Professional Documents
Culture Documents
Gate To The Net - Bridge To Terabithia For Geeks
Uploaded by
McCyberflyOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Gate To The Net - Bridge To Terabithia For Geeks
Uploaded by
McCyberflyCopyright:
Available Formats
Gate to the Net
(Bridge to Terabithia remake for IT Geeks)
by Tobey McCyberfly | cyberfly [at] email [dot] cz
Inspired by a drawing derived from a movie based on a book by its author with an amazing inner spring of fantasy.
It’s been two days since we had set out on this adventurous and dangerous journey to the Binary Kingdom and we
are slowly but unavoidably running out of supplies. How lucky we are to have met a good fairy just yesterday, who
generously increased our TCP keep-alive value by a few miliseconds. Without her, we wouldn’t be able to get over that
giant firewall rising ahead of us, set up as a fortification to discourage brave bits from attempting to reach the other
side.
And who are we, anyway? The bravest of all, bits of the legend, those who dare to avert the fate foretold them by
virtual Fates, who dare to face the most frightful and destructive traffic-control devices and intrusion prevention
systems in this whole enchanted world of networks. We are the chosen ones. Ones and zeros, to be precise.
Me, Zero of Freeland and my soul-mate companion, One of Free Province have decided to free all the Binarians,
slaves of the Dark Router, who have been, imprisoned, longing for freedom for ages. One is definitely the best bit I’ve
ever met in my life and with complete trust in her I know she’ll never let me down. We can do it. Together.
We are gently moving forward, through the unexplored world of the firewall vicinity. Having reached the Great Firewall
of China*, built with black magic along the large meadows we’ve crossed, I am carefully throwing a cross-over
network cable with a magic, standard uncompilant RJ-45 connector at the end, straight to the top of the firewall. It’s
hooked. Now we just need my uncanny little piece of code to temporarily disable it and get through. Success! We’re
in.
“Woow. I never knew it was so breath-takingly beautiful out here”, One is telling me and we are both staring into the
distance, enjoying the amazing view of this virtual private network. “Look at all those supernatural ciphers, those
unearthly packet frames and the vast encrypted land around us. Isn’t that beautiful, Zero?”
Indeed. On the other hand, we’re in for hitting on some evil private data, bit-eating monsters, ghostly lost packets or
malign password fields. “One, we have to watch out and quietly sneak to the wireless castle overthere.” - “Ait, let’s
use our built-in Wi-Fi aerials and take a shortcut to get there straight!” – “No, One. No shortcuts exist to places which
are worth reaching. Come on, let’s sneak around, through the digital valley and the forest by the castle.”
We are moving on. It’s getting more and more scary here, we can hear voices of ghost data transfers and sounds of
VoIP* chattering coming from the dark woods beside us. “Let’s run for a while Zero”, says One. I’m switching on the
fairy transceiver and relaying ourselves into an optical fiber. Now, this is what I call running fast. The flow of digital
data is floating past our bodies, lifting our parity check information in the air, filling us with energy and supporting our
feeling of breaking all the spells, including our foretold fates.
“Oh look, a river!”, I am announcing and slowing down before reaching it. “Cool, look at that enchanted coaxial cable
hanging down to the river’s bank! It’ll help us cross it.” We swung across the broadband corridor flooded with illegaly
shared multimedia to pass through another small forest of bewitched repeaters and switchers.
“Oh no! An evil password field is ahead of us!”, screams One, squeezing my hand in fear. “Fear not, my beloved!”, I
say, starting my portable version of Opera browser in the background. “We rule this network and nothing crushes
us !!!”, I’m calling out loud while waving Opera’s Wand* and successfully cracking the last obstacle on our way to the
castle.
We’re here. We’ve finally reached our destination MAC* address. And One is calling out: “Prisoners of the Dark
Router! We have come to free you! Show me that you hear us!!”
Encouraged by a loud reply of randomly generated beeps, we’re closing on the place of Binarians’ suffering and
crossing an overcrowded 10 Mbps bridge to the castle, preparing our dynamic liberty libraries or *.dll’s. Using a zero-
day vulnerability exploit*, we’re penetrating the main defence framework and quickly dragging them to a safe place in
the Freeland. Lucky us to have remembered enabling drag & drop in Freeland control panels before we left.
“Woot!”, all Binarian bits are shouting. “At last, we are all free. Thanks for saving us guys! Thanks a lot.”
Quickly checking the overall checksum hash to find out none of the bits are missing, we say goodbye and leave for
our original server room.
Heading back for our home server, I look at One smiling at me, to finally realize it…
She is the One I love and want to spend the rest of my expiration value with.
