Professional Documents
Culture Documents
Asa Ldap Authentication
Uploaded by
j_benz44Original Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Asa Ldap Authentication
Uploaded by
j_benz44Copyright:
Available Formats
ASA 8.
0: Configure LDAP Authentication for WebVPN Users
Document ID: 98625
Contents
Introduction Prerequisites Background Information Configure LDAP Authentication ASDM Command Line Interface Perform MultiDomain Searches (Optional) Verify Test with ASDM Test with CLI Troubleshoot Related Information
Introduction
This document demonstrates how to configure the Cisco Adaptive Security Appliance (ASA) to use an LDAP server for authentication of WebVPN users. The LDAP server in this example is Microsoft Active Directory. This configuration is performed with Adaptive Security Device Manager (ASDM) 6.0(2) on an ASA that runs software version 8.0(2). Note: In this example Lightweight Directory Access Protocol (LDAP) authentication is configured for WebVPN users, but this configuration can be used for all other types of remote access clients as well. Simply assign the AAA server group to the desired connection profile (tunnel group), as shown.
Prerequisites
A basic VPN configuration is required. In this example WebVPN is used.
Background Information
In this example, the ASA checks with an LDAP server in order to verify the identity of users that it authenticates. This process does not work like a traditional Remote Authentication DialIn User Service (RADIUS) or Terminal Access Controller AccessControl System Plus (TACACS+) exhange. These steps explain, at a high level, how the ASA uses an LDAP server in order to check user credentials. 1. The user initiates a connection to the ASA. 2. The ASA is configured to authenticate that user with the Microsoft Active Directory (AD)/LDAP server. 3. The ASA binds to the LDAP server with the credentials configured on the ASA (admin in this case), and looks up the provided username. The admin user also obtains the appropriate credentials to list contents within Active Directory. Refer to http://support.microsoft.com/?id=320528 for more information about how to grant LDAP query privileges.
Note: The Microsoft website at http://support.microsoft.com/?id=320528 is managed by a third party provider. Cisco is not responsible for its content. 4. If the username is found, the ASA attempts to bind to the LDAP server with the credentials that the user provided at login. 5. If the second bind is successful, authentication succeeds and the the ASA processes the attributes of the user. Note: In this example the attributes are not used for anything. Refer to ASA/PIX: Mapping VPN Clients to VPN Group Policies Through LDAP Configuration Example in order to see an example of how the ASA can process LDAP attributes.
Configure LDAP Authentication
In this section, you are presented with the information to configure the ASA to use an LDAP server for the authentication of WebVPN clients.
ASDM
Complete these steps in the ASDM in order to configure the ASA to communicate with the LDAP server and authenticate WebVPN clients. 1. Navigate to Configuration > Remote Access VPN > AAA Setup > AAA Server Groups. 2. Click Add next to AAA Server Groups 3. Specify a name for the new AAA Server group, and choose LDAP as the protocol.
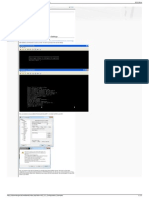
4. Be sure that your new group is selected in the top pane, and click Add next to the Servers in the Selected Group pane. 5. Provide the configuration information for your LDAP server. The subsequent screenshot illustrates an example configuration. This is an explanation of many of the configuration options: Interface Namethe interface that the ASA uses in order to reach the LDAP server Server Name or IP addressthe address that the ASA uses in order to reach the LDAP server Server Typethe type of LDAP server, such as Microsoft Base DNthe location in the LDAP hierarchy where the server must begin to search Scopethe extent of the search in the LDAP hierarchy that the server must make Naming Attributethe Relative Distinguished Name attribute (or attributes) that uniquely identifies an entry on the LDAP server. sAMAccountName is the default attribute in the
Microsoft Active Directory. Other commonly used attributes are CN, UID, and userPrincipalName. Login DNthe DN with enough privileges in order to be able to search/lread/lookup users in the LDAP server Login Passwordthe password for the DN account LDAP Attribute Mapan LDAP attribute map to be used with responses from this server. Refer to ASA/PIX: Mapping VPN Clients to VPN Group Policies Through LDAP Configuration Example for more information on how to configure LDAP attribute maps.
