Professional Documents
Culture Documents
34 Multilevel
Uploaded by
Chittaranjan Baral0 ratings0% found this document useful (0 votes)
17 views7 pagesinitial thesis of the FHG states, that developments, systems and structures are results of social processes within a culture (HOFFMANN, 1997). In the context of the trend of globalisation, which is characterised by the restriction to financial performance, economic growth has become to an end in itself (WELFORD, 2001).
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this Documentinitial thesis of the FHG states, that developments, systems and structures are results of social processes within a culture (HOFFMANN, 1997). In the context of the trend of globalisation, which is characterised by the restriction to financial performance, economic growth has become to an end in itself (WELFORD, 2001).
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
17 views7 pages34 Multilevel
Uploaded by
Chittaranjan Baralinitial thesis of the FHG states, that developments, systems and structures are results of social processes within a culture (HOFFMANN, 1997). In the context of the trend of globalisation, which is characterised by the restriction to financial performance, economic growth has become to an end in itself (WELFORD, 2001).
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 7
ISSN (Print) : 2320 3765
ISSN (Online): 2278 8875
International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Vol. 2, I ssue 4, April 2013
Copyright to IJAREEIE www.ijareeie.com 1467
Multilevel Security System for Automotives
using RFID and Biometric Techniques in
LabVIEW
Priya Darshini.V
1
, Prasannabalaje S.M
2
, Prakash.R
3
, Rekha.V
4
,Vinodhini.R
5
, Sangeetha Monica.T
6
Assistant Professor, Dept. of ECE, Dr N.G.P Institute of Technology, Coimbatore, Tamil Nadu, India
1
B.E. Final Year Student, Dept. of ECE, Dr N.G.P Institute of Technology, Coimbatore, India
2, 3, 4, 5, 6
Abstract: Motor vehicle theft is a serious problem in many parts of the world. In India, the annual loss from the car
theft is over $4 billion. The Automotive Information Council (AIC) reports that over one million motor vehicles are
stolen in the country each year. That is one motor vehicle theft occurs for every 31 seconds. Hence it has become
essential to secure the automotive in this modern world. This proposed thesis aims at securing the automotive using the
technologies like Radio Frequency Identification (RFID) technology, thumb registration system and face recognition
which is efficient by nature.The operational modes in this project are classified as training mode, automatic mode and
manual mode .Initially the RFID system gets authenticated. The importance of this system is, it gets its verification
from the Road Transportation Office (RTO).This authentication leads to the thumb registration module by which the
efficiency of the thumb is enhanced using Pattern Matching Algorithm (PMA). Face recognition system is used after
the thumb registration. Then the system allows the user to drive the car. For emergency, a key insertion slot will be
placed in the system with the help of which the user can insert the key. During this emergency mode of operation the
camera captures the drivers image and sends it to the owners mobile as Multimedia Messaging Service (MMS). The
owner provides the password then the system allows the user to drive the vehicle. Global System for Mobile
communication (GSM) module is also kept inbuilt for tracking purpose. The software testing in this project is done
using LabVIEW. The timing and efficiency will be analyzed for both hardware and software based on which the
implementation will be done in future.
Keywords: Face Recognition, GSM Module, MMS Module, Radio Frequency Identification technology, Thumb
Registration.
I. INTRODUCTION
In todays world owing a car is not a big deal but safeguarding the owned car has become a great deal. Even though the
modern automobiles are heterogeneously combined by the combination of latest digital components it had also created
the opportunity for new attacks [1]. A recent statistical report by United States of America (USA) has stated that around
2800 vehicles are being stolen in an average for a day. While the automotive industry has always considered safety a
critical engineering concern, it is not logical whether the vehicle manufacturers have anticipated in their designs and the
possibility of an adversary. Compounding this issue, in order to resolve the attack over the automotives many security
systems such as car alarm, radar communication system and immobilizer perceptions are in existence. The current
prevailing security system has certain disadvantages by itself [2] .Hence it has become evident to develop a security
system to make an identity and monitor the security of an automotive.
