Professional Documents
Culture Documents
Draytek 2 Cisco VPN
Uploaded by
Marco ManzanoOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Draytek 2 Cisco VPN
Uploaded by
Marco ManzanoCopyright:
Available Formats
How to build LAN to LAN VPN connection between Vigor router and CiscoASA
This application will guide you to build LAN to LAN VPN connection between Vigor router (e.g., Vigor2910) and CiscoASA. Suppose, � � The WAN IP address of CISCO ASA is 203.70.63.90, while LAN IP address is 192.168.1.1/255.255.255.0 The WAN1 IP address of Vigor2910 is 59.125.9.159; while LAN IP is 192.169.20.1/255.255.255.0
1. Choose Wizards>>IPsec VPN Wizard.
2. The VPN Wizard will be popped-up as follows. Choose Site-to-Site as VPN Tunnel Type; Outside as VPN Tunnel Interface; and click Next.
3. Click Yes to continue.
4. Type the WAN IP address of the peer in the field of Peer IP Address for IPsec VPN connection. Then type the Pre-shared key. Next, a profile name will be generated automatically in the field of Tunnel Group Name. Click Next.
5. Keep the default settings of Encryption type and Authentication, and specify the DH Group for your request. Then, click Next.
6. For the second phase of IKE encryption, keep the default settings and click Next.
7. In the following screen, type the local / remote IP address with the subnet mask for local /remote network. Then, click Next.
8. Click Finish.
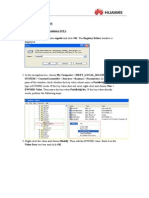
9. Click the tab of Configuration. Choose Site-to-Site VPN and click Connection Profiles. Now, the relational VPN settings will be displayed on the field of Connection Profiles. If required, you can click Edit on this field to modify other settings of VPN in details.
10. Click Edit to open the following screen. Expand the Advanced folder and choose Crypto Map Entry. Click Disable for Perfect Forward Secrecy, then choose answer-only as Connection Type. Next, click OK.
11. Click the tab of Configuration. Choose Firewall and click Access Rules.
12. Click Add. The Add Access Rule dialog will pop-up. Choose Inside as the Interface; and choose Permit as the Action. Choose local network as the Source; and remote network as the Destination. Next, click OK.
13. Click Add to add another access rule. Choose Outside as the Interface; and choose Permit as the Action. Choose remote network as the Source; and local network as the Destination. Next, click OK.
14. Access into the WUI of Vigor router (e.g., Vigor2910).
15. Open VPN and Remote Access>>LAN to LAN. Click index #1.
16. Type a name for such profile (e.g, cisco, in this case) and check the box of Enable this profile. Click Dial-Out as Call Direction and check Always on. Next, choose IPSec Tunnel as the Type of Server I am calling. Type the WAN IP address of the Peer (e.g., 203.70.63.90, in this case). Specify a Pre-Shared Key which must be the same as the settings configured in ASA.
17. As for IPSec Security Method, choose High. Click Advanced to open IKE advanced settings dialog box. In the dialog, please choose the IKE phase 1 proposal and IKE phase 2 proposal settings based on the network environment. Next, click OK to save the settings and exit the dialog.
