Professional Documents
Culture Documents
CCNAS v1.1 Skills-Based Assessment Hands On Answers
Uploaded by
David BondOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
CCNAS v1.1 Skills-Based Assessment Hands On Answers
Uploaded by
David BondCopyright:
Available Formats
Upload <http://www.scribd.com/upload-document> Log In <https://www.scribd.com/login> Sign up <https://www.scribd.com/login> <http://www.scribd.
com/> View all search results Browse </browse/books> Books </browse/Books> Biography <http://www.scribd.com/browse/Books/Biography-Autobiography>Business <http://www.scribd.com/browse/Books/Business-Economics>Cookbooks & Food <http://www.scribd.com/browse/Books/Cooking>Fiction & Literature <http://www.scribd.com/browse/Books/Fiction>History <http://www.scribd.com/browse/Books/History>Hobbies, Crafts, & Home <http://www.scribd.com/browse/Books/Hobbies-Crafts-and-Home>Kids & Teens <http://www.scribd.com/browse/Books/Kids-Teens>Mystery & Detective <http://www.scribd.com/browse/Books/Fiction/Mystery-Detective>Religion <http://www.scribd.com/browse/Books/Religion>Romance <http://www.scribd.com/browse/Books/Fiction/Romance1>Science Fiction <http://www.scribd.com/browse/Books/Fiction/Science-Fiction1> Other Content </browse> Brochures & Catalogs <http://www.scribd.com/browse/Types/BrochuresCatalogs>Court Filings <http://www.scribd.com/browse/BusinessLaw/Court-Filings>Creative Writing <http://www.scribd.com/browse/Types/Creative-Writing>Forms <http://www.scribd.com/browse/Types/Forms>How-To Guides/Manuals <http://www.scribd.com/browse/Types/HowTo-GuidesManuals>Maps <http://www.scribd.com/browse/Types/Maps>Posters <http://www.scribd.com/browse/Types/Graphic%20Art>Presentations <http://www.scribd.com/browse/Presentations>Recipes/Menus <http://www.scribd.com/browse/Types/RecipesMenus>School Work <http://www.scribd.com/browse/Types/School-Work> My Library </my-library> Recently Saved </my-library> Loading... Go to My Library </my-library> Welcome to Scribd, the world's digital library. Read, publish, and share books and documents. See more <http://www.scribd.com/> Download <#> Standard view Full view of 18 Add note Save to My Library Sync to mobile Look up keyword Like this Share on social networks 1Activity There was a problem sending you an sms. Check your phone number or try again later. To get Scribd mobile enter your number and we'll send you a link to the Scribd app for iPhone & Android. We've sent a link to the Scribd app. If you didn't receive it, try again.
Text me We'll never share your phone number. iTunes App Store <https://itunes.apple.com/us/app/scribd-worlds-largest-online/id542557212?mt=8#> | Google Play Store <https://play.google.com/store/apps/details?id=com.scribd.app.reader0&hl=en> Share to your social networks. Tweet <https://twitter.com/share> Embed 0of . Results for: No results containing your search query P. 18 CCNAS v1.1 Skills-Based Assessment Hands on Answers CCNAS v1.1 Skills-Based Assessment Hands on Answers Ratings: 0|Views: 474|Likes: 0 Published by Adelaide-City South Australia <http://www.scribd.com/adelaide_citya> CCNA Security 1.1 CCNA Security 1.1 More info: categoriesTopics <http://www.scribd.com/browse/Topics> Published by: Adelaide-City South Australia <http://www.scribd.com/adelaide_citya> on Oct 13, 2013 Copyright:Attribution Non-commercial Availability: Read on Scribd mobile: iPhone <https://itunes.apple.com/us/app/scribd-worlds-largest-online/id542557212?mt=8#> , iPad <https://itunes.apple.com/us/app/scribd-worlds-largest-online/id542557212?mt=8#> and Android <https://play.google.com/store/apps/details?id=com.scribd.app.reader0&hl=en>. Free download as PDF, TXT or read online for free from Scribd Flag for inappropriate content|Add to collection <#> See More See less http://www.scribd.com/doc/175689839/CCNAS-v1-1-Skills-Based-Assessment-Hands-onAnswers 10/31/2013
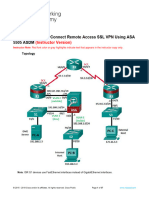
pdf text original All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 10 CCNA Security Skills-Based AssessmentStudent Academy Training Topology IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 FA0/0 209.165.200.233 255.255.255.248 N/A ASA E0/0S0/0/0(DCE)10.10.10.1 255.255.255.252 N/A N/ALoopback 1 172.20.1.1 255.255.255.0 N/A N/.AR2 S0/0/0 10.10.10.2 255.255.255.252 N/A N/AS0/0/1(DCE)10.20.20.2 255.255.255.252 N/A N/AR3 FA0/1 172.30.3.1 255.255.255.0 N/A S3 FA0/5S0/0/1 10.20.20.1 255.255.255.252 N/A N/A All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 2 of 10 CCNA Security Device Interface IP Address Subnet Mask Default Gateway Switch Port S1 VLAN 1 192.168.10.11 255.255.255.0 192.168.10.1 N/AS2 VLAN 1 192.168.10.12 255.255.255.0 192.168.10.1 N/AS3 VLAN 1 172.30.3.11 255.255.255.0 172.30.3.1 N/A ASAVLAN 1(E0/1)192.168.10.1 255.255.255.0 NA S2 FA0/24 ASAVLAN 2(E0/0)209.165.200.234 255.255.255.248 NA R1 FA0/0PC-A NIC 192.168.10.2 255.255.255.0 192.168.10.1 S1 FA0/6PC-B NIC 192.168.10.3 255.255.255.0 192.168.10.1 S2 FA0/18PC-C NIC 172.30.3.3 255.255.255.0 172.30.3.1 S3 FA0/18
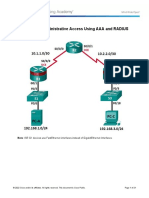
Objectives Part 1: Verify Basic Device Settings Part 2: Configure Secure Router Administrative Access Configure encrypted passwords and a login banner. Configure EXEC timeout on console and VTY lines. Configure login failure rates and VTY login enhancements. Configure SSH access and disable Telnet. Configure RADIUS/TACACS+/Local AAA authentication. Part 3: Configure a Site-to-Site VPN between ISRs Configure an IPsec site-to-site VPN between R1 and R3 using CCP. Part 4: Configure an ISR firewall and Intrusion Prevention System Configure a zone-based policy (ZPF) firewall on an ISR using CCP. Configure an Intrusion Prevention System (IPS) on an ISR using CCP. Part 5: Secure Network Switches Configure passwords and a login banner. Configure management VLAN access. Secure trunk ports. Secure access ports. Protect against STP attacks. Configure port security and disable unused ports. Part 6: Configure ASA Basic Settings and Firewall
Configure basic settings, passwords, date and time. Configure the inside and outside VLAN interfaces. Configure port address translation (PAT) for the inside network. Configure a DHCP server for the inside network. All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 3 of 10 CCNA Security Configure administrative access via Telnet and SSH. Configure a static default route for the ASA. Configure RADIUS/TACACS+/Local AAA user authentication. Verify address translation and firewall functionality Part 7: Configure ASA AnyConnect SSL VPN Remote Access Configure a remote access AnyConnect SSL VPN using ASDM. Verify AnyConnect SSL VPN access to the portal. Exam Overview The Case Study is divided into six parts. The parts should be completed sequentially. In Part 1 you verify thatthe basic device settings have been preconfigured by your group. In Part 2, you secure a network router usingthe CLI to configure various IOS features including AAA and SSH. In Part 3 you configure a site-to-site VPNbetween R1 and R3 through the ISP router (R2). In Part 4 you configure a ZPF firewall and IPS on an ISR.Part 5 configures network switches using the CLI. In Parts 6 and 7 you configure the ASA firewall functionalityand Anyconnect SSL VPN remote access. Part 1: Verify Basic Device Settings Network cabled as shown in the topology. Basic settings for all routers configured. o