6. Once you have configured the AAA server group and added a server to it, it is necessary to configure your connection profile (tunnel group) to use the new AAA configuration. Navigate to Configuration > Remote Access VPN > Clientless SSL VPN Access > Connection Profiles. 7. Choose the connection profile (tunnel group) for which you want to configure AAA, and click Edit 8. Under Authentication, choose the LDAP server group that you created earlier.
Command Line Interface
Complete these steps in the command line interface (CLI) in order to configure the ASA to communicate with the LDAP server and authenticate WebVPN clients.
ciscoasa#configure terminal
! Configure the AAA Server group. ciscoasa(config)#aaaserver LDAP_SRV_GRP protocol ldap
! Configure the AAA Server.
ciscoasa(configaaaservergroup)#aaaserver LDAP_SRV_GRP (inside) host 192.168.1.2 ciscoasa(configaaaserverhost)#ldapbasedn dc=ftwsecurity, dc=cisco, dc=com ciscoasa(configaaaserverhost)#ldaplogindn cn=admin, cn=users, dc=ftwsecurity, dc=cisco ciscoasa(configaaaserverhost)#ldaploginpassword ********** ciscoasa(configaaaserverhost)#ldapnamingattribute sAMAccountName ciscoasa(configaaaserverhost)#ldapscope subtree ciscoasa(configaaaserverhost)#servertype microsoft ciscoasa(configaaaserverhost)#exit
! Configure the tunnel group to use the new AAA setup. ciscoasa(config)#tunnelgroup ExampleGroup2 generalatt ciscoasa(configtunnelgeneral)#authenticationservergroup LDAP_SRV_GRP
Perform MultiDomain Searches (Optional)
Optional. The ASA currently does not support the LDAP referal mechanism for multidomain searches (Cisco bug ID CSCsj32153). Multidomain searches are supported with the AD in Global Catalog Server mode. In order to perform multidomain searches, setup up the AD server for Global Catalog Server mode, usually with the these key parameters for the LDAP server entry in the ASA. The key is to use an ldapnameattribute that must be unique across the directory tree.
serverport 3268 ldapscope subtree ldapnamingattribute userPrincipalName
Verify
Use this section in order to confirm that your configuration works properly.
Test with ASDM
Verify your LDAP configuration with the Test button on the AAA Server Groups configuration screen. Once you supply a username and password, this button allows you to send a test authentication request to the LDAP server. 1. Navigate to Configuration > Remote Access VPN > AAA Setup > AAA Server Groups. 2. Select your desired AAA Server group in the top pane. 3. Select the AAA server that you want to test in the lower pane. 4. Click the Test button to the right of the lower pane. 5. In the window that appears, click the Authentication radio button, and supply the credentials with which you want to test. Click OK when finished.
6. After the ASA contacts the LDAP server, a success or failure message appears.
Test with CLI
You can use the test command on the command line in order to test your AAA setup. A test request is sent to the AAA server, and the result appears on the command line.
ciscoasa#test aaaserver authentication LDAP_SRV_GRP host 192.168.1.2 username kate password cisco123 INFO: Attempting Authentication test to IP address <192.168.1.2> (timeout: 12 seconds) INFO: Authentication Successful
Troubleshoot
If unsure of the current DN string to use, you can issue the dsquery command on a Windows Active Driectory server from a command prompt in order to verify the appropriate DN String of a user object.
