Professional Documents
Culture Documents
Linux Audit Files To See Who Made Changes To A File
Uploaded by
koulis123Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Linux Audit Files To See Who Made Changes To A File
Uploaded by
koulis123Copyright:
Available Formats
Linux audit files to see who made changes to a file
ABOUT
FORUM
HOWTOS & FAQS
LOW GRAPHICS
SHELL SCRIPTS
Linux audit files to see who made changes to a file
by NIXCRAFT on MARCH 19, 20 0 7 4 8 COMME NT S L A S T UP DA T E D S EPT EM BER 7 , 2 0 0 7
in FILE S YSTEM , GNU/OPEN S OURCE , HOW T O
RSS/FEED
GET FREE LINUX TIPS
Sign up for our newsletter to get tutorials
you@example.com
Sign Up
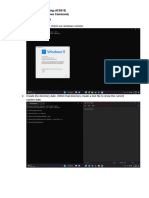
This is one of the key questions many new sys admin ask:
How do I audit file events such as read / write etc? How can I use audit to
see who changed a file in Linux?
The answer is to use 2.6 kernels audit system. Modern Linux kernel
(2.6.x) comes with auditd daemon. Its responsible for writing audit records
to the disk. During startup, the rules in /etc/audit.rules are read by this daemon. You can open
/etc/audit.rules file and make changes such as setup audit file log location and other option.
The default file is good enough to get started with auditd.
In order to use audit facility you need to use following utilities
=> auditctl - a command to assist controlling the kernels audit system. You can get status,
and add or delete rules into kernel audit system. Setting a watch on a file is accomplished
using this command:
=> ausearch - a command that can query the audit daemon logs based for events based on
different search criteria.
=> aureport - a tool that produces summary reports of the audit system logs.
nixCraft
! !
! !
Note that following all instructions are tested on CentOS 4.x and Fedora Core and RHEL 4/5
Linux.
Task: install audit package
The audit package contains the user space utilities for storing and searching the audit records
generate by the audit subsystem in the Linux 2.6 kernel. CentOS/Red Hat and Fedora core
includes audit rpm package. Use yum or up2date command to install package
# yum install audit
or
# up2date install audit
Auto start auditd service on boot
# ntsysv
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
nixCraft: 40.146 .nixCraft:
40.146 .
Linux audit files to see who made changes to a file
OR
# chkconfig auditd on
Now start service:
# /etc/init.d/auditd start
How do I set a watch on a file for auditing?
Let us say you would like to audit a /etc/passwd file. You need to type command as follows:
# auditctl -w /etc/passwd -p war -k password-file
Where,
-w /etc/passwd : Insert a watch for the file system object at given path i.e. watch file
called /etc/passwd
-p war : Set permissions filter for a file system watch. It can be r for read, w for write, x for
execute, a for append.
RELATED POSTS
How to keep a detailed audit trail of
whats being done on your Linux
systems
-k password-file : Set a filter key on a /etc/passwd file (watch). The password-file is a
filterkey (string of text that can be up to 31 bytes long). It can uniquely identify the audit
records produced by the watch. You need to use password-file string or phrase while
Uninstall files installed from a source
code tar-ball
searching audit logs.
In short you are monitoring (read as watching) a /etc/passwd file for anyone (including syscall)
that may perform a write, append or read operation on a file.
RHEL5: Linux Kernel kexec-tools bug
fix update
Wait for some time or as a normal user run command as follows:
$ grep 'something' /etc/passwd
$ vi /etc/passwd
Following are more examples:
Security Tip: Find out current working
directory of a process
Linux commands to help you navigate
File System audit rules
Add a watch on "/etc/shadow" with the arbitrary filterkey "shadow-file" that generates records
Red Hat / CentOS Linux 5.x: Perl
Performance Bug Fix Available
for "reads, writes, executes, and appends" on "shadow"
# auditctl -w /etc/shadow -k shadow-file -p rwxa
syscall audit rule
How to: Linux reset the permissions of
the installed rpm packages with
setperms option
The next rule suppresses auditing for mount syscall exits
# auditctl -a exit,never -S mount
How do I Drop or block attackers IP
with null routes?
File system audit rule
Add a watch "tmp" with a NULL filterkey that generates records "executes" on "/tmp" (good for
a webserver)
# auditctl -w /tmp -p e -k webserver-watch-tmp
syscall audit rule using pid
To see all syscalls made by a program called sshd (pid - 1005):
# auditctl -a entry,always -S all -F pid=1005
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
Linux Get List of Installed Software for
Reinstallation / Restore All the
Software Programs
Re-read The Partition Table Without
Rebooting Linux System
Linux audit files to see who made changes to a file
How do I find out who changed or accessed a file
/etc/passwd?