Host names, interface IP addresses, serial interface DCE clock rate. ** Host names and interface IP addresses >> Refer to table above! R1(config)#interface S0/0/0R1(config-if)#clock rate 64000R2(config)#interface S0/0/1R2(config-if)#clock rate 64000 o DNS lookup disabled on each router. R1(config)#no ip domain-lookupR2(config)#no ip domain-lookupR3(config)#no ip domain-lookup Static default routes on routers R1, R2 and R3 configured. o Static default route from R1 to R2 and from R3 to R2. R1(config)#ip route 0.0.0.0 0.0.0.0 10.10.10.2R3(config)#ip route 0.0.0.0 0.0.0.0 10.20.20.2 o Static routes from R2 to the R1 simulated LAN (Loopback 1), the R1 Fa0/0-to-ASA subnet andthe R3 LAN. R2(config)#ip route 10.10.10.2 255.255.255.0 172.20.1.1R1(config)#ip route 209.165.200.233 255.255.255.248 172.30.3.1 Basic settings for each switch configured. o Host names, VLAN 1 management address, IP default gateway. All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 4 of 10 CCNA Security S1(config)#interface vlan 1S1(config)#ip address 192.168.10.11 255.255.255.0S1(config)#no shutdownS1(config)#ip default-gateway 192.168.10.1S2(config)#interface vlan 1S2(config)#ip address 192.168.10.12 255.255.255.0S2(config)#no shutdownS2(config)#ip default-gateway 192.168.10.1S3(config)#interface vlan 1S3(config)#ip address 172.30.3.11 255.255.255.0S3(config)#no shutdownS3(config)#ip default-gateway 172.30.3.1 o DNS lookup disabled on each switch. S1(config)#no ip domain-lookupS2(config)#no ip domain-lookupS3(config)#no ip domain-lookup PC host IP settings configured. o Static IP address, subnet mask, and default gateway for each PC. >>> refer to the table above! Verify connectivity between PC-C and R1 Lo1 and Fa0/0. On PC-C
>> ping 172.20.1.1 (loopback 1)>> ping 209.165.200.233 (R1 Fa0/0) Part 2: Configure Secure Router Administrative Access Task 1: Configure Settings for R1 and R2. Step 1: Configure a minimum password length of 10 characters on R1. R1(config)#security passwords min-length 10 Step 2: Configure the enable secret password on R1. Use an enable secret password of ciscoenapa55 . R1(config)#enable secret ciscoenapa55 Step 3: Encrypt plaintext passwords on R1. R1(config)#service password-encryption Step 4: Configure the console lines on R1. Configure a console password of ciscoconpa55 and enable login. Set the exec-timeout to log out after 15 minutes of inactivity. Prevent console messages from interrupting command entry. Note: The vty lines for R1 are configured for SSH in Task 3. All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 5 of 10 CCNA Security R1(config)#line console 0R1(config-line)#password ciscoconpa55R1(config-line)#exec-timeout 15 0R1(config-line)#loginR1(config-line)#logging synchronous Step 5: Configure a login warning banner on R1. Configure a warning to unauthorized users with a message-of-the-day (MOTD) banner that says:Unauthorized access strictly prohibited and prosecuted to the full extent of the law!. R1(config)#banner motd $ Unauthorized access strictly prohibited and prosecuted to the full extent of the law!$ Step 6: Configure the vty lines and enable password on R2. a. Configure the password for vty lines to be ciscovtypa55 and enable login. Set the exec-timeout so asession is logged out after 15 minutes of inactivity. R2(config)#line vty 0 4R2(config-line)#password ciscovtypa55R2(config-line)#exec-timeout 15 0R2(config-line)#login b. Use an enable secret password of ciscoenapa55 . R2(config)#enable secret ciscoenapa55 Step 7: Enable HTTP access on router R2. Enable the HTTP server on R2 to simulate an Internet target for later testing. R2(config)#ip http server Task 2: Configure Local Authentication with AAA on R1.
Step 1: Configure the local user database. Create a local user account of Admin01 with a secret password of Admin01pa55 and a privilege level of 15 . R1(config)#username Admin01 privilege 15 secret Admin01pa55 Step 2: Enable AAA services. R1(config)#aaa new-model Step 3: Implement AAA services using RADIUS/TACACS+/local database. Create the default login authentication method list using RADIUS as the first option, TACACS+ as thesecond option, and case-sensitive local authentication as the third option and the enable password as thebackup option to use if an error occurs in relation to local authentication. R1(config)#aaa authentication login default group radius enableR1(config)#aaa authentication login default group tacacs+ enableR1(config)#aaa authentication login default local enable All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 6 of 10 CCNA Security Task 3: Configure the SSH Server on Router R1. Step 1: Configure the domain name ccnasecurity.com . R1(config)#ip domain-name ccnasecurity.com Step 2: Configure the incoming vty lines. Specify that the router vty lines will accept only SSH connections. R1(config)#line vty 0 4R1(config-line)#transport input sshR1(config-line)#exit Step 3: Generate the RSA encryption key pair. Configure the RSA keys with 1024 as the number of modulus bits. R1(config)#crypto key generate rsa general-keys modulus 1024 Step 4: Configure the SSH version. Specify that the router accept only SSH version 2 connections. R1#show ip ssh Step 5: Verify SSH connectivity to R1 from PC-C. Launch the SSH client on PC-C and test SSH connectivity to R1 and login in as Admin01 with thepassword Admin01pa55 . Server: ccnasecurity.com
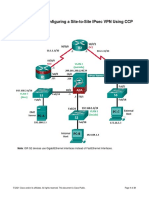
Port: 22 Username: Admin01 Password: Admin01pa55 Task 4: Secure against login attacks on R1. Step 1: Configure enhanced login security on R1. If a user fails to login twice within a 30 second time span, then disable logins for 1 minute. Log all failedlogin attempts. R1(config)#login on-failure log Part 3: Configure a Site-to-Site IPsec VPN between ISRs In Part 3 of this SBA, you use CCP to configure an IPsec VPN tunnel between R1 and R3 that passesthrough R2. Task 1: Configure the site-to-site VPN between R1 and R3. Step 1: Configure the enable secret password and HTTP access on R3 prior to starting CCP . a. From the CLI, configure an enable secret password of ciscoenapa55 for use with CCP on R3. R3(config)#enable secret ciscoenapa55 All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 7 of 10 CCNA Security b. Enable the HTTP server on R3. R3(config)# ip http server c. Add user Admin01 to the local database with a privileged level of 15, and a password of Admin01pa55 . R3(config)# username Admin01 privilege 15 secret Admin01pa55 d. Configure local database authentication of HTTP sessions. R3(config)# ip http authentication local Step 2: Access CCP and discover R3. From PC-C run CCP and access R3. o Manage Devices window > R3 IP address 172.30.3.1 in the first IP address field. o
Enter Admin01 in the Username field, and Admin01pa55 in the Password field. o At the CCP Dashboard, click the Discover button to discover and connect to R3. Step 3: Use the CCP VPN wizard to configure R3. Use the Quick Setup option to configure the R3 side of the site-to-site VPN. Click the Configure button at the top of the CCP screen. Choose Security > VPN > Site-to-Site VPN. Click the Launch the selected task button to begin the CCP Site-to-Site VPN wizard. From the initial Site-to-Site VPN wizard screen, choose the Step by step wizard, and then click Next . Step 4: Configure basic VPN connection information settings. a. Specify R3 S0/0/1 as the interface for the connection and R1 interface S0/0/0 as the remote peer static IP address. On the VPN Connection Information screen, select the interface for the connection, whichshould be R3 Serial0/0/1 . In the Peer Identity section, select Peer with static IP address and enter the IP address of the remote peer, R1 interface S0/0/0 , which is 10.10.10.1 .b. Specify the pre-shared VPN key cisco12345 . In the Authentication section, click Pre-shared Keys , and enter the pre-shared VPN key
cisco12345 . Re-enter the key for confirmation. Click Next to continue.c. Encrypt traffic between the R3 LAN and the R1 Loopback 1 simulated LAN. On the IKE Proposals screen, click Next to continue. On the Transform Set screen, click Next to continue. On the Traffic to protect screen, enter the following information; Local Network (R3 LAN) Remote Network (R1 Loopback) IP address: 172.30.3.1 Subnet Mask: 255.255.255.0 IP address: 172.20.1.1 Subnet Mask: 255.255.255.0 Click Next to continue. All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 8 of 10 CCNA Security Review the Summary of the Configuration screen. You can scroll down to see the IPsec rule(ACL) that CCP creates for R3, which permits all traffic from network 172.30.3.1/24 to network 172.20.1.1/24 . Click Finish to go to the Deliver Configuration to Device screen. On the Deliver Configuration to Device screen, select Save running config. to device's startupconfig,