C:\Documents and Settings\Administrator>dsquery user samid kate
! Queries Active Directory for samid id "kate" "CN=Kate Austen,CN=Users,DC=ftwsecurity,DC=cisco,DC=com"
The debug ldap 255 command can help to troubleshoot authentication problems in this scenario. This command enables LDAP debugging and allows you to watch the process that the ASA uses to connect to the LDAP server. This outputs show the ASA connect to the LDAP server as outlined in the Background Information section of this document. This debug shows a successful authentication:
ciscoasa#debug ldap 255 [7] Session Start [7] New request Session, context 0xd4b11730, reqType = 1 [7] Fiber started [7] Creating LDAP context with uri=ldap://192.168.1.2:389 [7] Connect to LDAP server: ldap://192.168.1.2:389, status = Successful [7] defaultNamingContext: value = DC=ftwsecurity,DC=cisco,DC=com [7] supportedLDAPVersion: value = 3 [7] supportedLDAPVersion: value = 2 [7] supportedSASLMechanisms: value = GSSAPI [7] supportedSASLMechanisms: value = GSSSPNEGO [7] supportedSASLMechanisms: value = EXTERNAL [7] supportedSASLMechanisms: value = DIGESTMD5
! The ASA connects to the LDAP server as admin to search for kate. [7] Binding as administrator [7] Performing Simple authentication for admin to 192.168.1.2
[7] LDAP Search: Base DN = [dc=ftwsecurity, dc=cisco, dc=com] Filter = [sAMAccountName=kate] Scope = [SUBTREE] [7] User DN = [CN=Kate Austen,CN=Users,DC=ftwsecurity,DC=cisco,DC=com] [7] Talking to Active Directory server 192.168.1.2 [7] Reading password policy for kate, dn:CN=Kate Austen,CN=Users, DC=ftwsecurity,DC=cisco,DC=com [7] Read bad password count 1
! The ASA binds to the LDAP server as kate to test the password. [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] [7] Binding as user Performing Simple authentication for kate to 192.168.1.2 Checking password policy for user kate Binding as administrator Performing Simple authentication for admin to 192.168.1.2 Authentication successful for kate to 192.168.1.2 Retrieving user attributes from server 192.168.1.2 Retrieved Attributes: objectClass: value = top objectClass: value = person objectClass: value = organizationalPerson objectClass: value = user cn: value = Kate Austen sn: value = Austen givenName: value = Kate distinguishedName: value = CN=Kate Austen,CN=Users,DC=ftwsecurity, DC=cisco,DC=com instanceType: value = 4 whenCreated: value = 20070815155224.0Z whenChanged: value = 20070815195813.0Z displayName: value = Kate Austen uSNCreated: value = 16430 memberOf: value = CN=Castaways,CN=Users,DC=ftwsecurity,DC=cisco,DC=com memberOf: value = CN=Employees,CN=Users,DC=ftwsecurity,DC=cisco,DC=com uSNChanged: value = 20500 name: value = Kate Austen objectGUID: value = ..z...yC.q0..... userAccountControl: value = 66048 badPwdCount: value = 1 codePage: value = 0 countryCode: value = 0 badPasswordTime: value = 128321799570937500 lastLogoff: value = 0 lastLogon: value = 128321798130468750 pwdLastSet: value = 128316667442656250 primaryGroupID: value = 513 objectSid: value = ............Q..p..*.p?E.Z... accountExpires: value = 9223372036854775807 logonCount: value = 0 sAMAccountName: value = kate sAMAccountType: value = 805306368 userPrincipalName: value = kate@ftwsecurity.cisco.com objectCategory: value = CN=Person,CN=Schema,CN=Configuration, DC=ftwsecurity,DC=cisco,DC=com dSCorePropagationData: value = 20070815195237.0Z dSCorePropagationData: value = 20070815195237.0Z dSCorePropagationData: value = 20070815195237.0Z dSCorePropagationData: value = 16010108151056.0Z Fiber exit Tx=685 bytes Rx=2690 bytes, status=1 Session End
This debug shows an authentication that fails due to an incorrect password:
ciscoasa#debug ldap 255 [8] Session Start [8] New request Session, context 0xd4b11730, reqType = 1 [8] Fiber started [8] Creating LDAP context with uri=ldap://192.168.1.2:389 [8] Connect to LDAP server: ldap://192.168.1.2:389, status = Successful [8] defaultNamingContext: value = DC=ftwsecurity,DC=cisco,DC=com [8] supportedLDAPVersion: value = 3 [8] supportedLDAPVersion: value = 2 [8] supportedSASLMechanisms: value = GSSAPI [8] supportedSASLMechanisms: value = GSSSPNEGO [8] supportedSASLMechanisms: value = EXTERNAL [8] supportedSASLMechanisms: value = DIGESTMD5
! The ASA connects to the LDAP server as admin to search for kate. [8] Binding as administrator [8] Performing Simple authentication for admin to 192.168.1.2 [8] LDAP Search: Base DN = [dc=ftwsecurity, dc=cisco, dc=com] Filter = [sAMAccountName=kate] Scope = [SUBTREE] [8] User DN = [CN=Kate Austen,CN=Users,DC=ftwsecurity,DC=cisco,DC=com] [8] Talking to Active Directory server 192.168.1.2 [8] Reading password policy for kate, dn:CN=Kate Austen,CN=Users, DC=ftwsecurity,DC=cisco,DC=com [8] Read bad password count 1
! The ASA attempts to bind as kate, but the password is incorrect. [8] [8] [8] [8] [8] [8] [8] [8] [8] [8] [8] [8] Binding as user Performing Simple authentication for kate to 192.168.1.2 Simple authentication for kate returned code (49) Invalid credentials Binding as administrator Performing Simple authentication for admin to 192.168.1.2 Reading bad password count for kate, dn: CN=Kate Austen,CN=Users, DC=ftwsecurity,DC=cisco,DC=com Received badPwdCount=1 for user kate badPwdCount=1 before, badPwdCount=1 after for kate now: Tue, 28 Aug 2007 15:33:05 GMT, lastset: Wed, 15 Aug 2007 15:52:24 GMT, delta=1122041, maxage=3710851 secs Invalid password for kate Fiber exit Tx=788 bytes Rx=2904 bytes, status=1 Session End
This debug shows an authentication that fails because the user can not be found on the LDAP server:
ciscoasa#debug ldap 255 [9] Session Start [9] New request Session, context 0xd4b11730, reqType = 1 [9] Fiber started [9] Creating LDAP context with uri=ldap://192.168.1.2:389 [9] Connect to LDAP server: ldap://192.168.1.2:389, status = Successful [9] defaultNamingContext: value = DC=ftwsecurity,DC=cisco,DC=com [9] supportedLDAPVersion: value = 3 [9] supportedLDAPVersion: value = 2 [9] supportedSASLMechanisms: value = GSSAPI [9] supportedSASLMechanisms: value = GSSSPNEGO [9] supportedSASLMechanisms: value = EXTERNAL [9] supportedSASLMechanisms: value = DIGESTMD5
! The user mikhail is not found.
[9] Binding as administrator [9] Performing Simple authentication for admin to 192.168.1.2 [9] LDAP Search: Base DN = [dc=ftwsecurity, dc=cisco, dc=com] Filter = [sAMAccountName=mikhail] Scope = [SUBTREE] [9] Requested attributes not found [9] Fiber exit Tx=256 bytes Rx=607 bytes, status=1 [9] Session End
The debugs show this error message when the connectivity between the ASA and the LDAP authentication server does not work:
ciscoasa# debug webvpn 255 INFO: debug webvpn enabled at level 255. ciscoasa# webvpn_portal.c:ewaFormSubmit_webvpn_login[2162] ewaFormSubmit_webvpn_login: tgCookie = NULL ewaFormSubmit_webvpn_login: cookie = 1 ewaFormSubmit_webvpn_login: tgCookieSet = 0 ewaFormSubmit_webvpn_login: tgroup = NULL ....not resuming [2587] webvpn_portal.c:http_webvpn_kill_cookie[787] webvpn_auth.c:http_webvpn_pre_authentication[2327] WebVPN: calling AAA with ewsContext (847917520) and nh (851696992)! webvpn_auth.c:webvpn_add_auth_handle[5118] WebVPN: started user authentication... webvpn_auth.c:webvpn_aaa_callback[5158] WebVPN: AAA status = (ERROR) webvpn_portal.c:ewaFormSubmit_webvpn_login[2162] ewaFormSubmit_webvpn_login: tgCookie = NULL ewaFormSubmit_webvpn_login: cookie = 1 ewaFormSubmit_webvpn_login: tgCookieSet = 0 ewaFormSubmit_webvpn_login: tgroup = NULL ....resuming [2564] webvpn_auth.c:http_webvpn_post_authentication[1506] WebVPN: user: (utrcd01) auth error.