Use ausearch command as follows:
# ausearch -f /etc/passwd
LATEST LINUX/UNIX Q & A
Mac OS X: Terminal Download File Command
GPG Change Passphrase Secret Key Password
Command
Python: Get Todays Current Date and Time
Debian / Ubuntu: Install Duplicity For Encrypted
Backup In Cloud
Change Password Using passwd Command Over
SSH Based Session
OR
# ausearch -f /etc/passwd | less
OpenSSH Config File Examples
SSH Into Google Cloud Compute Engine Instance
Using Secure Shell Client
OR
# ausearch -f /etc/passwd -i | less
Ubuntu Linux LTS: Force Kernel Package Updates
Which Have Been Kept Back
Mac OS X: Set / Change $PATH Variable
HowTo: Find a Directory On Linux Based System
Where,
-f /etc/passwd : Only search for this file
-i : Interpret numeric entities into text. For example, uid is converted to account name.
Output:
Linux / Unix: Sort ls Command Output By Last
Modified Date and Time
OS X Mountain Lion 10.8 Set Apache and PHP
Web-Server
Clear Squid Proxy Cache And Re-create the
Cache Directories
HowTo: Pronounce Mac OS X
---type=PATH msg=audit(03/16/2007 14:52:59.985:55) : name=/etc/passwd flags=follow,open
inode=23087346 dev=08:02 mode=file,644 ouid=root ogid=root rdev=00:00
type=CWD msg=audit(03/16/2007 14:52:59.985:55) : cwd=/webroot/home/lighttpd
type=FS_INODE msg=audit(03/16/2007 14:52:59.985:55) : inode=23087346 inode_uid=root
inode_gid=root inode_dev=08:02 inode_rdev=00:00
type=FS_WATCH msg=audit(03/16/2007 14:52:59.985:55) : watch_inode=23087346
watch=passwd filterkey=password-file perm=read,write,append perm_mask=read
type=SYSCALL msg=audit(03/16/2007 14:52:59.985:55) : arch=x86_64 syscall=open
success=yes exit=3 a0=7fbffffcb4 a1=0 a2=2 a3=6171d0 items=1 pid=12551
auid=unknown(4294967295) uid=lighttpd gid=lighttpd euid=lighttpd suid=lighttpd
fsuid=lighttpd egid=lighttpd sgid=lighttpd fsgid=lighttpd comm=grep exe=/bin/grep
Let us try to understand output
audit(03/16/2007 14:52:59.985:55) : Audit log time
uid=lighttpd gid=lighttpd : User ids in numerical format. By passing -i option to
command you can convert most of numeric data to human readable format. In our example
user is lighttpd used grep command to open a file
exe="/bin/grep" : Command grep used to access /etc/passwd file
perm_mask=read : File was open for read operation
So from log files you can clearly see who read file using grep or made changes to a file using
vi/vim text editor. Log provides tons of other information. You need to read man pages and
documentation to understand raw log format.
Other useful examples
Search for events with date and time stamps. if the date is omitted, today is assumed. If the
time is omitted, now is assumed. Use 24 hour clock time rather than AM or PM to specify time.
An example date is 10/24/05. An example of time is 18:00:00.
# ausearch -ts today -k password-file
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
Fedora Linux: Restart / Stop / Start DHCPD Server
Command
Linux: Find Out What Is Using TCP Port 80
HowTo: OS X Take a Screenshot On My Mac
Desktop
CentOS / RHEL: Install KornShell (KSH)
Linux / Unix: Shell Script Find Out In Which
Directory Script File Resides
Bash: Display Web Page Content In Terminal
Linux audit files to see who made changes to a file
# ausearch -ts 3/12/07 -k password-file
Search for an event matching the given executable name using -x option. For example find out
who has accessed /etc/passwd using rm command:
# ausearch -ts today -k password-file -x rm
# ausearch -ts 3/12/07 -k password-file -x rm
Search for an event with the given user name (UID). For example find out if user vivek (uid
506) try to open /etc/passwd:
# ausearch -ts today -k password-file -x rm -ui 506
# ausearch -k password-file -ui 506
Other auditing related posts
How to keep a detailed audit trail of whats being done on your Linux systems
How do I find out Linux CPU utilization?
Linux Setting processor affinity for a certain task or process
Further readings
Read man pages - auditd, ausearch, auditctl
Updated for accuracy.
Cosmote
www.cosmote.gr
HTC online Cosmote!
Tweet
44
11
308
If you would like to be kept up to date with our posts, you can follow us on Twitter,
Facebook, Google+, or even by subscribing to our RSS Feed.