II. OVERVIEW OF THE PROJECT
The ultimate aim of this project is to provide a hi-tech security to the automotive and preventing the unauthorized
persons from accessing it .The proposed system possess three modes of operations namely training mode, automatic
mode and the manual mode. In the training mode certain parameters of the driver such as name, license number,
employment ID, and blood groups are initially collected in the database for each individuals. The corresponding
persons thumb impressions in different textures will be trained using Pattern Matching Algorithm (PMA). Parallely the
facial image of the individual will also be put together and accumulated as a total database. In the automatic mode,
system will be verified with the RFID module based testing. Based on the result obtained, if matched with the above
criterion will be placed in the thumb registration system. The verification of this module leads to the face recognition in
which the faces of the current person will be compared with the training faces and the selection of the original image
will be done using the Principle Component Analysis (PCA) algorithm. Soon after the assessment the user will be
permitted to drive the vehicle.
ISSN (Print) : 2320 3765
ISSN (Online): 2278 8875
International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Vol. 2, I ssue 4, April 2013
Copyright to IJAREEIE www.ijareeie.com 1468
In case of emergency the key will be inserted in the key insertion slot after which the camera in the car takes the snap
of the person who drives the car .The snap shot will be messaged to the owner with the help of Multimedia Messaging
Service (MMS).The owner after providing the password makes the driver to drive the car.The path of the car will be
traced with the help of the Global Positioning System (GPS) module with the help of which the location of the car is
monitored and the car will also be stopped by providing the password to the system by the owner if required. All the
above mentioned technologies will be tested using the LabView software. Based on the results obtained from the
software, the design of hardware is done with the suitable components. The steps are taken to reduce the time delay
required to complete these modules successfully by the authenticated user.
III. LITERATURE REVIEW
Security systems nowadays have become a need for vehicles available with many modern features. This car security
system with extra access and intelligent alarming. This system will be accessed and configured by owner using
Bluetooth module communication via mobile phone to turn in on or off [3]. This system suggests that GSM based
security system are more stout then an ordinary security system .The ordinary systems are simply based on the concept
of sensors .They sound an alarm on detecting movement [4,5]. This system of technology has now lost its appeal as it
became a common sighting in meteors where these alarms go of unnecessarily. Due to the insecure environment the
ratio of the vehicle theft increases rapidly [6]. Because of this the manufactures of the automotive are taking some
serious steps for the protection of their valuable vehicles which includes activating alarms, steering wheel lock systems.
They ensure authorization for the owners and also inbuilt these anti-theft system to prevent car from theft [7].
Drawbacks
The automotive theft and the hijackings had been taken place by common ways of stealing cars .This is done by
deactivating the alarm or steering wheel lock by cutting wires, but the methods proposed in above surveys would also
sound ineffective [8]. The drawback of this system is, the results obtained from RADAR are not accurate. The
drawback of immobilizer concept was the software present in the system could be hacked easily.
IV. BLOCK DIAGRAM OF THE SYSTEM
The block diagram of the overall system is shown in the fig 1. It comprises of many modules such as RFID system,
Thumb Registration system, face recognition system as its main segments .It also includes different modules such as
GPS, Toggle switch for toggling purpose, and Retrieving switch along with the LED and LCD indication .All these
modules are supplied with power with the help of Power supply unit.
Fig 1.Block diagram of the system
ISSN (Print) : 2320 3765
ISSN (Online): 2278 8875
International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Vol. 2, I ssue 4, April 2013
Copyright to IJAREEIE www.ijareeie.com 1469
V. STRUCTURE OF RFID SYSTEMS
The modules that are required to design this system are as follows Voltage Maintainer circuit, Oscillator block,
Transistor-Transistor Logic (TTL), Encoder.Voltage Maintainer converts 5v to 3.3vusing IC-LM358 for maintaining at
the appropriate voltages [9]. These kinds of maintainers are preferred for baud rate at 2400 rates per second. The
Oscillator will be employed in order to avoid the ripple factor. They also use the filters to achieve resonant frequency
generated at the rate of 125 KHz at the baud rate of 2400.Helical type of antenna is employed in this paper. The
Transistor-Transistor Logic (TTL) uses up to convert 3.3v to 5v of power supply.Zener diode is used to regulate the
voltage. Common emitter configuration is carried out in TTL logic. The database of RFID system is shown in fig 2.
