Professional Documents
Culture Documents
MIS - Deliberate Software Attack
Uploaded by
jyoti_tanwar0508Original Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
MIS - Deliberate Software Attack
Uploaded by
jyoti_tanwar0508Copyright:
Available Formats
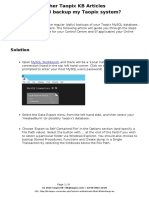
7
37
Deliberate Act of Sabotage or Vandalism
Individual or group who want to deliberately sabotage the
operations of a computer system or business, or perform
acts of vandalism to either destroy an asset or damage the
image of the organization
These threats can range from petty vandalism to organized
sabotage
Organizations rely on image so Web defacing can lead to
dropping consumer confidence and sales
Rising threat of hacktivist or cyber-activist operations the
most extreme version is cyber-terrorism
38
Deliberate Software Attacks
When an individual or group designs software to attack
systems, they create malicious code/software called
malware
Designed to damage, destroy, or deny service to the target systems
Mainly targeting Windows OS
http://stason.org/TULARC/os/linux.virus.html
http://www.sophos.com/pressoffice/news/articl
es/2006/02/macosxleap.html
Deliberate Software Attack
Includes:
macro virus
boot virus
worms
Trojan horses
logic bombs
back door or trap door
denial-of-service attacks
polymorphic
hoaxes
39 40
Virus
A virus is a computer program that copies
itself from file to file and typically performs
malicious or nuisance attacks on the
infected system
Upon activation, copies its code into one or
more larger programs
Hard to detect as well as hard to destroy or
deactivate
Symptoms of Virus
Computer runs slower then usual
Computer no longer boots up
Screen sometimes flicker
PC speaker beeps periodically
System crashes for no reason
Files/directories sometimes disappear
Denial of Service (DoS)
Display some strange message on the screen
41 42
HI Virus
The Hi virus was submitted in August, 1992. It is originally from Eastern
Europe. Hi is a memory resident infector of .EXE programs. When the first
Hi infected program is executed, the Hi virus will install itself memory
resident at the top of system memory but below the 640K DOS boundary,
moving interrupt 12's return. Total system and available free memory, as
indicated by the DOS CHKDSK program, will have decreased by 1,024
bytes. Interrupt 21 will be hooked by the virus. Once the Hi virus is
memory resident, it will infect .EXE programs when they are executed.
Infected programs will have a file length increase of 460 bytes with the
virus being located at the end of the file. The program's date and time in the
DOS disk directory listing will have been updated to the current system
date and time when infection occurred. The following text string can be
found near the end of all infected programs: "Hi"
8
Worms
Spread over network connection
Worms replicate
First worm released on the Internet was called
Morris worm, it was released on Nov 2, 1988.
Worms
Bubbleboy
Discovery Date: 11/8/1999
Origin: Argentina (?)
Length: 4992
Type: Worm/Macro
SubType: VbScript
Risk Assessment: Low
Category: Stealth/Companion
Worms
Bubbleboy
requires WSL (windows scripting language), Outlook or
Outlook Express, and IE5
Does not work in Windows NT
Effects Spanish and English version of Windows
2 variants have been identified
Is a latent virus on a Unix or Linux system
May cause DoS
Worms
How Bubbleboy works
Bubbleboy is embedded within an email message of HTML
format.
a VbScript while the user views a HTML page
a file named Update.hta is placed in the start up directory
upon reboot Bubbleboy executes
Worms
How Bubbleboy works
changes the registered owner/organization
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentV
ersion\RegisteredOwner = Bubble Boy
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentV
ersion\RegisteredOrganization = Vandalay Industry
using the Outlook MAPI address book it sends itself to each
entry
marks itself in the registry
HKEY_LOCAL_MACHINE\Software\Outlook.bubbleboy =
OUTLOOK.Bubbleboy1.0 by Zulu
48
Trojan Horse
A Trojan Horse is any program in which
malicious or harmful code is contained
inside of what appears to be a harmless
program
Malicious intent
Edit programs even registry information
Delete files
Set the computer as an FTP server
Obtain password