18. Type the remote network IP address and subnet mask (e.g., the inside interface of CiscoASA). Then, click OK.
19. Now, a LAN to LAN VPN connection between Vigor router and CiscoASA has been established.
You might also like
- Building Lan To Lan VPN From Vigor2920 To Vigor3900 by Using Ipsec Tunnel (Aggressive Mode)Document6 pagesBuilding Lan To Lan VPN From Vigor2920 To Vigor3900 by Using Ipsec Tunnel (Aggressive Mode)atomdNo ratings yet
- VPN IPSec DFL-860 To DFL-210-260-800-860-1600Document12 pagesVPN IPSec DFL-860 To DFL-210-260-800-860-1600marius_marinacheNo ratings yet
- SDM: Site-To-Site Ipsec VPN Between Asa/Pix and An Ios Router Configuration ExampleDocument37 pagesSDM: Site-To-Site Ipsec VPN Between Asa/Pix and An Ios Router Configuration ExampleAnonymous GEyA5IrNo ratings yet
- Broadband Router SettingDocument5 pagesBroadband Router SettingjlsinghNo ratings yet
- FortiGate To SonicWall VPN SDocument3 pagesFortiGate To SonicWall VPN SFabricio Soares BiccaNo ratings yet
- PremierWave XN QSDocument1 pagePremierWave XN QSJosué González LópezNo ratings yet
- How To Configure A VPNDocument5 pagesHow To Configure A VPNCentaur ArcherNo ratings yet
- Setting Up IPSec VPN ConnectionDocument13 pagesSetting Up IPSec VPN ConnectionhorstihorstNo ratings yet
- Networking Consolidated Under ArubaDocument54 pagesNetworking Consolidated Under ArubaRudinHariantoNo ratings yet
- Wifirobin ManualDocument25 pagesWifirobin ManualfilfrNo ratings yet
- Configuring An Ipsec VPN Tunnel Between A Cisco Sa 500 and A Mac Ipsecuritas ClientDocument11 pagesConfiguring An Ipsec VPN Tunnel Between A Cisco Sa 500 and A Mac Ipsecuritas Clientjhoan9924No ratings yet
- Cyberoam Firewall Rule Creation GuideDocument8 pagesCyberoam Firewall Rule Creation Guideraj KumarNo ratings yet
- VPNDocument18 pagesVPNsuddddddNo ratings yet
- So, Here Is My Step-By-Step Guide To Configuring A Wi-FiDocument3 pagesSo, Here Is My Step-By-Step Guide To Configuring A Wi-FinagapratapNo ratings yet
- MikroTik Site To Site OpenVPN Server SetupDocument5 pagesMikroTik Site To Site OpenVPN Server SetupDanuLSNo ratings yet
- How To Configure A Client-to-Site IPsec VPNDocument4 pagesHow To Configure A Client-to-Site IPsec VPNisoloNo ratings yet
- Vigor 2930 MonitoringDocument7 pagesVigor 2930 MonitoringgulshomeNo ratings yet
- VPN Configuration Guide: Cisco ASA 5500 SeriesDocument26 pagesVPN Configuration Guide: Cisco ASA 5500 SeriesHugo RamirezNo ratings yet
- Check Point Vlan v1 0Document26 pagesCheck Point Vlan v1 0Jignesh BhalsodNo ratings yet
- Pocket Guide: Establish Ipsec VPN Connection Between Sophos XG and Palo Alto FirewallDocument15 pagesPocket Guide: Establish Ipsec VPN Connection Between Sophos XG and Palo Alto FirewallCyber SkyNo ratings yet
- WNC Open Boost-N-manual PDFDocument44 pagesWNC Open Boost-N-manual PDFChris BarolasNo ratings yet
- How To Configure A 'Route All Traffic' WAN GroupVPN PolicyDocument10 pagesHow To Configure A 'Route All Traffic' WAN GroupVPN PolicyneuseeNo ratings yet
- Step-by-Step Guide to Set up a VPNDocument5 pagesStep-by-Step Guide to Set up a VPNjamilpervaz1No ratings yet
- Site To Site IPsec VPNDocument27 pagesSite To Site IPsec VPNRasakiRraskiNo ratings yet
- WiFi Shield v21 Tutorial v01Document18 pagesWiFi Shield v21 Tutorial v01riabu182No ratings yet
- Install and Configure OSS VPNDocument9 pagesInstall and Configure OSS VPNFima Yuda EktikaNo ratings yet
- Configure VPN on TP-LINK Routers with IPsec VPN ClientsDocument64 pagesConfigure VPN on TP-LINK Routers with IPsec VPN ClientssuadmujicNo ratings yet