Fig 2. Database of the system
VI. THUMB REGISTRATION SYSTEM
Fingerprint Identification and Digital Certification and it is used in a wide range of embedded applications. It features
with the SEA/RSA accelerator engines, the embedded non-volatile memory (Flash/OTP), the fingerprint processing
accelerator and its algorithm firmware. Cordis 5+ is the 32-bit RISC core which is featured with 16-/32-bit ISA and
Harvard bus architecture. The Enhanced DSP instruction extensions and accelerators are supported by this core system.
In addition, a 5-stage pipeline is used to increase the amount of operational parallelism, giving the most performance
out of each clock cycle. It is competent for System on Chip (SOC) products targeted at consumer, networking,
automotive and other cost-sensitive markets. The image of synochipis shown in the fig 3.
Fig 3 Image of Synochip
The thumb impressions of different users are taken initially and stored.The database is chosen as such, the RFID of a
particular user has to get matched with the thumb impression. They are matched using the PMA.This algorithm was
used inbuilt in the embedded programming .The image of thumb impression for different users is shown in the fig 4.
ISSN (Print) : 2320 3765
ISSN (Online): 2278 8875
International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Vol. 2, I ssue 4, April 2013
Copyright to IJAREEIE www.ijareeie.com 1470
Fig 4 Database of finger print images
VII. IMPLEMENTATION OF MODULES
A. INTERFACE OF RF MODULE WITH DSPIC
The RF transmitter employs a SAW-stabilized oscillator, for ensuring accurate frequency control for best range
performance. It receives serial data and transmits it wirelessly through RF through its antenna. The bandwidth of RF
transmitter works on typical frequency of 12 Megahertz. The LCD is seized with the circuit to display the required
information. The interface of DSPIC with RF module is specified in the fig 5.
Fig 5. RF module interface with DSPIC controller
B.INTERFACE OF FINGER PRINT SENSOR WITH DSPIC
Fingerprints are the traces of an impression from the friction ridges of any part of a human or other primate
hand. The finger print sensor consists of a synochip which incorporates the various images of finger prints. It features
with the SEA/RSA accelerator engines, the embedded non-volatile memory (Flash/OTP), the fingerprint processing
accelerator and its algorithm firmware. Synochip works on typical frequency of 120 MHz .The DSPIC is interfaced
with the finger print sensor as shown in the fig6.
ISSN (Print) : 2320 3765
ISSN (Online): 2278 8875
International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Vol. 2, I ssue 4, April 2013
Copyright to IJAREEIE www.ijareeie.com 1471
Fig 6. Finger print sensor interface with DSPIC
VIII. RESULTS AND DISCUSSIONS
On following the above procedures and methodology hardware implementation as well as the software implementation
has been done. The software implementation is done withthe help of LabVIEW software. The fig 7.1shows the result of
the overall hardware implementation of RFID systems and thumb registration.
Fig 7.1 RFID authentication
The biometrics recognition has been implemented. This module testing has been executed with the help of LabVIEW
software. The analysis of the system is done with the help of Pattern Matching Algorithm (PMA).The fig 7.2 displays
the output of thumb authentication system.
ISSN (Print) : 2320 3765
ISSN (Online): 2278 8875
International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Vol. 2, I ssue 4, April 2013
Copyright to IJAREEIE www.ijareeie.com 1472
Fig 7.2 Thumb authentication
IX. CONCLUSION
Hence these modules are fully designed and implemented. In future this thumb registration will be followed by the face
recognition .After developing the face recognition system .The modules such as MMS and GPS will be implemented in
the forth coming days. It is totally dealt with the external security to the automotive .In future this project may extend
its security for the human beings to safe guard their valuable life from accidents. Even if occurred, the monitoring
necessities such as the status of the person, the heartbeat, the pulse of the human and the condition of the patient will be
reported to their relatives and the nearby hospitals .These ideas will be implemented in future.
ACKNOWLEDGMENT
The authors would like to thanks the Management, Principal and the HOD Electronics and Communication
Engineering, Dr.N.G.P.Institute of Technology, Tamil Nadu, India for their support and technical advices.
REFERENCES
[1] Dong-Sun Kim. Member, IEEE, seung- yerlLee,Member,IEEE,Byung-SooKim.Member,IEEE,Sung-Chul Lee and Duck-Jin
Chung,Member,IEEE on the design of an Embedded Biometric Smart Card Reader, IEEE Transactions on RIFD systems ,Vol 3, PP.573-
577,June 2010
[2] Jifeng Dai and JieZhou, Senior Member, IEEE, Multifeature-Based High-Resolution PalmprintRecognition,IEEE Transactions on Pattern
Analysis and Machine inteligence.Vol.33 No.5., pp.945-957, May 2011.