Featured Articles:
30 Handy Bash Shell Aliases For Linux / Unix / Mac OS X
Top 30 Nmap Command Examples For Sys/Network Admins
25 PHP Security Best Practices For Sys Admins
20 Linux System Monitoring Tools Every SysAdmin Should Know
20 Linux Server Hardening Security Tips
Linux: 20 Iptables Examples For New SysAdmins
Top 20 OpenSSH Server Best Security Practices
Top 20 Nginx WebServer Best Security Practices
20 Examples: Make Sure Unix / Linux Configuration Files Are Free From Syntax Errors
15 Greatest Open Source Terminal Applications Of 2012
My 10 UNIX Command Line Mistakes
Top 10 Open Source Web-Based Project Management Software
Top 5 Email Client For Linux, Mac OS X, and Windows Users
The Novice Guide To Buying A Linux Laptop
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
Linux audit files to see who made changes to a file
{ 48 comments read them below or add one }
James Musil
March 21, 2007 at 3:42 pm
In the line auditctl -w /etc/passwd -k shadow-file -p rwxa you mean /etc/shadow not
/etc/passwd.
REPLY
nixCraft
March 21, 2007 at 4:41 pm
James,
Thanks for heads up, post has been updated.
REPLY
GH Snijders
March 22, 2007 at 8:12 am
Very interesting article, thanks alot.
I did spot one small detail, though:
So from log files you can clearly see who made changes to a file using grep commands.
Grep is a tool to *read* files, not change them ;)
REPLY
nixCraft
March 22, 2007 at 8:29 am
GH,
Heh I was suppose to use vim as an example but somehow I did pickup grep. Anyway post
has been updated
Appreciate your post.
REPLY
Rodrigo
March 27, 2007 at 8:32 pm
Question, i need a file monitor to tell me which files are being used on a few folders, can i
use auditd? is it compatible with Redhat 7.3? is there a GUI to use with this?
If this is not what i need.. can you point me to what i need or something close?
REPLY
nixCraft
March 28, 2007 at 5:54 am
Rodrigo,
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
Linux audit files to see who made changes to a file
RH 7.3 does not support auditd; also a big security risk for such old disro.
Get Cent OS 4.x or FC 6/7
REPLY
Rodrigo
March 28, 2007 at 11:29 am
Sadly the box running RH 7.3 is a live production box for a multinational company, I cant just
get a new OS installed on that server, we will be at least another 6 months before migrating
to a new system.
Do you perhaps have an idea of what tool I could use to monitor files in a folder that have
been accessed during a period of time?
BTW great site.
REPLY
motumboe
March 30, 2007 at 7:22 am
Found this article following this link: http://beranger.org/index.php?article=2722
Two great blogs, my comps
:-)
REPLY
nixCraft
March 30, 2007 at 5:26 pm
@motumboe, thanks for feedback :D
@Rodrigo you can write your own perl scripts
REPLY
Ken
September 6, 2007 at 10:40 pm
10
When I try to set up a file watch, it fails. When I do an auditctl -l, i get this at the bottom:
File system watches not supported
Any ideas on whats wrong?
(btw, Im guessing that I can get around this by tracing syscalls based on the files inode
numbers, but thats messy, and hard to maintain)
REPLY
tiger74
January 25, 2008 at 2:23 am
@nixcraft,
Thank you for such a great article.
But, Im confused, it seems that there is no man page for the audit.rules?
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
11
Linux audit files to see who made changes to a file
@rodrigo,
You can use tripwire with similar function. It detects file changes.
REPLY
ike
April 27, 2008 at 7:49 pm
12
:-) Wow. This is great article.
REPLY
Ken
May 22, 2008 at 11:11 am
13
I got the same error:
File system watches not supported
Did you ever resolve this?
Thanks John
REPLY
Nguyen Dang
December 14, 2008 at 12:50 am
14
Hi, thanks for the article.
How do I redirect auditd to not generate log message but call a user-defined program (for an
selected event)? Is it possible?
Thank you very much.
REPLY
Relay
February 11, 2009 at 7:03 pm
15
In the description for the -p option, a is for attribute, not append the man page has a full
explaination.
-p war : Set permissions filter for a file system watch. It can be r for read, w for write, x for
execute, a for append.
REPLY
John Doe
April 3, 2012 at 12:51 am
Newer versions seem to use a for attribute changes, my manpage reads like this:
-p [r|w|x|a]
Set permissions filter for a file system watch. r=read, w=write, x=execute, a=attribute
change.
Nice article though, exactly what i needed. :)
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
16
Linux audit files to see who made changes to a file
REPLY
john
May 9, 2009 at 12:09 pm
17
Great article. Ive checked the man pages and am still left with two questions:
1. It doesnt appear that the options to the p switch allow for logging file deletions? How do
we log when a file is deleted?