- Air Force One 2 V3 User ManualDocument53 pagesAir Force One 2 V3 User Manualhacker069100% (2)
- Configuring SonicWALL Port ForwardingDocument7 pagesConfiguring SonicWALL Port ForwardingjayaprahasNo ratings yet
- DrayTek Remote Dial in User Profile 6 enDocument26 pagesDrayTek Remote Dial in User Profile 6 enThiago Juliano SouzaNo ratings yet
- Troubleshooting Common Issues With Global VPN Client GVCDocument2 pagesTroubleshooting Common Issues With Global VPN Client GVCrijugNo ratings yet
- AC6-How To Setup Client+AP ModeDocument11 pagesAC6-How To Setup Client+AP ModedionisiusdiucezNo ratings yet
- Activity 3: 2003. Youtube Video Link: Https://Youtu - Be/FsprvgyajfmDocument2 pagesActivity 3: 2003. Youtube Video Link: Https://Youtu - Be/FsprvgyajfmMarjorie caldeaNo ratings yet
- Sophos XG Firewall - How To Configure SSL VPN Remote Access - Sophos CommunityDocument14 pagesSophos XG Firewall - How To Configure SSL VPN Remote Access - Sophos CommunityKhalid NatiqNo ratings yet
- Configure SSL VPN on PANOS 4.0Document14 pagesConfigure SSL VPN on PANOS 4.0Adrian VargasNo ratings yet
- Mikrotik Basic Internet Sharing With Bandwidth LimitingDocument8 pagesMikrotik Basic Internet Sharing With Bandwidth LimitingMuhammad Abdullah ButtNo ratings yet
- ARGtek CPE2615 User ManualDocument48 pagesARGtek CPE2615 User ManualPriyo SanyotoNo ratings yet
- smb5553 Configure Anyconnect Virtual Private Network VPN ConnectivitDocument13 pagessmb5553 Configure Anyconnect Virtual Private Network VPN ConnectivitalecNo ratings yet
- Configuring IPsec VPN With A FortiGate and A Cisco ASADocument6 pagesConfiguring IPsec VPN With A FortiGate and A Cisco ASAAshokNo ratings yet
- Port forwarding for D-Link G604T routerDocument7 pagesPort forwarding for D-Link G604T routerjonrocat2002No ratings yet
- DV230 Configuration Troubleshooting Guide v1.3: Sept. 15 09Document21 pagesDV230 Configuration Troubleshooting Guide v1.3: Sept. 15 09Wan Mazlan Wan MohamedNo ratings yet
- How To Create VTIDocument3 pagesHow To Create VTIEsteban GraciaNo ratings yet
- Configure AnyConnect VPN on RV34x RouterDocument13 pagesConfigure AnyConnect VPN on RV34x RouterThe Maison MaidsNo ratings yet
- Basic Mikrotik Configuration With PPPoE ServerDocument41 pagesBasic Mikrotik Configuration With PPPoE Serverarbabnazar786100% (1)
- Palo Alto Firewall With ROAS Design (Basic Lab)-1Document12 pagesPalo Alto Firewall With ROAS Design (Basic Lab)-1pramodNo ratings yet
- PortDocument4 pagesPortDinko DiĐNo ratings yet
- Basic Fortigate Firewall ConfigurationDocument17 pagesBasic Fortigate Firewall ConfigurationMuhDickiSetyawan96% (67)
- IPsec VPN To Microsoft Azure PDFDocument9 pagesIPsec VPN To Microsoft Azure PDFDaniel ÁvilaNo ratings yet
- ZTE 831 SeriesDocument8 pagesZTE 831 Seriesmoss2uNo ratings yet
- Creating A Split Tunnel VPN Connection in LinuxDocument11 pagesCreating A Split Tunnel VPN Connection in LinuxLORENA BOTERO BETANCURNo ratings yet
- SP9015 ManualDocument42 pagesSP9015 ManualMayela SotoNo ratings yet
- Configuring Snapgear Router As A Firewall and VPNDocument8 pagesConfiguring Snapgear Router As A Firewall and VPNDragon_novemberNo ratings yet
- Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNFrom EverandSet Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNRating: 5 out of 5 stars5/5 (1)
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3From EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3No ratings yet