[3] Zhijian Hu and Yunping Chen, New Method Of Live Line Measuring the Inductance Parameters Of Transmission Lines Based On GPS
Technology,IEEE transactions on power delivery.vol.23 pp.1288-1295, july2008
[4] Simon Sarkka,Member,IEEE,VilleV.Senoir Member, IEEE , MilikaHuusko , and KaarleJaakkola, Phase-Based UHF RFID Tracking With
Nonlinear Kalman Filtering and Smoothing ,IEEE Sensors journal.vol.12.no.5,pp.904-910, May 2012.
[5] P.K.Chan student Member ,IEEE,C.S.Choy,SeniorMember,IEEE,C.F.Chan,Member,IEEE,K.P.Pun,Member,IEEE, Preparing Smartcard for
the F uture:From Passive To Active,IEEE transactions on smart card ,vol 3,pp.245-250,april 2010.
[6] MauricioPamplonaSegundo, Luciano Silva, member;IEEE, Olga Regina Pereira Bellon, Member, IEEE, and ChauaC.Queirolo, Automatic
Face Segmentation and Facial Landmark Detection in Range Images, IEEE Transactions on systems man and cybernetics-part b:
cybernetics.Vol.40.no.5,pp.1319-1330, october 2010
[7] Sarnin, S.S. Member, IEEE, Tahir, M.H.B.M. Member, IEEE, Immobilizer Engine Control Unit (ECU) Using Radio Frequency
Module,IEEE Trans. Ind. Electron.,pages 323-328, april 2007.
[8] Samarabandu, J.Member, IEEE ; Sidhu, T.Member, IEEE ; Beresh, R.Member, IEEE ; Jian-Cheng Tan Member, IEEESecurity Analysis and
Auditing of IEC61850-Based Automated Substations,Power Delivery,IEEE Transactions on Volume:25 , Issue: 4 Page(s):2346 2355, Oct.
2010,
[9] Brooks, R.R. Member, IEEE ; MD Sander, S.Member, IEEE ; Juan Deng ; Taiber, J.Member, IEEE Automobile security concernsVehicular
Technology Magazine, IEEE, Volume:4 , Issue: 2 Page(s):52 64, June 2009
ISSN (Print) : 2320 3765
ISSN (Online): 2278 8875
International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Vol. 2, I ssue 4, April 2013
Copyright to IJAREEIE www.ijareeie.com 1473
BIOGRAPHY
PriyaDarshini .V received his B.E. and M.E. degrees in the field of Instrumentation
Engineering and applied Electronics in 2005 and 2010 respectively .She has been in the
teaching field for about 7.2 years. She is currently working as an assistant professor in
the ECE department. Her interests include Image processing Embedded systems,
National Instruments LabVIEW and Wireless communication Systems.
Prakash .R is currently doing his Final year of Engineering in the field of Electronics
and communication engineering in Dr.N.G.P.Institute of Technology, Tamil Nadu,
and India. He had published a paper in an International Conference held in
Coimbatore Institute of Technology, Coimbatore. His interests include Digital
Electronics Embedded systems and Wireless communication Systems.
Prasannabalaje.S.M. is currently doing his Final year of Engineering in the field of
Electronics and communication engineering in Dr.N.G.P.Institute of Technology,
Tamil Nadu, and India. His interests include Digital Electronics Embedded systems
and Wireless communication Systems. He is an expert in Hardware and
communication systems.
Sangeetha Monica .T is currently doing her Final year of Engineering in the field of
Electronics and communication engineering in Dr.N.G.P.Institute of Technology,
Tamil Nadu, and India .She served as the student placement coordinator for ECE
department in her college . Her interests include Digital Electronics Embedded
systems and networks.
Vinodhini.R is currently doing her Final year of Engineering in the field of
Electronics and communication engineering in Dr.N.G.P.Institute of Technology,
Tamil Nadu, India. Her interests include Digital Electronics, Embedded systems and
Wireless communication Systems.