and click the Deliver button. After the commands have been delivered, click OK .To save these configuration commands for later editing or documentation purposes; Click Save to file button. Step 5: Generate a mirror configuration from R3 and apply it to R1. a. On R3, generate a mirror configuration for application to router R1 and save it to the desktop or flashdrive. Edit the file as necessary and apply the mirrored commands to R1.On R3 Click the Configure button at the top of the CCP screen. Choose Security > VPN > Site-to-Site VPN. Click the Edit Site to Site VPN tab. Select the VPN policy you just configured on R1 and click the Generate Mirror button in thelower right of the window.The Generate Mirror window displays the commands necessary to configure R3 as a VPN peer.Scroll through the window to see all the commands generated. Click the Save button to create a text file. Name it VPN-Mirror-Cfg-for-R3.txt .b. Apply the crypto map to the R1 VPN interface. On R1, enter privileged EXEC mode and then global config mode. Copy the commands from the text file into the R1 CLI.To apply the crypto map to R1 VPN interface, enter the following; R1(config)#interface S0/0/0R1(config-if)#crypto map SDM_CMAP_1 Task 2: Test the Site-to-Site IPsec VPN using CCP a. On R3 (PC-C), use CCP to test the IPsec VPN tunnel between the two routers. Security > VPN > Site-to-Site VPN and click the Edit Site-to-Site VPN tab. From the Edit Site to Site VPN tab, choose the VPN and click Test Tunnel . VPN Troubleshooting window displays, click the Start
button to start troubleshooting the tunnel. Click Yes to continue when the CCP Warning window is displayed. In the next VPN Troubleshooting window, enter the IP address of the R3 Fa0/1 interface in thedestination network field ( 172.30.3.1 ) and click Continue to begin the debugging process. If successful, click Save Report . Click Close when you're finished.b. Ping from PC-C to the R1 Lo1 interface at 172.16.1.1 to generate some interesting traffic. On PC-C >> ping 172.16.1.1 c. Issue the show crypto isakmp sa command on R3 to view the security association created. R3# show crypto isakmp sa All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 9 of 10 CCNA Security d. Issue the show crypto ipsec sa command on R1 to verify packets are being received from R3and decrypted by R1. R1# show crypto isakmp sa Part 4: Configure an ISR Firewall and Intrusion Prevention System In Part 4, you configure a zone-based policy firewall and IPS on R3 using CCP. Task 1: Configure a ZPF Firewall on R3 using CCP. Step 1: Use the CCP Firewall wizard to configure a zone-based firewall. a. Configure a Basic firewall with Fa0/1 interface as the Inside interface and S0/0/1 as the Outside interface.
Configure > Security > Firewall > Firewall. Select Basic Firewall . Click the Launch the selected task button. Click Next to continue. Check the Inside (trusted) check box for Fast Ethernet0/1 and the Outside (untrusted) checkbox for Serial0/0/1 . Click Next . Click OK when the warning is displayed informing you that you cannot launch CCP from theS0/0/1 interface after the Firewall wizard completes.b. Use the Low Security setting, and complete the Firewall wizard. Move the slider to Low Security and click the Preview Commands button to preview thecommands that are delivered to the router. Click Next to continue. On the Review the Firewall Configuration Summary screen, click Finish to complete theFirewall wizard. Step 2: Verify Firewall functionality. a. From PC-C, ping external router R2. The pings should be successful.>> ping 10.20.20.2b. From external router R2, ping PC-C. The pings should NOT be successful.>> ping 172.30.3.3 Task 2: Configure IPS on R3 Using CCP. Step 1: Prepare router R3 and the TFTP server. To configure Cisco IOS IPS 5.x, the IOS IPS signature package file and public crypto key files must beavailable on the PC with the TFTP server installed. R3 uses PC-C as the TFTP server. Check with your instructor if these files are not on the PC.
Install TFTP Server application on PC-Ca. Verify that the IOS-Sxxx-CLI.pkg signature package file is in the default TFTP folder. The xxx is theversion number and varies depending on which file was downloaded from Cisco.com.b. Verify that the realm-cisco.pub.key.txt file is available and note its location on PC-C. All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 10 of 10 CCNA Security c. Verify or create the IPS directory, ipsdir , in router flash on R3. R3#mkdir ipsdirR3#dir flash: Note: For router R3, the IPS signature (.xml) files in the flash:/ipsdir/ directory should have been deletedand the directory removed prior to starting the SBA. The files must be deleted from the directory in order to remove it. Note: If the ipsdir directory is listed and there are files in it, contact your instructor. This directory must beempty before configuring IPS. If there are no files in it you may proceed to configure IPS. Step 2: Access CCP and discover R3 (if required). Specify Admin01 as the username and Admin01pa55 as the password. In the Manage Devices window add R3 IP address 172.30.3.1 in the first IP address field. Enter Admin01 in the Username field, and Admin01pa55 in the Password field. At the CCP Dashboard , click the Discover button to discover and connect to R3. If discoveryfails, click the Discovery Details button to determine the problem. Step 3: Use the CCP IPS wizard to configure IPS. a. Launch the IPS wizard and apply the IPS rule in the inbound direction for Serial0/0/1.
Click the Configure button at the top of the CCP screen. Choose Security > Intrusion Prevention > Create IPS. Click Launch IPS Rule Wizard . Click Next to continue. In the Select Interfaces window, check the Inbound check box for Fast Ethernet0/1 andSerial0/0/1. Click Next .b. Specify the signature file with a URL and use TFTP to retrieve the file from PC-C. Signature File and Public Key window, click the ellipsis () button next to Specify theSignature File You Want to Use with IOS IPS to open the Specify Signature File window.Confirm that the Specify signature file using URL option is chosen. For Protocol, select tftp from the drop-down menu. Enter the IP address of the PC-C TFTP server and the filename. The address is 172.30.3.3/IOS-Sxxx-CLI.pkg (where xxx is the number of the package) Click OK to return to the Signature File and Public Key window.c. Name the public key file realm-cisco.pub . In the Configure Public Key section of the Signature File and Public Key window,enter realm-cisco.pub in the Name field.d. Copy the text from the public key file to the CCP IPS wizard. Open the realm-cisco-pub-key.txt file located on PC-C.
Copy the text between the phrase key-string and the word quit into the Key field in the ConfigurePublic Key section. Click Next to display the Config Location and Category window.e. Specify the flash:/ipsdir/ directory name as the location to store the signature information. In the Config Location and Category window in the Config Location section, clickthe ellipsis (...) button next to Config Location to add the location. Verify that Specify the config location on this router is selected. Click the ellipsis (...) button. All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 11 of 10 CCNA Security Click the plus sign (+) next to flash. Choose ipsdir and then click OK.f. Choose the basic category. In the Choose Category field of the Config Location and Category window, choose basic .g. Complete the wizard. Click Next in the Cisco CCP IPS Policies Wizard window.