2. The kernel does not allow us set a watch on the / directory. If I wanted to log all file
deletions, would I be best served by setting watches on all my top level directories
(bin,boot,dev,etc)?
Thanks again for the great resource!
- John
REPLY
J.C. Denton
July 3, 2009 at 3:44 pm
18
After a system restart or a manual one (sudo /etc/init.d/auditd restart) all my file monitoring is
gone. sudo auditctl -l says no rules then. do I have to save the rules to a textfile or
something? Please help (using (X)ubuntu 8.04 LTS)! ;-)
REPLY
Frans
July 20, 2009 at 6:40 am
19
Is this also working on Vmware ESX server 3.5? Because this is a modified RedHat
distrobution.
REPLY
Stef
November 12, 2009 at 9:28 am
20
Hi,
thanks for this article. Helps me a lot!
regards
REPLY
sushil
December 18, 2009 at 5:15 pm
21
hello,
good article..
REPLY
asdasdsd
December 22, 2009 at 1:23 pm
# /etc/init.d/audit start
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
22
Linux audit files to see who made changes to a file
# auditctl -w /etc/passwd -p war -k _etc_passwd
# auditctl -w /etc/shadow -k etc_shadow -p rwxa
# vipw (make a change)
# ausearch -f etc_passwd
Not a lot of use this idea :(
REPLY
asdasdsd
December 22, 2009 at 1:25 pm
23
/edit:
# ausearch -f etc_passwd
\
Had to escape the greater and less than sign because this comments section thought that it
was some HTML!
REPLY
Anonymous
July 5, 2010 at 9:04 pm
24
is it possible to use it from NIS.. we use ypcat
REPLY
Jagadeesh
July 9, 2010 at 5:07 am
25
Hi,
This is very nice article. In my company we have NFS mounted home directories. Anyone
can access files from anybodys home. This will help me monitoring who comes to my home
:-)
Thanks for this article
REPLY
Hello1971
July 14, 2010 at 2:03 am
26
Hi, Did this work on exported directory. I mean, if any one read/write a file through NFS, The
audit system will log them??
REPLY
nima0102
September 21, 2010 at 1:51 pm
27
Good Article :):)
REPLY
Dave Marcus
October 7, 2010 at 9:07 pm
Is there anyway to place an audit on a directory? And yes its a very good article, I have it
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
28
Linux audit files to see who made changes to a file
bookmarked.
REPLY
Yzhar
November 11, 2010 at 10:27 am
29
Im a Varins inc eng that had research this stuff for a while.
Unix (any), lacks such abilities and the best it can do is audit pre define objects.
scale is poor and some file operations are missing.
We have successfully build such framework (for about any unix platforms).
it is running on hundreds production sites for 3 years now. and I can tell you it wasnt
easy.
I dont want to sound like a sales man (Im not), but hope I can save you some time if
you are looking for such solution.
btw,
very nice article.
REPLY
Aldian
November 22, 2010 at 10:34 am
30
You forgot to explain how to stop monitoring once not needed anymore
REPLY
Sandy
December 12, 2010 at 7:42 pm
31
Does auditd work over NFS ? . I mean, if any one read/write a file through NFS, The audit
system will log them?? I have not been able to configure this. auditd captures read/write
access from FTP and even CIFS but not from NFS ? Anyone has any Clue ?
REPLY
Prashant
October 17, 2011 at 5:48 am
32
Hi Sandy,
Were you about to get the answer for your query..
As even I want to get statistics on NFS / CIFS / FTP etc..
please let me know if you got any tips !
thnx
Prashant
REPLY
Roumen Semov
December 16, 2010 at 12:39 am
Hmmm, appending text to a watched file does not show up in the audit logs:
echo hello world >> /etc/passwd
Any idea why?
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
33
Linux audit files to see who made changes to a file
REPLY
RG
May 27, 2011 at 5:00 am
34
You might need to turn auditing on by changing the default yes to no
at the bottom of the file /etc/sysconfig/auditd:
# This option disables syscall auditing by default. This can also be
# accomplished by auditctl -e.
AUDITD_DISABLE_CONTEXTS=no
Set to no for full audit functionality including file and directory watches and system call
auditing.
REPLY
DarenTay
February 25, 2011 at 8:04 am
35
If a user su to root, how do we manage that? Can we identify whos the original user?
REPLY
joe
March 21, 2011 at 5:43 pm
36
Daren Tay
For SU install sudo and which uses su log.
REPLY
Cristian Rusu
April 27, 2011 at 7:52 am
37
Hello
Is there any way to figure out what php script modified a file on the system?
I got a bug where all the images in some folders are converted to an black empty png and I
cant figure out what does this for months.