- Hacking : A Comprehensive, Step-By-Step Guide to Techniques and Strategies to Learn Ethical Hacking with Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingFrom EverandHacking : A Comprehensive, Step-By-Step Guide to Techniques and Strategies to Learn Ethical Hacking with Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingNo ratings yet
- Teacher swap agreement for family reasonsDocument4 pagesTeacher swap agreement for family reasonsKimber LeeNo ratings yet
- Shilajit The Panacea For CancerDocument48 pagesShilajit The Panacea For Cancerliving63100% (1)
- Principle of Utmost Good FaithDocument7 pagesPrinciple of Utmost Good FaithshreyaNo ratings yet
- Best Safety Practices in The Philippine Construction PDFDocument16 pagesBest Safety Practices in The Philippine Construction PDFDione Klarisse GuevaraNo ratings yet
- Monson, Concilio Di TrentoDocument38 pagesMonson, Concilio Di TrentoFrancesca Muller100% (1)
- The Political Philosophy of Giorgio Agamben A Critical EvaluationDocument20 pagesThe Political Philosophy of Giorgio Agamben A Critical EvaluationLEANo ratings yet
- Term Paper On BF SkinnerDocument7 pagesTerm Paper On BF Skinnerc5rga5h2100% (1)
- History: The Origin of Kho-KhotheDocument17 pagesHistory: The Origin of Kho-KhotheIndrani BhattacharyaNo ratings yet
- Cignal Channel 490Document2 pagesCignal Channel 490Arild JuliusNo ratings yet
- Writing Assessment and Evaluation Checklist - PeerDocument1 pageWriting Assessment and Evaluation Checklist - PeerMarlyn Joy YaconNo ratings yet
- 10 1108 - Apjie 02 2023 0027Document17 pages10 1108 - Apjie 02 2023 0027Aubin DiffoNo ratings yet
- Relay Models Per Types Mdp38 EnuDocument618 pagesRelay Models Per Types Mdp38 Enuazer NadingaNo ratings yet
- SK Council Authorizes New Bank AccountDocument3 pagesSK Council Authorizes New Bank Accountt3emo shikihiraNo ratings yet
- The Scavenger's Handbook v1 SmallerDocument33 pagesThe Scavenger's Handbook v1 SmallerBeto TNo ratings yet
- Political Science Assignment PDFDocument6 pagesPolitical Science Assignment PDFkalari chandanaNo ratings yet
- Operative ObstetricsDocument6 pagesOperative ObstetricsGrasya ZackieNo ratings yet
- SEIPIDocument20 pagesSEIPIdexterbautistadecember161985No ratings yet
- NQC User ManualDocument6 pagesNQC User ManualgarneliNo ratings yet
- The Role of Store LocationDocument6 pagesThe Role of Store LocationJessa La Rosa MarquezNo ratings yet
- History of Downtown San Diego - TimelineDocument3 pagesHistory of Downtown San Diego - Timelineapi-671103457No ratings yet
- Rainin Catalog 2014 ENDocument92 pagesRainin Catalog 2014 ENliebersax8282No ratings yet
- FOREIGN DOLL CORP May 2023 TD StatementDocument4 pagesFOREIGN DOLL CORP May 2023 TD Statementlesly malebrancheNo ratings yet
- Your Money Personality Unlock The Secret To A Rich and Happy LifeDocument30 pagesYour Money Personality Unlock The Secret To A Rich and Happy LifeLiz Koh100% (1)
- Booklet - CopyxDocument20 pagesBooklet - CopyxHåkon HallenbergNo ratings yet
- Ck-Nac FsDocument2 pagesCk-Nac Fsadamalay wardiwiraNo ratings yet
- Case Study - Succession LawDocument2 pagesCase Study - Succession LawpablopoparamartinNo ratings yet
- Scantype NNPC AdvertDocument3 pagesScantype NNPC AdvertAdeshola FunmilayoNo ratings yet
- Legal Maxim V02Document29 pagesLegal Maxim V02singam harikanthNo ratings yet
- Eco Orphanage: Model of Sustainability: 15 536 Words (Not Including Bibliography)Document78 pagesEco Orphanage: Model of Sustainability: 15 536 Words (Not Including Bibliography)Princess ManiquizNo ratings yet
- Block 2 MVA 026Document48 pagesBlock 2 MVA 026abhilash govind mishraNo ratings yet