Spy
Usually doesnt reproduce
9
49
Trojan Horse
Back Orifice
Discovery Date: 10/15/1998
Origin: Pro-hacker Website
Length: 124,928
Type: Trojan
SubType: Remote Access
Risk Assessment: Low
Category: Stealth
Trojan Horse
About Back Orifice
requires Windows to work
distributed by Cult of the Dead Cow
similar to PC Anywhere, Carbon Copy software
allows remote access and control of other computers
install a reference in the registry
once infected, runs in the background
by default uses UDP port 54320
TCP port 54321
In Australia 72% of 92 ISP surveyed were infected with Back
Orifice
Trojan Horse
Features of Back Orifice
pings and query servers
reboot or lock up the system
list cached and screen saver password
display system information
logs keystrokes
edit registry
server control
receive and send files
display a message box
Macro
Specific to certain applications
Comprise a high percentage of the viruses
Usually made in WordBasic and Visual Basic for
Applications (VBA)
Microsoft shipped Concept, the first macro
virus, on a CD ROM called "Windows 95
Software Compatibility Test" in 1995
Macro
Melissa
Discovery Date: 3/26/1999
Origin: Newsgroup Posting
Length: varies depending on variant
Type: Macro/Worm
Subtype: Macro
Risk Assessment: High
Category: Companion
10
Macro
Melissa
requires WSL, Outlook or Outlook Express
Word 97 SR1 or Office 2000
105 lines of code (original variant)
received either as an infected template or email
attachment
lowers computer defenses to future macro
virus attacks
may cause DoS
infects template files with its own macro code
80% of of the 150 Fortune 1000 companies
were affected
Macro
How Melissa works
the virus is activated through a MS word document
document displays reference to pornographic websites
while macro runs
1st lowers the macro protection security setting for
future attacks
checks to see is it has run in current session before
HKEY_LOCAL_MACHINE\Software\Microsoft\Office\Melis
sa = by Kwyjibo
propagates itself using the Outlook MAPI address book
(emails sent to the first 50 addresses)
Macro
How Melissa works
infects the Normal.dot template file with its own code
Lastly if the minutes of the hour match up to the date
the macro inserts a quote by Bart Simpson into the
current document
Twenty two points, plus triple word score, plus fifty points
for using all my letters. Games over. Im outta here.
58
Back Door/Trap Door
Payload of virus, worm, Trojan horse
Allow the attacker to access the system at
will with special privileges
Back Orifice and Subseven
59
Polymorphism Boot Virus
Most difficult to remove
60
11
Logical Bomb
explosion based on logic
61
Spyware: what is it?
spyware is programming that is put in your
computer to spy on you
adware pushes ads, track Internet habits and
performs other sneaky tricks
62
Spyware: how do you know when you
have it?
Computers slow down to a crawl
Annoying Pop-ups appear
Browser Start Page changes
Unwanted toolbars, tray programs
New programs are installed on your PC and
show up on the desktop
63
Cases of Spyware Infection
64
65
Spybot in action
Here
You might also like
- List Anti Rootkit & AntiVirus For Ubuntu, Linux & BSD (Edition 2018)From EverandList Anti Rootkit & AntiVirus For Ubuntu, Linux & BSD (Edition 2018)No ratings yet
- Computer VirusDocument28 pagesComputer VirusPiyuSh JainNo ratings yet
- Free Antivirus And Antimalware Software For Ubuntu & Linux MintFrom EverandFree Antivirus And Antimalware Software For Ubuntu & Linux MintNo ratings yet
- NTCCDocument26 pagesNTCCPranav SharmaNo ratings yet
- Common Windows, Linux and Web Server Systems Hacking TechniquesFrom EverandCommon Windows, Linux and Web Server Systems Hacking TechniquesNo ratings yet
- Presentation On Computer VirusesDocument31 pagesPresentation On Computer Virusesmitesh67% (3)
- Best Free AntiVirus Software For Old Windows Xp Sp3 Operating System 2021 Bilingual VersionFrom EverandBest Free AntiVirus Software For Old Windows Xp Sp3 Operating System 2021 Bilingual VersionNo ratings yet
- SEO-Optimized Title for Computer Virus Seminar DocumentDocument28 pagesSEO-Optimized Title for Computer Virus Seminar DocumentDeepak PatraNo ratings yet
- Erbil polytechnic university student report on computer virusesDocument6 pagesErbil polytechnic university student report on computer virusesBlnd HawdianyNo ratings yet