Thank you for any hint
Cris
REPLY
David
May 23, 2011 at 9:35 pm
38
Id change the permissions on the PNG files to read-only possibly by changing the
extended attributes if necessary and see what breaks. Might have to change the
directory permissions if the mysterious program is actually creating a new file and moving
deleting the old one as these steps dont require file permissions, just directory
permissions.
REPLY
Tha_Duck
May 26, 2011 at 11:38 am
# auditctl -w /tmp -p e -k webserver-watch-tmp
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
39
Linux audit files to see who made changes to a file
Shouldnt that be:
# auditctl -w /tmp -p x -k webserver-watch-tmp
?
REPLY
dreamingkat
July 9, 2011 at 8:10 am
40
according to the man page, a isnt for append, its for attribute changes.
REPLY
Funutation
October 13, 2011 at 5:45 pm
41
anyone know whether SELinux includes these features? I assume that it does, and does
even more but I cannot find details (easily :-)
thanx
REPLY
ceooph
November 21, 2011 at 9:15 am
42
Hi,
Thanks for this article and your whole site. I have a problem with auditd.
Can you audit a directory (yes) and all subdirectory ??
I want to audit a complete map point with folder, sub-folder, sub-sub-folder,
Thanks a lot for your help
REPLY
John Gonzalez
November 29, 2011 at 11:55 pm
43
Thank You!!!
REPLY
ritesh
June 4, 2012 at 11:46 am
44
HI,
I configured samba as a file server. Server is running successfully. I wanted to see logs
which user currently accessing a file and which file got deleted from user.
Is this possible in samba ?
Thanks in advacne.
Ritesh
REPLY
thomas
October 19, 2012 at 3:26 am
i have set up my audit.rules file.
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
45
Linux audit files to see who made changes to a file
when i start auditd, i get an output stating:
the audit system is in immutable mode. no audit rules loaded.
when i type auditctl -l it says no rules loaded.
i thought when i set up my audit.rules file and started auditd, thats all i had to do. after
reading this article, i believe there is more i need to do.
can someone elaborate on how the audit.rules file comes into play?
REPLY
ibeam7
November 28, 2012 at 11:20 pm
46
thomas
Check to see if you have
-e 2
at the end of your audit.rules file. If so, once you reload or restart your auditd service you
will not be able to modify your rules file without bouncing the server. If doing testing, its
best to use
-e 1
which just enables the rules but doesnt lock them.
REPLY
Kirk
March 26, 2013 at 11:14 pm
47
Is it possible to write rules to detect modifications to any file in /var/www with the name
settings.php? This doesnt work, but it captures what Id like to be able to do:
auditctl -w /var/www/vhosts/*/settings.php -k config-watch -prwa
Thanks.
REPLY
Sarfraz
September 2, 2013 at 12:27 pm
Do we enable file auditing for files accessed from SFTP like winscp tool?
REPLY
Leave a Comment
Name *
E-mail *
Website
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
48
Linux audit files to see who made changes to a file
You can use these H T M L tags and attributes for your code and commands: <strong> <em> <ol> <li> <u> <ul> <blockquote> <pre>
<a href="" title="">
Notify me of followup comments via e-mail.
Submit
Tagged as: audit daemon, audit package, audit records, audit system, auditctl command, ausearch command,
grep command, rhel, Sys admin, trace syscall, yum command
PREVIOUS POST:
Howto install & use Flash, Java, Real Player 32 bit plugins under 64 bit
Firefox
NEXT POST:
How to edit video on a Linux Desktop system
2004-2013 nixCraft. All rights reserved. Cannot be reproduced without written permission.