Click Finish in the IPS Policies Wizard window and review the commands that will be deliveredto the router. Click Deliver . Click OK when the Commands Deliver Status window is ready. When the signature configuration process has completed, you return to the IPS window with the Edit IPS tab selected. Part 5: Secure Network Switches Task 1: Configure Passwords and a Login Banner on S1. Step 1: Configure the enable secret password of ciscoenapa55. S1(config)#enable secret ciscoenapa55 Step 2: Encrypt plaintext passwords. S1(config)#service password-encryption Step 3: Configure the console and VTY lines. a. Configure a console password of ciscoconpa55 and set the exec-timeout to log out after 5 minutesof inactivity. Prevent console messages from interrupting command entry. S1(config)#line console 0S1(config-line)#password ciscoconpa55S1(config-line)#exec-timeout 5 0S1(config-line)#loginS1(config-line)#logging synchronous b. Configure a vty lines password of ciscovtypa55 and set the exec-timeout to log out after 5 minutes of inactivity. S1(config)#line vty 0 15S2(config-line)#password ciscovtypa55S2(config-line)#exec-timeout 5 0S2(config-line)#login Step 4: Configure a login warning banner. Configure a warning to unauthorized users with a message-of-the-day (MOTD) banner that saysUnauthorized access strictly prohibited and prosecuted to the full extent of the law!. S1(config)#banner motd $Unauthorized access strictly prohibited and prosecuted tothe full extent of the law!$ Step 5: Disable HTTP access. S1(config)#no http server All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 12 of 10 CCNA Security Task 2: Secure Trunk and Access Ports on S1 and S2.
Step 1: Configure trunk ports on S1 and S2. S1(config)#interface FastEthernet 0/1S1(config-if)#switchport mode trunkS2(config)#interface FastEthernet 0/1S2(config-if)#switchport mode trunk Step 2: Change the native VLAN to 99 for the trunk ports on S1 and S2. S1(config)#interface Fa0/1S1(config-if)#switchport trunk native vlan 99S1(config-if)#end S2(config)#interface Fa0/1S2(config-if)#switchport trunk native vlan 99S2(config-if)#end Step 3: Prevent the use of DTP on S1 and S2 trunk ports. S1(config)# interface Fa0/1 S1(config-if)# switchport nonegotiate S2(config)# interface Fa0/1 S2(config-if)# switchport nonegotiate Step 4: Verify the trunking configuration on S1 and S2. S1#show interface fa0/1 trunkS2#show interface fa0/1 trunk Step 5: Enable storm control for broadcasts on S1 and S2 trunk ports. S1(config)# interface FastEthernet 0/1 S1(config-if)# storm-control broadcast level 50 S2(config)# interface FastEthernet 0/1 S2(config-if)# storm-control broadcast level 50 Step 6: Disable trunking on S1 access ports that are in use. S1(config)# interface FastEthernet 0/1 S1(config-if)# switchport mode access S1(config)# interface FastEthernet 0/6 S1(config-if)# switchport mode access Step 7: Enable PortFast on S1 access ports that are in use. S1(config)# interface FastEthernet 0/1 S1(config-if)#spanning-tree portfast All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 13 of 10 CCNA Security S1(config)# interface FastEthernet 0/6 S1(config-if)#spanning-tree portfast Step 8: Enable BPDU guard on S1 access ports that are in use. S1(config)# interface FastEthernet 0/1 S1(config-if)# spanning-tree bpduguard enable S1(config)# interface FastEthernet 0/6 S1(config-if)# spanning-tree bpduguard enable
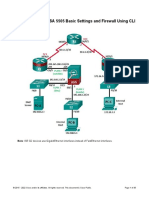
Task 3: Configure Port Security and Disable Unused Ports. Step 1: Configure basic port security for the S1 access port. Use the default port security options (set maximum MAC addresses to 1 and violation action to shutdown). Allow the secure MAC address that is dynamically learned on a port be added to the switch runningconfiguration. S1(config)# interface FastEthernet 0/1 S1(config-if)#shutdownS1(config-if)#switchport port-securityS1(config-if)#switchport port-security mac-address [your switch mac address]S1(config-if)#switchport port-security mac-address stickyS1(config-if)#no shutdown S1(config)# interface FastEthernet 0/6 S1(config-if)# shutdown S1(config-if)#switchport port-securityS1(config-if)#switchport port-security mac-address [your switch mac address]S1(config-if)#switchport port-security mac-address stickyS1(config-if)#no shutdown Step 2: Disable unused ports on S1. As a further security measure, disable any ports not being used. S1(config)#interface range FastEthernet 0/2-5S1(config)#shutdownS1(config)#interface range FastEthernet 0/7-24S1(config)#shutdown Part 6: Configure ASA Basic Settings and Firewall Task 1: Prepare the ASA for ASDM access. Step 1: Clear the previous ASA configuration settings. ciscoasa# write eraseciscoasa# show startciscoasa# reload Step 2: Bypass Setup Mode and configure the VLAN/routed interfaces using CLI. a. The VLAN 1 logical interface will be used by PC-B to access ASDM on ASA physical interface E0/1.Configure interface VLAN 1 and name it inside . Specify IP address 192.168.10.1 and subnet mask 255.255.255.0 . Verify that the security level is set to 100 . All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 14 of 10 CCNA Security ciscoasa(config)# interface vlan 1ciscoasa(config-if)# nameif insideINFO: Security level for "inside" set to 100 by default.ciscoasa(config-if)# ip address 192.168.10.1 255.255.255.0ciscoasa(config-if)# exit b. Pre-configure interface VLAN 2 and name it outside
, and add physical interface E0/0 to VLAN 2.You will assign the IP address using ASDM. Verify that the security level is set to 0 . ciscoasa(config)# interface vlan 2ciscoasa(config-if)# nameif outsideINFO: Security level for "outside" set to 0 by default.ciscoasa(config-if)# interface e0/0ciscoasa(config-if)# switchport access vlan 2ciscoasa(config-if)# no shutciscoasa(config-if)# exit c. Test Connectivity to the ASA by pinging from PC-B to ASA interface VLAN 1 IP address 192.168.10.1 . The pings should be successful. On PC-B >> ping 192.168.10.1 Step 3: Configure and verify access to the ASA from the inside network. a. Configure the ASA to accept HTTPS connections and to allow access to ASDM from any host on theinside network 192.168.10.0/24. ciscoasa(config)# http server enableciscoasa(config)# http 192.168.10.0 255.255.255.0 inside b. Open a browser on PC-B and test the HTTPS access to the ASA ASDM GUI. On PC-B >> https://192.168.10.1 Task 2: Configure basic ASA settings using the ASDM Startup Wizard. Step 1: Access the Configuration menu and launch the Startup wizard. Click the Configuration button at the top left of the screen. There are five main configuration areas: Device Setup Firewall Remote Access VPN Site-to-Site VPN Device Management Step 2: Configure hostname, domain name, and enable password. Configure the ASA host name CCNAS-ASA and domain name of ccnasecurity.com . Change the enablemode password to ciscoenapa55 . On first startup wizard >> ensure Modify Existing Configuration option is selected. All contents are Copyright 19922012 Cisco Systems, Inc. All rights
reserved. This document is Cisco Public Information. Page 15 of 10 CCNA Security On step 2 wizard screen, enter the following;Hostname: CCNAS-ASA Domain name: ccnasecurity.com Password: ciscoenapa55 << You must click the checkbox for changing the enable modepassword and change it from blank (no password) to ciscoenapa55 Step 3: Configure the outside VLAN interface. Enter an outside IP address of 209.165.200.234 and mask 255.255.255.248 . On step 3 wizard screen >> for Outside and Inside VLANs, do not change the current settings. For DMZ VLAN, select Do not configure button and uncheck Enable VLAN On step 4 wizard screen >> verify that port Ethernet1 is in Inside VLAN 1 and that port Ethernet0is in Outside VLAN 2. On step 5 wizard screen >> Interface IP Address Configuration, enter the following outside IPaddress:IP address: 209.165.200.234 Mask: 255.255.255.248 Step 4: Configure DHCP, address translation and administrative access. a. Enable the DHCP server on the Inside Interface and specify a starting IP address of 192.168.10.5 and ending IP address of 192.168.10.30 . Enter the DNS server 1 address of 10.3.3.3 and domainname ccnasecurity.com . On step 6 wizard screen >> select checkbox Enable DHCP server on the inside interface .Enter the following;Starting IP address: 192.168.10.5 Ending IP address: 192.168.10.30
DNS Server 1: 10.3.3.3 Domain Name: ccnasecurity.com b. Configure the ASA to use port address translation (PAT) address of the outside interface. On step 7 wizard screen >> Ensure Use Port Address Translation (PAT) and Use the IPaddress on the outside interface is selected only. c. Add Telnet access to the ASA for the inside network 192.168.10.0 with a subnet mask of 255.255.255.0 . Add SSH access to the ASA from host 172.30.3.3 on the outside network. On step 8 wizard screen >> Add the following entries >> Telnet Interface: inside IP address: 192.168.10.0 Mask: 255.255.255.0 Type: SSH Interface: outside IP address: 172.30.3.3 Mask: 255.255.255.255 Ensure that Enable HTTP server for HTTPS/ASDM access is checked. On step 9 wizard Startup Wizard Summary >> review the Finish. Restart ASDM and provide the new enable password ciscoenapa55 with no username . Return tothe Device Dashboard and check the Interface using the IP
Click Add.Type:
settings, click
Status window.