- Computer VirusesDocument26 pagesComputer VirusesMahe KotaNo ratings yet
- Virus ProofDocument6 pagesVirus Proofashim01No ratings yet
- VirusesDocument23 pagesVirusestsegadese4No ratings yet
- CAP6135: Malware and Software Vulnerability Analysis: VirusesDocument21 pagesCAP6135: Malware and Software Vulnerability Analysis: Virusesshantaram35No ratings yet
- Why writing virus code and types of virusesDocument4 pagesWhy writing virus code and types of virusesAnkit BatraNo ratings yet
- Computerviruses 171008143158Document22 pagesComputerviruses 171008143158Ranmark BatonghinogNo ratings yet
- What is a Computer Security Risk? Types of Malware and Computer VirusesDocument10 pagesWhat is a Computer Security Risk? Types of Malware and Computer Viruseshantu malamNo ratings yet
- Computer VirusesDocument11 pagesComputer Viruseshasnain qayyumNo ratings yet
- Wish Virus Research Docments For Freelance WorkDocument43 pagesWish Virus Research Docments For Freelance Workmy wishNo ratings yet
- ICT LM Week 2Document37 pagesICT LM Week 2akioNo ratings yet
- Computer VirusDocument10 pagesComputer VirusBert CondinoNo ratings yet
- Section 6Document14 pagesSection 6Nguyễn Chí ThanhNo ratings yet
- Network Viruses and WormsDocument24 pagesNetwork Viruses and WormsKushan JeewanthaNo ratings yet
- Virus Types - HackersOnlineClubDocument4 pagesVirus Types - HackersOnlineClubMuhammad ShadabNo ratings yet
- Day - 1Document19 pagesDay - 1Sivakumar RavichandranNo ratings yet
- Malware Attacks:: Hekandjo Matheus, 201405997 CMP 3821 Network System Security Lab 1Document4 pagesMalware Attacks:: Hekandjo Matheus, 201405997 CMP 3821 Network System Security Lab 1Mathew Mathyzo HekandjoNo ratings yet
- Welcome To Our Welcome To Our: Presentatio NDocument33 pagesWelcome To Our Welcome To Our: Presentatio Ndurgesh30No ratings yet
- Computer Virus and MalwareDocument13 pagesComputer Virus and MalwareMaxim TawoutiaNo ratings yet
- History of VirusDocument15 pagesHistory of VirusKeziah Cheluj GamengNo ratings yet
- PIS Module 4Document26 pagesPIS Module 4Zayn TawfikNo ratings yet
- Microsoft PowerPoint 97-2004 PresentationDocument38 pagesMicrosoft PowerPoint 97-2004 PresentationShene LucinoNo ratings yet
- Introduction About Computer Viruses and Their Types.Document2 pagesIntroduction About Computer Viruses and Their Types.lianerivera24No ratings yet
- Infotech JS2 Eclass Computer VirusDocument2 pagesInfotech JS2 Eclass Computer VirusMaria ElizabethNo ratings yet
- The History of Computer VirusDocument5 pagesThe History of Computer VirusDrRohitKumarMDHomNo ratings yet
- Virus and Its TypesDocument7 pagesVirus and Its TypesrajNo ratings yet
- Se Re CoDocument30 pagesSe Re CoVishalNo ratings yet
- Module 5 - MalwareDocument5 pagesModule 5 - MalwareJamara Pucan100% (1)
- Computer ThreatsDocument6 pagesComputer Threatsjimmybarack27No ratings yet
- VirusDocument8 pagesVirusRavula KartheekNo ratings yet
- Understanding Malicious SoftwareDocument54 pagesUnderstanding Malicious SoftwareNarender KumarNo ratings yet
- Lec3 MalwaresDocument26 pagesLec3 MalwaresAhmad AleemNo ratings yet
- Cybersecurity FosteremilyDocument5 pagesCybersecurity Fosteremilyapi-543325403No ratings yet
- Computer VirusDocument7 pagesComputer Viruscabella_pasaporteNo ratings yet
- VirusDocument18 pagesVirusAtharvaNo ratings yet
- Introduction To Computer VirusesDocument31 pagesIntroduction To Computer Virusesaafy92% (12)
- Ethical - Hacking-1 (Islamic University of Science and Technology Pulwama)Document37 pagesEthical - Hacking-1 (Islamic University of Science and Technology Pulwama)cse 20 42Syed TawqeerNo ratings yet
- Computer Virus From Wikipedia, The Free EncyclopediaDocument14 pagesComputer Virus From Wikipedia, The Free EncyclopediaJustin CookNo ratings yet
- Computer VirusDocument5 pagesComputer Virussatudas149No ratings yet
- Defending Against Malicious Software AttacksDocument29 pagesDefending Against Malicious Software Attackshunter nullNo ratings yet
- English Unit3Document6 pagesEnglish Unit3tanetzheldakNo ratings yet
- Definition of 'Computer Virus'Document20 pagesDefinition of 'Computer Virus'BDlive. LandNo ratings yet
- 2ND Term Data Proc. E-NoteDocument30 pages2ND Term Data Proc. E-NoteEro ChuksNo ratings yet