Rekha.V is currently doing her Final year of Engineering in the field of Electronics
and communication engineering in Dr.N.G.P.Institute of Technology, Tamil Nadu,
India. Her interests include image processing, Embedded systems and Wireless
communication Systems.
You might also like
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (894)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Activate Adobe Photoshop CS5 Free Using Serial KeyDocument3 pagesActivate Adobe Photoshop CS5 Free Using Serial KeyLukmanto68% (28)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- Process ValidationDocument116 pagesProcess ValidationsamirneseemNo ratings yet
- 2002 Chevrolet Trailblazer ManualDocument6 pages2002 Chevrolet Trailblazer ManualChittaranjan Baral0% (2)
- Ascet AutosarDocument173 pagesAscet AutosarChethanNo ratings yet
- City Gas Distribution ReportDocument22 pagesCity Gas Distribution Reportdimple1101100% (9)
- Blum2020 Book RationalCybersecurityForBusineDocument349 pagesBlum2020 Book RationalCybersecurityForBusineJulio Garcia GarciaNo ratings yet
- Introduction To ARADocument13 pagesIntroduction To ARAChittaranjan BaralNo ratings yet
- Master Thesis Mostafa MassoudDocument98 pagesMaster Thesis Mostafa MassoudChittaranjan BaralNo ratings yet
- Scilab TutorialDocument55 pagesScilab TutorialMichael Villame100% (1)
- Developer IqDocument15 pagesDeveloper IqChittaranjan BaralNo ratings yet
- Passenger ServicesDocument55 pagesPassenger ServicesChittaranjan BaralNo ratings yet
- 02 Boot SlidesDocument18 pages02 Boot SlidesChittaranjan BaralNo ratings yet
- BMW 20151005 PDFDocument28 pagesBMW 20151005 PDFChittaranjan BaralNo ratings yet
- 13 TCBExercise PostedDocument11 pages13 TCBExercise PostedChittaranjan BaralNo ratings yet
- Scilab Tutorial PDFDocument1 pageScilab Tutorial PDFChittaranjan Baral100% (1)
- Stack Corruption: Details Message ReplyDocument1 pageStack Corruption: Details Message ReplyChittaranjan BaralNo ratings yet
- HVACDocument2 pagesHVACChittaranjan BaralNo ratings yet
- How ToDocument7 pagesHow ToChittaranjan BaralNo ratings yet
- Mazda BrochuresDocument7 pagesMazda BrochuresChittaranjan BaralNo ratings yet
- NI-CAN BroucherDocument16 pagesNI-CAN BroucherChittaranjan BaralNo ratings yet
- F4FNCZNGBB7H2O7Document1 pageF4FNCZNGBB7H2O7MAMDISETNo ratings yet
- Can Tool DetailsDocument1 pageCan Tool DetailsChittaranjan BaralNo ratings yet
- Executive Summary FinalDocument6 pagesExecutive Summary FinalChittaranjan BaralNo ratings yet
- An-Imc-1-002 Flash Kernel CCP Hc12 Micro ControllerDocument14 pagesAn-Imc-1-002 Flash Kernel CCP Hc12 Micro ControllerChittaranjan BaralNo ratings yet
- AVR103: Using The EEPROM Programming Modes: FeaturesDocument5 pagesAVR103: Using The EEPROM Programming Modes: FeaturesSUGANSAPLNo ratings yet
- 25LC640Document24 pages25LC640hyd27No ratings yet
- 10 1 1 17 4493Document6 pages10 1 1 17 4493Chittaranjan BaralNo ratings yet
- Create A 1-Wire Master With Xilinx PicoBlaze - Reference Schematic - MaximDocument12 pagesCreate A 1-Wire Master With Xilinx PicoBlaze - Reference Schematic - MaximChittaranjan BaralNo ratings yet
- CAN Protocol Word FileDocument18 pagesCAN Protocol Word FileChittaranjan Baral100% (1)
- Sensor Circuit DesignDocument2 pagesSensor Circuit DesignChittaranjan BaralNo ratings yet
- 6-3 E MoessingerDocument29 pages6-3 E MoessingerChittaranjan BaralNo ratings yet
- 17 - Design of RF Based SpeedDocument4 pages17 - Design of RF Based SpeedChittaranjan BaralNo ratings yet