Related Information
Technical Support & Documentation Cisco Systems
Contacts & Feedback | Help | Site Map 2010 2011 Cisco Systems, Inc. All rights reserved. Terms & Conditions | Privacy Statement | Cookie Policy | Trademarks of Cisco Systems, Inc.
Updated: Sep 24, 2007
Document ID: 98625
You might also like
- Lab 4: Access Policy For EasyconnectDocument12 pagesLab 4: Access Policy For EasyconnectJosel ArevaloNo ratings yet
- Configuration and Evaluation of Some Microsoft and Linux Proxy Servers, Security, Intrusion Detection, AntiVirus and AntiSpam ToolsFrom EverandConfiguration and Evaluation of Some Microsoft and Linux Proxy Servers, Security, Intrusion Detection, AntiVirus and AntiSpam ToolsNo ratings yet
- Practical Deployment of Cisco Identity Services Engine (ISE): Real-World Examples of AAA DeploymentsFrom EverandPractical Deployment of Cisco Identity Services Engine (ISE): Real-World Examples of AAA DeploymentsRating: 5 out of 5 stars5/5 (2)
- Quick Configuration of Openldap and Kerberos In Linux and Authenicating Linux to Active DirectoryFrom EverandQuick Configuration of Openldap and Kerberos In Linux and Authenicating Linux to Active DirectoryNo ratings yet
- Ansible Lab - Quick LearnDocument57 pagesAnsible Lab - Quick LearnJoel White100% (1)
- Web Dispatcher SSL Trust ConfigurationDocument12 pagesWeb Dispatcher SSL Trust ConfigurationAmiya ChakrabortyNo ratings yet
- Versa - Configure AAADocument21 pagesVersa - Configure AAAIsrael PNo ratings yet
- Aaa LdapDocument12 pagesAaa LdapuserossNo ratings yet
- Ccna Security Section 3bDocument21 pagesCcna Security Section 3bRatnesh KumarNo ratings yet
- Web Dispatcher SSL Trust ConfigurationDocument14 pagesWeb Dispatcher SSL Trust Configurationspacnav100% (1)
- Cisco Expressway Authenticating Accounts Using LDAP Deployment Guide X8 5Document19 pagesCisco Expressway Authenticating Accounts Using LDAP Deployment Guide X8 5Alvaro ReyesNo ratings yet
- Configuring An LDAP AAA Server: Selected ASDM VPN Procedures, Version 5.2 (1) OL-10670-01Document14 pagesConfiguring An LDAP AAA Server: Selected ASDM VPN Procedures, Version 5.2 (1) OL-10670-01Khalil NiniNo ratings yet
- Configure Ldap On RouterDocument18 pagesConfigure Ldap On RouterEnis ByciNo ratings yet
- Configure External Server for AAADocument40 pagesConfigure External Server for AAAPape_Alie_Thia_8072No ratings yet
- Cisco AsaDocument12 pagesCisco AsaStyve PolaNo ratings yet
- Configure External AAA Server VPNDocument14 pagesConfigure External AAA Server VPNKeny Oscar Cortes GonzalezNo ratings yet
- Set up EAP-TLS wireless authentication with NPS RADIUS serverDocument29 pagesSet up EAP-TLS wireless authentication with NPS RADIUS serverpedirstuffNo ratings yet
- Blue Coat Security First Steps: Solution For Integrating Authentication Using LDAPDocument17 pagesBlue Coat Security First Steps: Solution For Integrating Authentication Using LDAPEmilioNo ratings yet
- EAP Authentication With RADIUS ServerDocument13 pagesEAP Authentication With RADIUS ServerlancethNo ratings yet
- Obiee - LdapDocument8 pagesObiee - Ldapvenkatesh.gollaNo ratings yet