- 16 WormsDocument69 pages16 WormsmeenakshiNo ratings yet
- Running Head: COMPUTER VIRUS: Computer Virus Sneha Chideti New England College Computer Security: Foundations - 202050Document5 pagesRunning Head: COMPUTER VIRUS: Computer Virus Sneha Chideti New England College Computer Security: Foundations - 202050cofoje9006No ratings yet
- Chapter # 6 - Security Copyright and The Law Page 180-191Document12 pagesChapter # 6 - Security Copyright and The Law Page 180-191Wasif QaziNo ratings yet
- Virus and Related ThreatsDocument28 pagesVirus and Related ThreatsNatarajan Kumaran100% (1)
- Chapter Five Computer Security: How Infections OccurDocument7 pagesChapter Five Computer Security: How Infections OccurErmiasNo ratings yet
- Computer Virus: Presented By: MahnoorDocument8 pagesComputer Virus: Presented By: MahnoorSana KhanNo ratings yet
- Avoiding Computer VirusesDocument1 pageAvoiding Computer VirusesCaroline Gustin100% (1)
- Adobe Acrobat Xi Pro 1102 Torrent PDFDocument4 pagesAdobe Acrobat Xi Pro 1102 Torrent PDFSaraNo ratings yet
- Website Baker ManualDocument21 pagesWebsite Baker ManualSivakaran YogaratnamNo ratings yet
- Drop BoxDocument6 pagesDrop BoxAndrés InfanteNo ratings yet
- Backup and RecoveryDocument66 pagesBackup and Recoveryjc_fleuryNo ratings yet
- JKSimBlast License FileDocument1 pageJKSimBlast License FileJulio SantosNo ratings yet
- HPOS SP12.1 Install and Config Guide Hpos41sp121incenUSDocument352 pagesHPOS SP12.1 Install and Config Guide Hpos41sp121incenUSParashar Singh100% (1)
- TaoPix Backup FAQ-80-enDocument8 pagesTaoPix Backup FAQ-80-enFernando CarneiroNo ratings yet
- Setup Log 2022-11-25 #001Document55 pagesSetup Log 2022-11-25 #001Francesco RegestroNo ratings yet
- Xiaomi Redmi 3S/Prime Hard Reset (How To Flash, Unlock Pattern Lock If Forget)Document5 pagesXiaomi Redmi 3S/Prime Hard Reset (How To Flash, Unlock Pattern Lock If Forget)Brajesh SinghNo ratings yet
- VVM Exam AppDocument11 pagesVVM Exam AppRUBIX PLANETNo ratings yet
- UnixDocument101 pagesUnixPreethi KishoreNo ratings yet
- Save SOLIDWORKS Drawing To PDF Macro To Automate The Process PDFDocument9 pagesSave SOLIDWORKS Drawing To PDF Macro To Automate The Process PDFch_deepakNo ratings yet
- HC110111012 File System Navigation and ManagementDocument19 pagesHC110111012 File System Navigation and ManagementPablo Eduardo PillajoNo ratings yet
- Linux FiltersDocument18 pagesLinux Filtersyashwanth sai100% (1)
- fqp0 BK Install Server Windows Oracle PDFDocument146 pagesfqp0 BK Install Server Windows Oracle PDFinvis31No ratings yet
- Red Hat AMQ-7.5-Managing AMQ Broker-en-USDocument72 pagesRed Hat AMQ-7.5-Managing AMQ Broker-en-USCvNo ratings yet
- Protel 2004 Training Manual PDFDocument210 pagesProtel 2004 Training Manual PDFCharoon SuriyawichitwongNo ratings yet
- Ops Center 14Document42 pagesOps Center 14bndycoolNo ratings yet
- Cloud 12CDocument44 pagesCloud 12CHưng NguyễnNo ratings yet
- How to get MCSE 2003 certified by passing 7 examsDocument8 pagesHow to get MCSE 2003 certified by passing 7 examsYoussef RadiNo ratings yet
- Climanager 4 2 User GuideDocument306 pagesClimanager 4 2 User GuideEivind48No ratings yet
- What is an Operating System: Definition, Types & FunctionsDocument64 pagesWhat is an Operating System: Definition, Types & FunctionsEmran HossainNo ratings yet
- Network Policy Server (NPS) Operations GuideDocument57 pagesNetwork Policy Server (NPS) Operations GuidesadcomNo ratings yet
- Jammu: Under The Guidance of Submitted by Raman Sir Akanksha Malla Class Roll No:-18 Board Roll NoDocument49 pagesJammu: Under The Guidance of Submitted by Raman Sir Akanksha Malla Class Roll No:-18 Board Roll NoPuneet ChawlaNo ratings yet
- Kaushik DevopsDocument6 pagesKaushik DevopsKritika ShuklaNo ratings yet
- Pega 7 Designer Studio TourDocument17 pagesPega 7 Designer Studio TourSivanand Pattabhi100% (2)
- Miflash@2020628Document2 pagesMiflash@2020628pavan kumarNo ratings yet
- Capcut EditingDocument14 pagesCapcut EditingPrecious Rhoilyn Dublado BascugNo ratings yet
- Rebranding The Atheros 928x Cards - The GuideDocument19 pagesRebranding The Atheros 928x Cards - The GuidemarkNo ratings yet
- Introduction To Adobe Indesign Cs6 Server DevelopmentDocument29 pagesIntroduction To Adobe Indesign Cs6 Server DevelopmentLuis Fernando BritoNo ratings yet