- Home Automation Topology Power Supply DesignDocument2 pagesHome Automation Topology Power Supply DesignChittaranjan BaralNo ratings yet
- 2.4 Adams Equity TheoryDocument1 page2.4 Adams Equity TheoryLoraineNo ratings yet
- Assignment 2 - p1 p2 p3Document16 pagesAssignment 2 - p1 p2 p3api-31192579150% (2)
- UPGRADEDocument2 pagesUPGRADEVedansh OswalNo ratings yet
- Market Participants in Securities MarketDocument11 pagesMarket Participants in Securities MarketSandra PhilipNo ratings yet
- Personal InsuranceDocument11 pagesPersonal InsuranceSumit Kumar SharmaNo ratings yet
- AB InBev Code of Business Conduct PDFDocument10 pagesAB InBev Code of Business Conduct PDFcristian quelmis vilca huarachiNo ratings yet
- Ielts Band 9 Sample Essay NoDocument5 pagesIelts Band 9 Sample Essay NoNhã NguyễnNo ratings yet
- FOMRHI Quarterly: Ekna Dal CortivoDocument52 pagesFOMRHI Quarterly: Ekna Dal CortivoGaetano PreviteraNo ratings yet
- Presentation Pineda Research CenterDocument11 pagesPresentation Pineda Research CenterPinedaMongeNo ratings yet
- Norms and specifications for distribution transformer, DG set, street light poles, LED lights and high mast lightDocument4 pagesNorms and specifications for distribution transformer, DG set, street light poles, LED lights and high mast lightKumar AvinashNo ratings yet
- Draft of The English Literature ProjectDocument9 pagesDraft of The English Literature ProjectHarshika Verma100% (1)
- The Non Technical Part: Sample Interview Questions For Network EngineersDocument5 pagesThe Non Technical Part: Sample Interview Questions For Network EngineersblablaNo ratings yet
- ECED Lab ReportDocument18 pagesECED Lab ReportAvni GuptaNo ratings yet
- AssemblyinstructionsDocument12 pagesAssemblyinstructionsPriscila AzevedoNo ratings yet
- Youtube AlgorithmDocument27 pagesYoutube AlgorithmShubham FarakateNo ratings yet
- WEEK 8 HW WS - B - Graphs & ChartsDocument6 pagesWEEK 8 HW WS - B - Graphs & Chartsangela trioNo ratings yet
- Equity AdvisorDocument2 pagesEquity AdvisorHarshit AgarwalNo ratings yet
- Characteristics: Wheels Alloy Aluminium Magnesium Heat ConductionDocument4 pagesCharacteristics: Wheels Alloy Aluminium Magnesium Heat ConductionJv CruzeNo ratings yet
- "Corbel" - Concrete Corbel Analysis: Program DescriptionDocument4 pages"Corbel" - Concrete Corbel Analysis: Program DescriptioniuliandurdureanuNo ratings yet
- HetNet Solution Helps Telcos Improve User Experience & RevenueDocument60 pagesHetNet Solution Helps Telcos Improve User Experience & RevenuefarrukhmohammedNo ratings yet
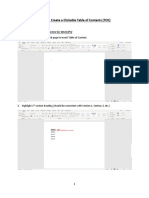
- How To: Create A Clickable Table of Contents (TOC)Document10 pagesHow To: Create A Clickable Table of Contents (TOC)Xuan Mai Nguyen ThiNo ratings yet
- Top Machine Learning ToolsDocument9 pagesTop Machine Learning ToolsMaria LavanyaNo ratings yet
- S0231689H02-B01-0001 Rev 02 Code 1 General Arrangement Drawing For 44 Kva Diesel Generator PDFDocument6 pagesS0231689H02-B01-0001 Rev 02 Code 1 General Arrangement Drawing For 44 Kva Diesel Generator PDFAnonymous AfjzJdnNo ratings yet
- Guardplc Certified Function Blocks - Basic Suite: Catalog Number 1753-CfbbasicDocument110 pagesGuardplc Certified Function Blocks - Basic Suite: Catalog Number 1753-CfbbasicTarun BharadwajNo ratings yet
- Chi Square LessonDocument11 pagesChi Square LessonKaia HamadaNo ratings yet
- Rust Experimental v2017 DevBlog 179 x64 #KnightsTableDocument2 pagesRust Experimental v2017 DevBlog 179 x64 #KnightsTableIngrutinNo ratings yet