Privacy Policy | Terms of Service | Questions or Comments | Copyright Info | Sitemap
http://www.cyberciti.biz/tips/linux-audit-files-to-see-who-made-changes-to-a-file.html[5/11/2013 1:58:18 ]
You might also like
- Steps To Install LAMP in A Offline Centos MachineDocument16 pagesSteps To Install LAMP in A Offline Centos MachineRed IeNo ratings yet
- Linux System Administrator Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesFrom EverandLinux System Administrator Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesNo ratings yet
- CS333 OS Lab06 BSCS5CDocument5 pagesCS333 OS Lab06 BSCS5CMuhammad ZohaibNo ratings yet
- Auditing Solaris Security With CLI: Gathering Background InformationDocument7 pagesAuditing Solaris Security With CLI: Gathering Background Informationronaldo_ronaldo100% (1)
- Cert Intrusion Detection ChecklistDocument4 pagesCert Intrusion Detection Checklistthelibrarian0% (1)
- Linprivesc - PuckieStyleDocument26 pagesLinprivesc - PuckieStylepeterndindi41No ratings yet
- Red Hat Certified System Administrator Study GuideDocument15 pagesRed Hat Certified System Administrator Study GuideJason SmithNo ratings yet
- How To Find Anything Under Linux: Find Largest or Newest FilesDocument4 pagesHow To Find Anything Under Linux: Find Largest or Newest FilesMani KandanNo ratings yet
- System Admin Unit1 & Unit2Document112 pagesSystem Admin Unit1 & Unit2Shivansh JoshiNo ratings yet
- Linux Network Administration Chapter 3Document11 pagesLinux Network Administration Chapter 3Memoh Clinton55No ratings yet
- Lsa QB AnsDocument55 pagesLsa QB AnsGaurav bansodeNo ratings yet
- Kashif AliDocument13 pagesKashif AliAshwaq ShaikNo ratings yet
- Linux PersistanceDocument5 pagesLinux Persistanceroman16kovNo ratings yet
- Linux Scenario Based Interviews QuestionsDocument19 pagesLinux Scenario Based Interviews QuestionsjosephNo ratings yet
- Technical Test. System Support Analyst SeniorDocument4 pagesTechnical Test. System Support Analyst SeniorJuan JuanNo ratings yet
- 20 Linux Server Hardening Security TipsDocument12 pages20 Linux Server Hardening Security TipsEva TumwesigyeNo ratings yet
- Red Hat Certified System Administrator (EX200) - RHCSA Exam Prep PDF - 1595884353Document87 pagesRed Hat Certified System Administrator (EX200) - RHCSA Exam Prep PDF - 1595884353Ricardo SanchezNo ratings yet
- 20 Linux Server Hardening Security Tips - NixCraftDocument28 pages20 Linux Server Hardening Security Tips - NixCraftngocn198No ratings yet
- Linux Config Syntax CheckDocument4 pagesLinux Config Syntax CheckKrishna ForuNo ratings yet
- Basic Linux Commands From A+Document30 pagesBasic Linux Commands From A+Juan MedinaNo ratings yet
- Linux CommandDocument8 pagesLinux CommandShakhawatHossainShoyebNo ratings yet
- Basic Linux CMDocument5 pagesBasic Linux CMTcp VnNo ratings yet
- 50 Most Frequently Used Linux Commands PDFDocument58 pages50 Most Frequently Used Linux Commands PDFTunas Andiranto100% (2)
- FilePermissionsCommands UnixDocument25 pagesFilePermissionsCommands Unixshubhamraj201718No ratings yet
- Homework No. 3: Course Code: Cap423Document11 pagesHomework No. 3: Course Code: Cap423Mannu KhairaNo ratings yet
- 40 Linux Server Hardening Security TipsDocument18 pages40 Linux Server Hardening Security TipsMazanaNo ratings yet
- Log Files: Log Files Are Files That Contain Messages About The System, Including The KernelDocument21 pagesLog Files: Log Files Are Files That Contain Messages About The System, Including The KernelSougata Roy ChowdhuryNo ratings yet
- Chapter - 6: Linux File System StructureDocument38 pagesChapter - 6: Linux File System Structureak.microsoft20056613No ratings yet
- Weebly ExplainedDocument6 pagesWeebly ExplainedrezoltNo ratings yet
- Linux Interview Questions & AnswersDocument87 pagesLinux Interview Questions & AnswersSri ShailamNo ratings yet
- Mastering Unix Shell Scripting: Bash, Bourne, and Korn Shell Scripting for Programmers, System Administrators, and UNIX GurusFrom EverandMastering Unix Shell Scripting: Bash, Bourne, and Korn Shell Scripting for Programmers, System Administrators, and UNIX GurusRating: 3.5 out of 5 stars3.5/5 (2)