- Cisco ASA IPSec VPN With LoginTC Two Factor Authentication For VPN With IPSec AlternativeDocument22 pagesCisco ASA IPSec VPN With LoginTC Two Factor Authentication For VPN With IPSec AlternativeRatheesh RavindranNo ratings yet
- Research Paper On Radius ServerDocument8 pagesResearch Paper On Radius Serverfzfgkws3100% (1)
- Cisco ISE Links Documents (Merged)Document418 pagesCisco ISE Links Documents (Merged)Haris Khan100% (1)
- Clientless SSL VPN Access PDFDocument31 pagesClientless SSL VPN Access PDFJWilhNo ratings yet
- RadiusDocument7 pagesRadiusMatias A Badal M.No ratings yet
- Configure L2TP Over IPsec Between WindowDocument28 pagesConfigure L2TP Over IPsec Between WindowAkram AlqadasiNo ratings yet
- 4tress As Radius Web Token and Cisco Asa Integration v1.1Document34 pages4tress As Radius Web Token and Cisco Asa Integration v1.1mahmedha78No ratings yet
- Configure Centralizd Ldap + SSH Authentication Server in Linux EnvironmentDocument4 pagesConfigure Centralizd Ldap + SSH Authentication Server in Linux Environmentultimatearun123No ratings yet
- LdapDocument2 pagesLdapLuziaGomesNo ratings yet
- Authentication, Authorization, and Accounting (AAA)Document20 pagesAuthentication, Authorization, and Accounting (AAA)Hafizh MaulidanNo ratings yet
- Configuring RADIUS Authentication With WPA2-EnterpriseDocument13 pagesConfiguring RADIUS Authentication With WPA2-EnterpriseJean Jacques BelyNo ratings yet
- Create a Two Server ADFS LabDocument2 pagesCreate a Two Server ADFS LabDisha1No ratings yet
- Configuring MAC-Based Authentication On A Switch Through The Command Line InterfaceDocument14 pagesConfiguring MAC-Based Authentication On A Switch Through The Command Line InterfaceBuba HanakoyeNo ratings yet
- Aindumps.70 411.v2015 09 21 PDFDocument631 pagesAindumps.70 411.v2015 09 21 PDFolfa0No ratings yet
- Configuring RADIUS: Layer 3 SolutionsDocument36 pagesConfiguring RADIUS: Layer 3 SolutionsBrian FrenchNo ratings yet
- Configure NPS Radius for 802.1X Wired and Wireless AccessDocument39 pagesConfigure NPS Radius for 802.1X Wired and Wireless AccessBlueilNo ratings yet
- How To Enable LDAP Authentication: Classification: (Protected)Document11 pagesHow To Enable LDAP Authentication: Classification: (Protected)tran lanNo ratings yet
- Integrating Active Directory With Sign-On Splash PageDocument6 pagesIntegrating Active Directory With Sign-On Splash PageSenan AlkaabyNo ratings yet
- Set up FreeRADIUS for Active Directory authenticationDocument20 pagesSet up FreeRADIUS for Active Directory authenticationcpasgraveNo ratings yet
- Authenticating Outgoing Web Proxy Requests With RADIUS in ISA Server 2004Document9 pagesAuthenticating Outgoing Web Proxy Requests With RADIUS in ISA Server 2004MunimAkhtarChoudhuryNo ratings yet
- Publish OWA Using FortiWebDocument8 pagesPublish OWA Using FortiWebevaNo ratings yet
- Setup LDAP Server in Ubuntu & Configure in BMCDocument23 pagesSetup LDAP Server in Ubuntu & Configure in BMCPreethi Kalaiselvam100% (1)
- Task Setup Free Radius Server - Draft - enDocument5 pagesTask Setup Free Radius Server - Draft - enTaqi DeenNo ratings yet
- JRadiusSimulator CoovaRADIUS TestingDocument13 pagesJRadiusSimulator CoovaRADIUS TestingAmanda LewisNo ratings yet