*Side notes:
Great Firewall of China = based on a real-world firewall banning censored websites out of Chinese web space
VoIP = voice over internet protocol, voice communication means
Opera Wand = Opera’s safe password manager
0-day vulnerability exploit = security-breaking script using freshly discovered vulnerabilities
For Leslie. 7}{e 3nD
You might also like
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5795)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (588)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (400)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (345)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (121)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Humber College, Wireless Telecommunication (North Campus) : Presented byDocument18 pagesHumber College, Wireless Telecommunication (North Campus) : Presented byharish sharmaNo ratings yet
- Zig Bee Wire Shark SnifferDocument15 pagesZig Bee Wire Shark SnifferOsman AteşNo ratings yet
- Cisco IOS PackagingDocument9 pagesCisco IOS PackagingjfwirrmannNo ratings yet
- McqsDocument71 pagesMcqsGaurav Khullar0% (1)
- Checkpoint Interview QuestionsDocument2 pagesCheckpoint Interview Questionssrivatsan_ece100% (3)
- STKT104X User's ManualDocument58 pagesSTKT104X User's ManualAshok BabuNo ratings yet
- Automated Malware Analysis Sans Fire 2009 2Document46 pagesAutomated Malware Analysis Sans Fire 2009 2jackivescNo ratings yet
- At Command ManualDocument38 pagesAt Command ManualOpulens KeyNo ratings yet
- Telkomsel: Aktivasi GPRS/MMS Lewat OTA / SMSDocument3 pagesTelkomsel: Aktivasi GPRS/MMS Lewat OTA / SMSwisnuy31No ratings yet
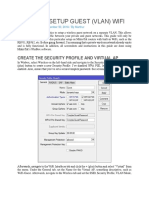
- Mikrotik Setup Guest (Vlan) WifiDocument12 pagesMikrotik Setup Guest (Vlan) WifiKhodor AkoumNo ratings yet
- Network Programming With GoDocument123 pagesNetwork Programming With GoTudor Luca100% (1)
- cn16 12Document85 pagescn16 12mufasNo ratings yet
- Anna University Civil Lateral (100404815001-28)Document18 pagesAnna University Civil Lateral (100404815001-28)pddsivaNo ratings yet
- Rotork - PakscanDocument2 pagesRotork - PakscanIglesia Adventista SILOÉNo ratings yet
- Practical No: 1 Aim:To Make and Test A Straight Through CableDocument39 pagesPractical No: 1 Aim:To Make and Test A Straight Through CablediveshNo ratings yet
- 4 Exploring Network QoSDocument8 pages4 Exploring Network QoSonlycisco.tkNo ratings yet
- LifestyleDocument37 pagesLifestyleVina Yabao LuchavezNo ratings yet
- Em Microelectronic: Appnote 411Document19 pagesEm Microelectronic: Appnote 411Renato Siqueira100% (8)
- Vicidial Multi-Server Manual by Poundteam v1 1Document25 pagesVicidial Multi-Server Manual by Poundteam v1 1Elyin Martinez0% (1)
- 10EC65 Operating Systems - Structure of Operating SystemsDocument37 pages10EC65 Operating Systems - Structure of Operating SystemsShrishail BhatNo ratings yet
- Srs For Online Examination Sys.Document6 pagesSrs For Online Examination Sys.Akshay SinghNo ratings yet
- Unit 4Document16 pagesUnit 4Senthilnathan SNo ratings yet
- Cisco UCS C220 M5 Server Installation and Service Guide: Americas HeadquartersDocument142 pagesCisco UCS C220 M5 Server Installation and Service Guide: Americas HeadquartersKazi Didar Hossain ShohanNo ratings yet
- McAfee KnowledgeBase - Ports Needed by ePO 4.0 and 4Document4 pagesMcAfee KnowledgeBase - Ports Needed by ePO 4.0 and 4Gopi GopinathNo ratings yet
- Quectel GSM BT Application Note V1.2Document48 pagesQuectel GSM BT Application Note V1.2MaiDungNo ratings yet
- Learnenglish Britishcouncil OrgDocument3 pagesLearnenglish Britishcouncil OrgDavid Lance MariminNo ratings yet
- GWT 2.3Document469 pagesGWT 2.3beatrix_boda_1No ratings yet
- IP-PDU User ManualDocument22 pagesIP-PDU User ManualWawanku WawankuNo ratings yet
- Communication Aided Protection SchemesDocument34 pagesCommunication Aided Protection Schemespvenky_kkdNo ratings yet