ratings yet
- SF - Domestic Water PipingDocument16 pagesSF - Domestic Water PipingJahat AtencioNo ratings yet
- Contacts From MotorolaDocument26 pagesContacts From MotorolamvayangcoNo ratings yet
- ADJUST FUEL TIMINGDocument3 pagesADJUST FUEL TIMINGSanjay MadakaNo ratings yet
- CDU Basic Engineering Design BasisDocument12 pagesCDU Basic Engineering Design BasisSampat100% (2)
- Locking and Unlocking of Automobile Engine Using RFID1Document19 pagesLocking and Unlocking of Automobile Engine Using RFID1Ravi AkkiNo ratings yet
- O10/011/O16/O20 Single Pressure Control: Installation DataDocument4 pagesO10/011/O16/O20 Single Pressure Control: Installation DataMichael MartinNo ratings yet
- Electric Loco Moti 00 NewtDocument232 pagesElectric Loco Moti 00 NewtNanu KaruniaNo ratings yet
- A - Buch PL120106Document84 pagesA - Buch PL120106Cristian Piñeros100% (1)
- Ciscenje Hadnjaka HyundaiDocument4 pagesCiscenje Hadnjaka HyundaiAjdin Herc AhmetovicNo ratings yet
- Production SchedulingDocument242 pagesProduction SchedulingClint Foster0% (2)
- Userspace Drivers in LinuxDocument4 pagesUserspace Drivers in LinuxJeffi Edward100% (1)
- Module 1 - Project InitiationDocument21 pagesModule 1 - Project InitiationDenmark WilsonNo ratings yet
- RICOH Streamline NX Guia de UsuarioDocument107 pagesRICOH Streamline NX Guia de UsuarioMaria Elena AvilaNo ratings yet
- PCI Journal July - August 2020Document120 pagesPCI Journal July - August 2020Farja_ZzzNo ratings yet
- Midterm Exam Summary For Data Communications PDFDocument9 pagesMidterm Exam Summary For Data Communications PDFKit Jason MonjeNo ratings yet
- Criteria DesandingDocument13 pagesCriteria Desandinglebrix100% (1)