- SAS Security Administration GuideDocument265 pagesSAS Security Administration GuideMrYenThanhNo ratings yet
- SQL Server 2019 High Availability (SQL Server Simplified)Document171 pagesSQL Server 2019 High Availability (SQL Server Simplified)amit_post2000No ratings yet
- Cisco Systems, Inc.: Rsa Securid Ready Implementation GuideDocument31 pagesCisco Systems, Inc.: Rsa Securid Ready Implementation Guidecharming_chum88No ratings yet
- Aaa RadiusDocument20 pagesAaa RadiusWill TohallinoNo ratings yet
- LDAP Authentication For 3PAR InServs PDFDocument5 pagesLDAP Authentication For 3PAR InServs PDFShawn PrafulNo ratings yet
- vtiger LDAP Integration: SEO-Optimized TitleDocument12 pagesvtiger LDAP Integration: SEO-Optimized TitlednthuanNo ratings yet
- Cisco Asa Black Shield IDDocument12 pagesCisco Asa Black Shield ID8johnwongNo ratings yet
- Vfront Install File in English v0.99.3Document11 pagesVfront Install File in English v0.99.3njwscribdNo ratings yet
- Ccna Security Ch7 Implementing Aaa Using Ios ACS ServerDocument28 pagesCcna Security Ch7 Implementing Aaa Using Ios ACS Serverflorinn81No ratings yet
- Exacqvision Active DirectoryDocument14 pagesExacqvision Active Directoryafcn72No ratings yet
- Radius Single Sign On RssoDocument10 pagesRadius Single Sign On Rssoliving4it.peNo ratings yet
- Auto ProxyDocument56 pagesAuto ProxySumit AgrawalNo ratings yet
- Connect To SQL Server Using SQL Authentication in ASP - Net 2.0Document11 pagesConnect To SQL Server Using SQL Authentication in ASP - Net 2.0pawanmudgalNo ratings yet
- PEAP Under Unified Wireless Networks With Microsoft Internet Authentication ServiceDocument63 pagesPEAP Under Unified Wireless Networks With Microsoft Internet Authentication ServicesaurabhsareenNo ratings yet
- Configuring SSL For SAP Host Agent On Windows - SAP Host Agent - SAP LibraryDocument3 pagesConfiguring SSL For SAP Host Agent On Windows - SAP Host Agent - SAP LibraryLokesh GrcNo ratings yet
- LDAP Implementation HOWTODocument11 pagesLDAP Implementation HOWTOcodety CODETYNo ratings yet
- Chapter 3: AAADocument82 pagesChapter 3: AAARyanb378No ratings yet
- Cisco Aironet 1530 Series Outdoor Access Point: Sleek, Innovative, Flexible, ProvenDocument9 pagesCisco Aironet 1530 Series Outdoor Access Point: Sleek, Innovative, Flexible, Provenj_benz44No ratings yet
- Configure WGB 00 PDFDocument7 pagesConfigure WGB 00 PDFj_benz44No ratings yet
- Call Manager OptionsDocument4 pagesCall Manager Optionsj_benz44No ratings yet
- Configure WGB 00 PDFDocument7 pagesConfigure WGB 00 PDFj_benz44No ratings yet
- Extendair (TDD) Series: Digital Microwave Radios Installation and Management GuideDocument148 pagesExtendair (TDD) Series: Digital Microwave Radios Installation and Management Guidej_benz44No ratings yet
- Xenserver Installation Guide: 5.5.0 Update 2Document41 pagesXenserver Installation Guide: 5.5.0 Update 2vnkvijayNo ratings yet
- Extendair (TDD) Series: Digital Microwave Radios Installation and Management GuideDocument148 pagesExtendair (TDD) Series: Digital Microwave Radios Installation and Management Guidej_benz44No ratings yet