All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 16 of 10 CCNA Security Step 5: Test Telnet access to the ASA. a.
From a command prompt or GUI Telnet client on PC-B, Telnet to the ASA inside interface at IPaddress 192.168.10.1.>> telnet 192.168.10.1 Task 3: Configuring ASA Settings from the ASDM Configuration Menu. Step 1: Set the ASA Date and Time. Set the time zone, current date and time and apply the commands to the ASA. Configuration screen > Device Setup menu > System Time > Clock Select your Time Zone from drop-down menu > enter current date and time in the fieldsprovided. Click Apply to send the commands to the ASA. Step 2: Configure a static default route for the ASA. Add a static route for the outside interface and specify Any for the network object and a Gateway IP of 209.165.200.233 . Use Ping from the ASDM Tools menu to test connectivity to the IP address of router R1 S0/0/0 (10.10.10.1). The ping should succeed. From the ASDM Tools menu, select Ping and enter the IP address of router R1 S0/0/0(10.10.10.1).>> ASA does not have a default route to unknown external networks. The ping should fail becausethe ASA has no route to 10.10.10.1. Click Close to continue. Configuration screen > Device Setup menu > Routing > Static Routes. Click IPv4 Only buttonand click Add to add a new static route. In the Add Static Route dialogue box, choose the outside interface from the drop down menu. Click on the ellipsis button (. .) next to Network . Select Any
from the list of network objects, then click OK . The selection of Any translates to a quad zero route. For the Gateway IP, enter 209.165.200.233 Click OK and click Apply to send the commands to the ASA. Step 3: Test access to an external website from PC-B. Open a browser on PC-B and enter the IP address of the R2 S0/0/0 interface (10.10.10.2) to simulateaccess to an external website. The R2 HTTP server was previously enabled so you should be promptedwith a user authentication login dialog box from the R2 GUI device manger. Exit the browser. Open up browser > enter http://10.10.10.2 Step 4: Configure AAA for SSH client access. a. Create a new user named admin with a password of cisco123 . Allow this user Full access (ASDM,SSH, Telnet, and console) and set the privilege level to 15 . Configuration screen > Device Management area > click Users/AAA Click User Accounts and then Add . Create a new user named admin Enter cisco123 as the password and enter the password again to confirm it.
All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 17 of 10 CCNA Security Allow this user Full access (ASDM, SSH, Telnet, and console) under Access Restrictions. Set privilege level to 15 . Click OK to add the user and click Apply to send the command to the ASA. b. Require authentication for HTTP/ASDM, SSH and Telnet connections and specify the LOCALserver group for each connection type. Configuration screen > Device Management area > click Users/AAA Click AAA Access . On the Authentication tab, click the checkbox to require authentication for HTTP/ASDM,SSH and Telnet connections Specify the LOCAL server group for each enabled connection type. Click Apply to send the commands to the ASA. c. From P C-C, open an SSH client such as PuTTY and attempt to access the ASA outside interface at 209.165.200.234 . You should be able to establish the connection. Open PuTTY on PC-C > select the SSH option. Ensure the port number is
22 . Enter the IP address: 209.165.200.234 Part 7: Configure ASA AnyConnect SSL VPN Remote Access Step 1: Configure the SSL VPN user interface. Configure VPN-Con-Prof as the Connection Profile Name, and specify outside as the interface to whichoutside users will connect. On PC-B open up browser > type in: https://192.168.10.1 A security warning will appear about the website security certificate. Click Continue to thiswebsite . Click Yes for any other security warnings. At the ASDM welcome page, click the Run ASDM button. Login as user admin with password cisco123 . From the ASDM main menu, select Wizards > VPN Wizards > Clientless SSL VPN wizard . Click Next . On the SSL VPN Interface screen (Step 2 of 6), configure ClientlessVPN-Con-Prof as the Connection Profile Name , and specify outside as the interface to which outside users will connect.Click Next .
Step 2: Configure AAA user authentication. Use the local user database to authenticate remote access users and create a new user named VPNuser with a password of remote . On the User Authentication screen (Step 3 of 6) click Authenticate using the local user database button. Enter the username VPNuser and the password remote . Click Add to create the new user.Click Next to continue. Step 3: Configure the VPN group policy. Create a new group policy named VPN-Grp-Pol . On the Group Policy screen (Step 4 of 6) create a new group policy named VPN-Grp-Pol .Click Next to continue. All contents are Copyright 19922012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 18 of 10 CCNA Security Step 4: Configure the bookmark list . a. Add a bookmark list and name it WebServer-XX (where XX is your initials). From the Clientless Connections Only Bookmark List screen (Step 5 of 6) click the Manage button to create an HTTP server bookmark. In the Configure GUI Customization Objects window, click Add to open the Add Bookmark List window. Name the list Web-Server-XX .>> FROM HERE DO NOT CLICK
OK YET!b. Add a new Bookmark with Web Mail as the Bookmark Title. Specify the server destination IP addressof PC-B 192.168.10.3 (simulating a web server). From the Add Bookmark List window, click Add to open the Add Bookmark window. Enter Web Mail as the Bookmark Title. Enter the server destination IP address 192.168.10.3 as the URL. Click OK in the Add Bookmark window to return to the Configure GUI Customization Objects window. Select the desired bookmark and click OK to return to the Bookmark List window.Click Next to continue. The Summary page (Step 6 of 6) is displayed next. Verify that the information configured in theSSL VPN wizard is correct. Click Finish to complete the process and deliver the commands to the ASA. To verify the connection profile ; Configuration > Remote Access VPN > Clientless SSL VPN Access > Connection Profiles.From this window the VPN configuration can be verified and edited. Step 5: Verify VPN access from the remote host. Open the browser on PC-C and enter the login URL for the SSL VPN into the address field(https://209.165.200.234). The Logon window should appear. Enter the previously configured user name VPNuser and password remote and click Logon to continue. The Web Portal window should display.