- Crossbeam Firewalls 0Document4 pagesCrossbeam Firewalls 0Atul ChauhanNo ratings yet
- Commands/: Get The Description For A CommandDocument15 pagesCommands/: Get The Description For A CommandGegham MovsesNo ratings yet
- Evaluation of Some Windows and Linux Intrusion Detection ToolsFrom EverandEvaluation of Some Windows and Linux Intrusion Detection ToolsNo ratings yet
- Abusing SUID BinariesDocument25 pagesAbusing SUID Binariesrayd.testingNo ratings yet
- WP RedHat 7tips PDocument6 pagesWP RedHat 7tips PcompuwizsolNo ratings yet
- Evaluation of Some Intrusion Detection and Vulnerability Assessment ToolsFrom EverandEvaluation of Some Intrusion Detection and Vulnerability Assessment ToolsNo ratings yet
- Linux Interview1Document2 pagesLinux Interview1BharathNo ratings yet
- © 2018 Caendra Inc. - Hera For Ptpv5 - Linux Exploitation (Local Enumeration)Document11 pages© 2018 Caendra Inc. - Hera For Ptpv5 - Linux Exploitation (Local Enumeration)Saw GyiNo ratings yet
- Intrusion Discovery Linux Cheat SheetDocument2 pagesIntrusion Discovery Linux Cheat SheetRaquel WaitforitNo ratings yet
- 20 Linux Server Hardening Security TipsDocument25 pages20 Linux Server Hardening Security TipsIla IlanNo ratings yet
- AIX User and Group AdministrationDocument16 pagesAIX User and Group AdministrationsatNo ratings yet
- GCC Lab ManualDocument61 pagesGCC Lab ManualMadhu BalaNo ratings yet
- Linux Commands To Manage Local AccountsDocument25 pagesLinux Commands To Manage Local AccountsgshreyaNo ratings yet
- Linux Interview Questions Part4Document3 pagesLinux Interview Questions Part4BharathNo ratings yet
- Free Open Source Linux OS For Data Recovery & Data Rescue Bilingual Version UltimateFrom EverandFree Open Source Linux OS For Data Recovery & Data Rescue Bilingual Version UltimateNo ratings yet
- Linux Commands 3Document52 pagesLinux Commands 3Rakesh RakeeNo ratings yet
- Linux Command AssignmentDocument3 pagesLinux Command AssignmentHannieeeNo ratings yet
- C What Is The Booting Process of Linux Systen and Explain It, Is The First Process Comes UnderDocument18 pagesC What Is The Booting Process of Linux Systen and Explain It, Is The First Process Comes UndershekharNo ratings yet
- Common Linux Ubuntu Commands OverviewDocument40 pagesCommon Linux Ubuntu Commands OverviewMuhammad ZaineNo ratings yet
- Devops FilesDocument9 pagesDevops Filessweetha sweethaNo ratings yet
- Basic Red Hat LinuxDocument5 pagesBasic Red Hat LinuxjohnsonkumaraNo ratings yet
- Understand Filesystem) .: D. KernelDocument10 pagesUnderstand Filesystem) .: D. KernelMishraa_jiNo ratings yet
- Module 1 Ethical HackingDocument13 pagesModule 1 Ethical HackingApurva KeskarNo ratings yet
- Secure Machine Translate)Document24 pagesSecure Machine Translate)nvphucvnNo ratings yet
- Workshop 8Document7 pagesWorkshop 8firstlastfzsv3No ratings yet
- Starbucks SWOT Analysis 2014Document13 pagesStarbucks SWOT Analysis 2014koulis1230% (1)
- Create A Bootable Ubuntu USB Flash Drive The Easy Way - How-To GeekDocument8 pagesCreate A Bootable Ubuntu USB Flash Drive The Easy Way - How-To Geekkoulis123No ratings yet
- Starbucks SWOT Analysis 2014Document13 pagesStarbucks SWOT Analysis 2014koulis1230% (1)
- Starbucks SWOT Analysis 2013Document13 pagesStarbucks SWOT Analysis 2013koulis123No ratings yet
- BeerDocument3 pagesBeerKoulis KoulidisNo ratings yet
- Elder Lister Dauvergne Progress in Development Studies FINAL Dec 2013Document15 pagesElder Lister Dauvergne Progress in Development Studies FINAL Dec 2013koulis123No ratings yet
- Attack Profiling For Ddos - ThesisDocument96 pagesAttack Profiling For Ddos - Thesiskoulis123No ratings yet
- State of The Coffee IndustryDocument5 pagesState of The Coffee Industrykoulis123No ratings yet
- Datamonitor Starbucks SWOT Analysis 2011Document13 pagesDatamonitor Starbucks SWOT Analysis 2011Koulis KoulidisNo ratings yet
- How To Extract RPM or DEB Packages - G-Loaded JournalDocument13 pagesHow To Extract RPM or DEB Packages - G-Loaded Journalkoulis123No ratings yet
- How Do I Remove or Hide Old Kernel Versions, To Clean Up The Boot MeDocument19 pagesHow Do I Remove or Hide Old Kernel Versions, To Clean Up The Boot Mekoulis123No ratings yet