- Test Case ID Test Case No. Test Case Description Pre-ConditionsDocument7 pagesTest Case ID Test Case No. Test Case Description Pre-ConditionsTanuja VermaNo ratings yet
- 3424 Radius Auth Using Msserver PDFDocument6 pages3424 Radius Auth Using Msserver PDFJosé Nelson GuindoNo ratings yet
- Book 2Document1 pageBook 2Mintu PoddarNo ratings yet
- CCNA Security 210-260Document2 pagesCCNA Security 210-260Chris BuenaventuraNo ratings yet
- How To Configure A Brocade Silkworm Series SwitchDocument6 pagesHow To Configure A Brocade Silkworm Series SwitchgmawoyoNo ratings yet
- New Regedit Romnci - RegDocument8 pagesNew Regedit Romnci - Regkhaled zouaghi100% (1)
- VMM 2012 Powershell Cmdlets - : Get-Command - Module VirtualmachinemanagerDocument3 pagesVMM 2012 Powershell Cmdlets - : Get-Command - Module VirtualmachinemanagerGabriel Vallejos MartínNo ratings yet
- SlavaSoft Checksum Utility FilesDocument63 pagesSlavaSoft Checksum Utility FilesbrunoNo ratings yet
- Mingw64: Clonar El Repositorio Creado en La Nube en La PC Loca / Conexión RemotaDocument6 pagesMingw64: Clonar El Repositorio Creado en La Nube en La PC Loca / Conexión RemotaFredSpinozaCamposNo ratings yet
- Debug 1214Document4 pagesDebug 1214Hafiz NaimNo ratings yet
- Ping BasebandDocument3 pagesPing BasebandBeat HackerNo ratings yet
- Code1 by Kingg - OneDocument10 pagesCode1 by Kingg - OneHoñëy BhättiNo ratings yet
- X PH 3Document4 pagesX PH 3Regy YudhawiratamaNo ratings yet
- Increase Form: "User32.Dll" "Releasecapture"Document5 pagesIncrease Form: "User32.Dll" "Releasecapture"Rayleigh 05No ratings yet
- ACS Configuration ExamplesDocument21 pagesACS Configuration ExamplesVirender KumarNo ratings yet
- PTC Install LogDocument2 pagesPTC Install Logshrawan0908No ratings yet
- TBCDocument3 pagesTBCMARIO AYUBANNo ratings yet
- 70-411 R2 Test Bank Lesson 15Document11 pages70-411 R2 Test Bank Lesson 15Mazaher MohamedaliNo ratings yet
- Single Sign-On Implementation Guide: Salesforce, Summer '21Document78 pagesSingle Sign-On Implementation Guide: Salesforce, Summer '21Kayu manisNo ratings yet
- API Gateway APISIX Integrates Keycloak For Authentication - Apache APISIX - Cloud-Native API GatewayDocument11 pagesAPI Gateway APISIX Integrates Keycloak For Authentication - Apache APISIX - Cloud-Native API Gatewayhisyam darwisNo ratings yet
- Voucher-Bos Muda-7-Hari - 20rb-Up-418-11.21.22Document3 pagesVoucher-Bos Muda-7-Hari - 20rb-Up-418-11.21.22Ach rodli wildaniNo ratings yet
- RIP PresentationDocument43 pagesRIP PresentationNarendra KishoreNo ratings yet
- Ceng610 Lab 6Document4 pagesCeng610 Lab 6Kirolous FroukNo ratings yet
- ACN QB Chap3 - 103558Document3 pagesACN QB Chap3 - 103558Ramesh PotbhareNo ratings yet
- Account Activation Kotak SecuritiesDocument5 pagesAccount Activation Kotak SecuritiesShashank ChandraNo ratings yet
- How To Configure Siteminder Single Sign-On (Sso) : Barracuda Web Application FirewallDocument6 pagesHow To Configure Siteminder Single Sign-On (Sso) : Barracuda Web Application FirewallHoyamu BalamuNo ratings yet
- Cyberark 1Document121 pagesCyberark 1fransiscu100% (1)
- Optimize Windows SettingsDocument4 pagesOptimize Windows SettingssmokeZ12100% (1)