On PC-C open up browser >> in the address bar, type in: https://209.165.200.234 Enter the following credentials;Username: VPNuser Password: remote Click Logon to continue. Now the web portal should display! Activity (1) Filters Add to collectionReviewAdd noteLikeEmbed Showing AllMost RecentReviewsAll NotesLikes You've already reviewed this. Edit your review <#>. Rating 0/5 Post notePost reviewPost replyPost note and like 1 hundred reads|about 1 month ago Load more Recommended * PURCHASE ONLY SAMPLE NOT AVAILABLE CCNAS v1.1 SBA cisco84 <http://www.scribd.com/doc/135886206/CCNAS-v1-1-SBA> * PURCHASE ONLY SAMPLE NOT AVAILABLE Ccnasecurity Sba Final Billy Zomg <http://www.scribd.com/doc/88889521/Ccnasecurity-Sba-Final> * PURCHASE ONLY SAMPLE NOT AVAILABLE ccna security skills based assessment http://utsit.blogspot.com.au/ <http://www.scribd.com/doc/95302525/ccna-security-skills-based-assessment> * PURCHASE ONLY SAMPLE NOT AVAILABLE
CCNA Security Skills Based Assessment-1 Hiran Vithanage <http://www.scribd.com/doc/112839461/CCNA-Security-Skills-Based-Assessment-1 > * PURCHASE ONLY SAMPLE NOT AVAILABLE Instructors-CCNASec-V1.1 cisco84 <http://www.scribd.com/doc/121389592/Instructors-CCNASec-V1-1> * PURCHASE ONLY SAMPLE NOT AVAILABLE CCNA Security PT Practice SBA-1 Zhenya Hristova <http://www.scribd.com/doc/59280706/CCNA-Security-PT-Practice-SBA-1> * PURCHASE ONLY SAMPLE NOT AVAILABLE CCNA Security - Final Exam Answers abdallah18 <http://www.scribd.com/doc/61397645/CCNA-Security-Final-Exam-Answers> * PURCHASE ONLY SAMPLE NOT AVAILABLE Ccna Security Sba Riyad Id <http://www.scribd.com/doc/83302778/Ccna-Security-Sba> * More From This User <http://www.scribd.com/adelaide_citya/documents> * PURCHASE ONLY SAMPLE NOT AVAILABLE 6EWS Theory Test V2 Adelaide-City South Australia <http://www.scribd.com/doc/173255086/6EWS-Theory-Test-V2> * PURCHASE ONLY SAMPLE NOT AVAILABLE Aruba ACMA Practice Theory 6EWD Pt2 Adelaide-City South Australia <http://www.scribd.com/doc/171344156/Aruba-ACMA-Practice-Theory-6EWD-Pt2> * PURCHASE ONLY SAMPLE NOT AVAILABLE Aruba ACMA Practice Theory 6EWD Pt1 Adelaide-City South Australia <http://www.scribd.com/doc/171339928/Aruba-ACMA-Practice-Theory-6EWD-Pt1>
* PURCHASE ONLY SAMPLE NOT AVAILABLE Aruba.practiceTest.acma 6 1.v2013!07!23.by.drummerkyle Adelaide-City South Australia <http://www.scribd.com/doc/168132255/Aruba-practiceTest-acma-6-1-v2013-07-23 -by-drummerkyle> * PURCHASE ONLY SAMPLE NOT AVAILABLE 6EWS Theory Test Adelaide-City South Australia <http://www.scribd.com/doc/166219742/6EWS-Theory-Test> * PURCHASE ONLY SAMPLE NOT AVAILABLE 2010_3_1971cdc5 Adelaide-City South Australia <http://www.scribd.com/doc/164573654/2010-3-1971cdc5> * PURCHASE ONLY SAMPLE NOT AVAILABLE Chapter4-ExploitWin7 Adelaide-City South Australia <http://www.scribd.com/doc/147561032/Chapter4-ExploitWin7> * PURCHASE ONLY SAMPLE NOT AVAILABLE 5LXN SSH Exercise Adelaide-City South Australia <http://www.scribd.com/doc/145226502/5LXN-SSH-Exercise> * PURCHASE ONLY SAMPLE NOT AVAILABLE 5LXN Samba Exercise Adelaide-City South Australia <http://www.scribd.com/doc/145222934/5LXN-Samba-Exercise> * PURCHASE ONLY SAMPLE NOT AVAILABLE Iptables Exercise Adelaide-City South Australia <http://www.scribd.com/doc/145222587/Iptables-Exercise> * PURCHASE ONLY SAMPLE NOT AVAILABLE Iptables Exercise Adelaide-City South Australia <http://www.scribd.com/doc/143696966/Iptables-Exercise> * PURCHASE ONLY
SAMPLE NOT AVAILABLE Open Gpg Adelaide-City South Australia <http://www.scribd.com/doc/143696375/Open-Gpg> * PURCHASE ONLY SAMPLE NOT AVAILABLE 4LNX2 Samba Exercise Adelaide-City South Australia <http://www.scribd.com/doc/143680646/4LNX2-Samba-Exercise> * PURCHASE ONLY SAMPLE NOT AVAILABLE 4lnx2 Nfs Vsftp Exercise Adelaide-City South Australia <http://www.scribd.com/doc/143558084/4lnx2-Nfs-Vsftp-Exercise> * PURCHASE ONLY SAMPLE NOT AVAILABLE 5ECS - Administering Office 365 Adelaide-City South Australia <http://www.scribd.com/doc/143554046/5ECS-Administering-Office-365> * PURCHASE ONLY SAMPLE NOT AVAILABLE Deploying Office 365 Adelaide-City South Australia <http://www.scribd.com/doc/143547680/Deploying-Office-365> * PURCHASE ONLY SAMPLE NOT AVAILABLE MCTS 70-664: MS Lync 2010 Configuring Adelaide-City South Australia <http://www.scribd.com/doc/143544463/MCTS-70-664-MS-Lync-2010-Configuring> * PURCHASE ONLY SAMPLE NOT AVAILABLE Theory Test 1 - Microsoft Exchange 2010 Adelaide-City South Australia <http://www.scribd.com/doc/143337822/Theory-Test-1-Microsoft-Exchange-2010> * PURCHASE ONLY SAMPLE NOT AVAILABLE 5ECS SharePoint 2010 Configuring Adelaide-City South Australia <http://www.scribd.com/doc/143336427/5ECS-SharePoint-2010-Configuring> * PURCHASE ONLY SAMPLE NOT AVAILABLE
SharePoint 2010 Configuring eLearning Self Test Adelaide-City South Australia <http://www.scribd.com/doc/142034735/SharePoint-2010-Configuring-eLearning-S elf-Test> * PURCHASE ONLY SAMPLE NOT AVAILABLE Dis4 Lab 5.5.3.3 Student Adelaide-City South Australia <http://www.scribd.com/doc/140951005/Dis4-Lab-5-5-3-3-Student> * PURCHASE ONLY SAMPLE NOT AVAILABLE Stadium Story Adelaide-City South Australia <http://www.scribd.com/doc/140950975/Stadium-Story> * PURCHASE ONLY SAMPLE NOT AVAILABLE Film Story Adelaide-City South Australia <http://www.scribd.com/doc/140950900/film-story> * PURCHASE ONLY SAMPLE NOT AVAILABLE Dis4 Lab 1.3.4.4 Answer Adelaide-City South Australia <http://www.scribd.com/doc/138454759/Dis4-Lab-1-3-4-4-Answer> * Download and print this document * Read and print without ads * Download to keep your version * Edit, email or read offline Choose a format: .PDF.TXT Download Recommended <http://www.scribd.com/doc/135886206/CCNAS-v1-1-SBA> CCNAS v1.1 SBA <http://www.scribd.com/doc/135886206/CCNAS-v1-1-SBA> cisco84 <http://www.scribd.com/cisco84> CCNAS v1.1 SBA <http://www.scribd.com/doc/88889521/Ccnasecurity-Sba-Final> Ccnasecurity Sba Final
<http://www.scribd.com/doc/88889521/Ccnasecurity-Sba-Final> Billy Zomg <http://www.scribd.com/bzomg> <http://www.scribd.com/doc/95302525/ccna-security-skills-based-assessment> ccna security skills based assessment <http://www.scribd.com/doc/95302525/ccna-security-skills-based-assessment> http://utsit.blogspot.com.au/ <http://www.scribd.com/UTSuni> ccna security skills based assessment <http://www.scribd.com/doc/112839461/CCNA-Security-Skills-Based-Assessment-1> CCNA Security Skills Based Assessment-1 <http://www.scribd.com/doc/112839461/CCNA-Security-Skills-Based-Assessment-1> Hiran Vithanage <http://www.scribd.com/hiranv> <http://www.scribd.com/doc/121389592/Instructors-CCNASec-V1-1> Instructors-CCNASec-V1.1 <http://www.scribd.com/doc/121389592/Instructors-CCNASec-V1-1> cisco84 <http://www.scribd.com/cisco84> lolz <http://www.scribd.com/doc/59280706/CCNA-Security-PT-Practice-SBA-1> CCNA Security PT Practice SBA-1 <http://www.scribd.com/doc/59280706/CCNA-Security-PT-Practice-SBA-1> Zhenya Hristova <http://www.scribd.com/zhenya_hristova> <http://www.scribd.com/doc/61397645/CCNA-Security-Final-Exam-Answers> CCNA Security - Final Exam Answers <http://www.scribd.com/doc/61397645/CCNA-Security-Final-Exam-Answers> abdallah18 <http://www.scribd.com/abdallah18> <http://www.scribd.com/doc/83302778/Ccna-Security-Sba> Ccna Security Sba <http://www.scribd.com/doc/83302778/Ccna-Security-Sba> Riyad Id <http://www.scribd.com/abu_yousef_1> answers Previous <#>|Next <#>Page 1 of 2 Download and print this document * Read and print without ads * Download to keep your version * Edit, email or read offline Choose a format: .PDF.TXT Download You're Reading a Free Preview Download scribd. scribd. scribd. scribd. scribd. scribd. scribd. scribd. scribd. scribd. scribd. scribd. scribd. scribd.