- OpenVPN Configuration Step by Step - MikroTik WikiDocument27 pagesOpenVPN Configuration Step by Step - MikroTik Wikikoulis123No ratings yet
- Fuzzy Cognitive MapsDocument7 pagesFuzzy Cognitive Mapskoulis123No ratings yet
- Yg Ab Building FloodgatesDocument46 pagesYg Ab Building Floodgateskoulis123No ratings yet
- Manual IP Firewall NAT - MikroTik WikiDocument8 pagesManual IP Firewall NAT - MikroTik Wikikoulis123No ratings yet
- MikroTik RB750 - Basic Firewall & SecurityDocument21 pagesMikroTik RB750 - Basic Firewall & Securitykoulis123100% (1)
- NetworkPro On Quality of Service - MikroTik WikiDocument9 pagesNetworkPro On Quality of Service - MikroTik Wikikoulis123No ratings yet
- Basic Traffic Shaping Based On Layer-7 Protocols - MikroTik WikiDocument14 pagesBasic Traffic Shaping Based On Layer-7 Protocols - MikroTik Wikikoulis123No ratings yet
- Mikrotik 4 Wan Load BalanceDocument4 pagesMikrotik 4 Wan Load Balancekoulis123100% (1)
- Cpe 100 TransformationsDocument7 pagesCpe 100 TransformationsChristina Zara91% (23)
- Sample Paper Reading CpeDocument6 pagesSample Paper Reading Cpekoulis123No ratings yet
- LFS201 Labs - Solutions PDFDocument133 pagesLFS201 Labs - Solutions PDFHitesh Trivedi100% (3)
- UntitledDocument6 pagesUntitledReza Abdul AbdulNo ratings yet
- How To Install Myanmar Font On Ubuntu 910Document19 pagesHow To Install Myanmar Font On Ubuntu 910HRmyanmarNo ratings yet
- C6 - LAB - Access ControlDocument4 pagesC6 - LAB - Access ControlMinh NhựtNo ratings yet
- Description: Tags: Hostguideupdate100402Document141 pagesDescription: Tags: Hostguideupdate100402anon-516813No ratings yet
- CLF ALLDocument464 pagesCLF ALLphyzicsNo ratings yet
- Guia de Desinstalación de ODOO EN UBUNTUDocument3 pagesGuia de Desinstalación de ODOO EN UBUNTUjesusgom100% (1)
- Computational Chemistry On The Desktop PC: The Arrival of UNIXDocument9 pagesComputational Chemistry On The Desktop PC: The Arrival of UNIXswapnil kaleNo ratings yet
- Trần Thị Hồng Nhan - B2111940 - CT104H - Lab01 PDFDocument6 pagesTrần Thị Hồng Nhan - B2111940 - CT104H - Lab01 PDFnhan trầnNo ratings yet
- HackerDocument21 pagesHackerArun kumarNo ratings yet
- D1101651GC10 - Ag UNIX and Linux Essentials Activity GuideDocument110 pagesD1101651GC10 - Ag UNIX and Linux Essentials Activity Guidejohnroberts1354No ratings yet
- Compat LogDocument16 pagesCompat Logakif09102007No ratings yet
- Software DefinitionDocument19 pagesSoftware DefinitionShafiq Mohd NorNo ratings yet
- 11gR2 ASM DisksDocument64 pages11gR2 ASM DisksankurlibraNo ratings yet
- Linuxperftools 140820091946 Phpapp01Document85 pagesLinuxperftools 140820091946 Phpapp01tolosfineNo ratings yet
- Unit 5 MS DosDocument10 pagesUnit 5 MS DosTapan RanaNo ratings yet
- PM Debug InfoDocument82 pagesPM Debug InfoDarkzin ProNo ratings yet
- Install SnortDocument16 pagesInstall SnortnashirumNo ratings yet
- CENTOS 6 Getting Started With SuricataDocument4 pagesCENTOS 6 Getting Started With SuricatamingsetaoNo ratings yet
- 875-1940-10 Veritas NetBackUp PDFDocument52 pages875-1940-10 Veritas NetBackUp PDFaksmsaidNo ratings yet
- Eylenburg Operating System Timeline Family TreeDocument23 pagesEylenburg Operating System Timeline Family TreeumairNo ratings yet
- Midterm 1 - Attempt ReviewDocument21 pagesMidterm 1 - Attempt ReviewSon NguyenNo ratings yet
- Process in LinuxDocument17 pagesProcess in LinuxNelson LuzigaNo ratings yet
- Unix McqsDocument24 pagesUnix Mcqspalailalitha1No ratings yet
- NDMDocument5 pagesNDMSatish AgrawalNo ratings yet
- Log - Removing Snap From GNOME Completely - 2024-03-17 - 18.30hrsDocument4 pagesLog - Removing Snap From GNOME Completely - 2024-03-17 - 18.30hrsVelan ChandrasekarNo ratings yet
- Computer Forensics Final GradeDocument15 pagesComputer Forensics Final GradeNicasio AquinoNo ratings yet
- Logcat Home Fota Update LogDocument301 pagesLogcat Home Fota Update LogCristinel BadicNo ratings yet
- Report On LinuxDocument15 pagesReport On Linuxgangana nikhithreddyNo ratings yet
- Dynamic Modelling Tips and TricksDocument20 pagesDynamic Modelling Tips and TricksmkwendeNo ratings yet