<http://twitter.com/scribd><http://www.facebook.com/pages/Scribd/6978454082></sc ribd> *About* * * * * * About Scribd <http://www.scribd.com/about> Team <http://www.scribd.com/about/team> Blog <http://blog.scribd.com/> Join our team! </jobs> Contact Us <http://www.scribd.com/contact>
*Subscriptions* * Subscribe today <http://www.scribd.com/subscribe> * Your subscription <http://www.scribd.com/account-settings/order-history> * Gift cards <http://www.scribd.com/giftcards> *Advertise with us* * Get started </advertise> * AdChoices </adchoices> *Support* * * * * > *Partners* * Publishers </publishers> * Developers / API </developers> *Legal* * Terms </terms> * Privacy </privacy> * Copyright </copyright> *Get Scribd Mobile* Scribd on Appstore <https://itunes.apple.com/us/app/scribd-worlds-largest-online/id542557212?mt =8#> Scribd on Google Play <https://play.google.com/store/apps/details?id=com.scribd.app.reader0&hl=en> * Mobile Site <http://www.scribd.com/mobile?remobile=1> Copyright 2013 Scribd Inc. Language: English <#> Choose the language in which you want to experience Scribd: * English </language?destination=http%3A%2F%2Fwww.scribd.com%2Fdoc%2F175689839&id=en&a nchor=> Help <http://support.scribd.com/login> FAQ </faq> Press </press> Purchase Help <http://support.scribd.com/forums/189164-Purchases-subscriptions-and-refunds
* </language?destination=http%3A%2F%2Fzh.scribd.com%2Fdoc%2F175689839&id=zh&an chor=> * Espaol </language?destination=http%3A%2F%2Fes.scribd.com%2Fdoc%2F175689839&id=es&an chor=> * </language?destination=http%3A%2F%2Far.scribd.com%2Fdoc%2F175689839&id=ar&an chor=> * Portugus </language?destination=http%3A%2F%2Fpt.scribd.com%2Fdoc%2F175689839&id=pt-br &anchor=> * </language?destination=http%3A%2F%2Fja.scribd.com%2Fdoc%2F175689839&id=ja&an chor=> * Deutsch </language?destination=http%3A%2F%2Fde.scribd.com%2Fdoc%2F175689839&id=de&an chor=> * Franais </language?destination=http%3A%2F%2Ffr.scribd.com%2Fdoc%2F175689839&id=fr&an chor=> * Turkce </language?destination=http%3A%2F%2Ftr.scribd.com%2Fdoc%2F175689839&id=tr&an chor=> * </language?destination=http%3A%2F%2Fru.scribd.com%2Fdoc%2F175689839&id=ru&an chor=> * Ting vit </language?destination=http%3A%2F%2Fvi.scribd.com%2Fdoc%2F175689839&id=vi&an chor=> * Jzyk polski </language?destination=http%3A%2F%2Fpl.scribd.com%2Fdoc%2F175689839&id=pl&an chor=> * Bahasa indonesia </language?destination=http%3A%2F%2Fid.scribd.com%2Fdoc%2F175689839&id=id&an chor=> Login with Facebook Sorry, we are unable to log you in via Facebook at this time. Please try again later. Already have a Scribd account? <#toggle> Email address or username Password Trouble logging in? </password/forgot> New to Scribd? Sign up for a free account. <#toggle> Create username (required) Password (required) Email address (required) Send me the Scribd Newsletter, and occasional account related communications. Privacy policy <http://www.scribd.com/privacy> You will receive email notifications regarding your account activity. You can manage these notifications in your account settings. We promise to respect your privacy. JOIN80 MILLION MONTHLY READERS
FROM100+ COUNTRIES READING40 MILLION BOOKS & DOCUMENTS Login Successful Sign Up Successful Now bringing you back... Reset Password Please enter your email address below to reset your password. We will send you an email with instructions on how to continue. Email address You need to provide a login for this account as well. login Submit Back to login Password Reset Email Sent Does that email address look wrong? Try again with a different email.
You might also like
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3From EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3No ratings yet
- CCNAS v1.1 Skills-Based Assessment Hands On AnswersDocument18 pagesCCNAS v1.1 Skills-Based Assessment Hands On AnswersAdelaide-City South Australia86% (14)
- CCNAS v1.1 SBADocument10 pagesCCNAS v1.1 SBACaleb Peters0% (1)
- Ccnasv1.1 Chp10 Lab D Asa Isr s2s VPN StudentDocument36 pagesCcnasv1.1 Chp10 Lab D Asa Isr s2s VPN Studentmuscle260% (1)
- 5.4.1.2 Packet Tracer - Skills Integration Challenge Instructions-OkDocument9 pages5.4.1.2 Packet Tracer - Skills Integration Challenge Instructions-OkSergio Castañeda50% (2)
- 10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5506-X ASDMDocument16 pages10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5506-X ASDMelizaNo ratings yet
- Lab Sous Gns3-Configuring A Site-To-Site Ipsec VPN Using CCP and AsdmDocument31 pagesLab Sous Gns3-Configuring A Site-To-Site Ipsec VPN Using CCP and Asdmaboubakeriam djibirldararNo ratings yet
- 10.2.1.9 Lab - Configure A Site-To-Site IPsec VPN Using ISR CLI and ASA 5505 ASDMDocument22 pages10.2.1.9 Lab - Configure A Site-To-Site IPsec VPN Using ISR CLI and ASA 5505 ASDMerojasNo ratings yet
- 10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5505 ASDMDocument22 pages10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5505 ASDMelizaNo ratings yet
- Cisco ASA 5505 - Getting Started GuideDocument166 pagesCisco ASA 5505 - Getting Started GuidefdipernaNo ratings yet
- Ccnasv1.1 Chp10 Lab-C Asa-ssl-VPN Instructor 8.25.37 Am 8.25.57 AmDocument50 pagesCcnasv1.1 Chp10 Lab-C Asa-ssl-VPN Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (3)
- 10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5505 ASDM - InstructorDocument36 pages10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5505 ASDM - Instructorcheicktest1No ratings yet
- Konfigurasi ServerDocument6 pagesKonfigurasi ServerDhandi Dwi FaryanNo ratings yet
- 10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5506-X ASDM - InstructorDocument29 pages10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5506-X ASDM - Instructorcheicktest1No ratings yet
- Asa 91 Firewall ConfigDocument712 pagesAsa 91 Firewall Configdimkatsar30No ratings yet
- Lab - Configuring A Site-to-Site VPN Using Cisco IOS and CCPDocument30 pagesLab - Configuring A Site-to-Site VPN Using Cisco IOS and CCPVasan Suryaßoyzz100% (1)
- Cisco Configuring A Cisco 827 Router Terminating On A Cisco 6400 in RBE Mode Using RFC1483 BridgingDocument6 pagesCisco Configuring A Cisco 827 Router Terminating On A Cisco 6400 in RBE Mode Using RFC1483 BridgingSamah ElshariefNo ratings yet
- 10.1.4.8 Lab - Configure ASA 5506-X Basic Settings and Firewall Using ASDMDocument16 pages10.1.4.8 Lab - Configure ASA 5506-X Basic Settings and Firewall Using ASDMelizaNo ratings yet
- Configuring Zone Based Policy FirewallsDocument13 pagesConfiguring Zone Based Policy FirewallsNorman Pal-og Madongit17% (6)
- 10.3.1.1 Lab - Configure Clientless Remote Access SSL VPNs Using ASA 5505 ASDMDocument21 pages10.3.1.1 Lab - Configure Clientless Remote Access SSL VPNs Using ASA 5505 ASDMelizaNo ratings yet
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSDocument21 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSOsman SepulvedaNo ratings yet
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS PDFDocument20 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS PDFLizSocaZevallos100% (1)
- 4.4.1.2 Lab - Configuring Zone-Based Policy FirewallsDocument13 pages4.4.1.2 Lab - Configuring Zone-Based Policy Firewallscesar javierNo ratings yet
- Configuring An Ipsec Tunnel Through A Firewall With Nat: Document Id: 14138Document8 pagesConfiguring An Ipsec Tunnel Through A Firewall With Nat: Document Id: 14138pandvas5No ratings yet
- Digi Connect® Wan Application Guide:: Sample Cisco Asa To Digi Connect / Connectport VPN Config PG 1Document6 pagesDigi Connect® Wan Application Guide:: Sample Cisco Asa To Digi Connect / Connectport VPN Config PG 1Miquel Pelegrí QuevedoNo ratings yet
- Ccnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 AmDocument35 pagesCcnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (2)
- Troubleshooting BGP PDFDocument108 pagesTroubleshooting BGP PDFSatyapriya PanigrahiNo ratings yet
- 9.3.1.2 Lab - Configure ASA 5506-X Basic Settings and Firewall Using CLIDocument24 pages9.3.1.2 Lab - Configure ASA 5506-X Basic Settings and Firewall Using CLIeliza0% (1)
- 1.-Asegurarnos de Tener Una Configuración de Red Estática:: Cat /etc/sysconfig/network-Scripts/ifcfg-Enp0s3Document18 pages1.-Asegurarnos de Tener Una Configuración de Red Estática:: Cat /etc/sysconfig/network-Scripts/ifcfg-Enp0s3Andres BustosNo ratings yet
- 9.3.1.2 Lab - Configure ASA 5505 Basic Settings and Firewall Using CLIDocument26 pages9.3.1.2 Lab - Configure ASA 5505 Basic Settings and Firewall Using CLIJUan ALexis MEna0% (1)
- Laboratorium 1Document35 pagesLaboratorium 1SBX 4LifeNo ratings yet
- Practical Walk ThroughDocument9 pagesPractical Walk ThroughtjduffieNo ratings yet
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSDocument21 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSPauloNo ratings yet
- 9.3.2.13 Lab - Configuring and Verifying Extended ACLsDocument8 pages9.3.2.13 Lab - Configuring and Verifying Extended ACLsAnonymous cW6o4f886% (14)
- CCNA Security CommandsDocument61 pagesCCNA Security CommandsMohammed Mostafa100% (5)
- 11.4.1.2 Packet Tracer - Skills Integration Challenge InstructionsDocument4 pages11.4.1.2 Packet Tracer - Skills Integration Challenge InstructionsJose Luis Gil50% (2)
- CCNA Security Skills Based Challenge LabDocument9 pagesCCNA Security Skills Based Challenge LabSiaw YsNo ratings yet
- Security Hardening Checklist Guide For Cisco RoutersDocument7 pagesSecurity Hardening Checklist Guide For Cisco RoutersFaouzi MaddouriNo ratings yet
- Praktik Ke-6 Lab - Konfigurasi Pengaturan Dasar ASA Dan Firewall Menggunakan CLI - MahasiswaDocument37 pagesPraktik Ke-6 Lab - Konfigurasi Pengaturan Dasar ASA Dan Firewall Menggunakan CLI - MahasiswaIhsan EooiNo ratings yet
- 5.4.1.1 Lab - Configure An Intrusion Prevention System (IPS) PDFDocument21 pages5.4.1.1 Lab - Configure An Intrusion Prevention System (IPS) PDFIvan ZuritaNo ratings yet
- Icnd1 CramDocument64 pagesIcnd1 CramJuan SmithNo ratings yet
- Tyit Sic Manual 2023-24Document56 pagesTyit Sic Manual 2023-24newvinayakprintsNo ratings yet
- CCENT Cheat SheetDocument18 pagesCCENT Cheat SheetJim D'FotoNo ratings yet
- Ccnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 AmDocument52 pagesCcnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 Amclearmoon247No ratings yet
- Isa 2000Document72 pagesIsa 2000rrs756No ratings yet
- 4.4.1.2 Lab - Configuring Zone-Based Policy FirewallsDocument15 pages4.4.1.2 Lab - Configuring Zone-Based Policy FirewallselizaNo ratings yet
- Configuring Layer 3 Interfaces On Catalyst 6500Document8 pagesConfiguring Layer 3 Interfaces On Catalyst 6500Syed Ali Raza GardeziNo ratings yet
- 10.3.1.2 Lab - Configure AnyConnect Remote Access SSL VPN Using ASA 5505 ASDM - InstructorDocument37 pages10.3.1.2 Lab - Configure AnyConnect Remote Access SSL VPN Using ASA 5505 ASDM - Instructorcheicktest1No ratings yet
- Chapter 9 Lab A: Configuring ASA Basic Settings and Firewall Using CLIDocument13 pagesChapter 9 Lab A: Configuring ASA Basic Settings and Firewall Using CLIHAMDI GDHAMINo ratings yet
- 10.1.4.8 Lab - Configure ASA 5505 Basic Settings and Firewall Using ASDMDocument40 pages10.1.4.8 Lab - Configure ASA 5505 Basic Settings and Firewall Using ASDMerojasNo ratings yet
- 9.3.1.2 Lab - Configure ASA Basic Settings and Firewall Using CLI PDFDocument26 pages9.3.1.2 Lab - Configure ASA Basic Settings and Firewall Using CLI PDFPAPA AROUNA FOFANA50% (2)
- Cisco IOS Security TemplateDocument10 pagesCisco IOS Security TemplateshankerunrNo ratings yet
- ASA5506 9-3-1-2 Lab - Configure ASA Basic Settings and Firewall Using CLI - 1-26Document31 pagesASA5506 9-3-1-2 Lab - Configure ASA Basic Settings and Firewall Using CLI - 1-26Hoàng Dũng0% (1)
- 10.3.1.2 Lab - Configure AnyConnect Remote Access SSL VPN Using ASA 5506-X ASDM - InstructorDocument22 pages10.3.1.2 Lab - Configure AnyConnect Remote Access SSL VPN Using ASA 5506-X ASDM - Instructorcheicktest1No ratings yet
- Accessing The WAN Student Skills Based Assessment Lab Answer KeyDocument9 pagesAccessing The WAN Student Skills Based Assessment Lab Answer KeyRadmilo Milojković75% (4)
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- LABDCT 2002 (Guide) Nexus.5020.Lab - GuideDocument52 pagesLABDCT 2002 (Guide) Nexus.5020.Lab - Guidekds20850No ratings yet
- Cloud Computing IEEE PaperDocument4 pagesCloud Computing IEEE PaperAsrar Ul HaqNo ratings yet
- 2.4.3.4 Packet TracerDocument11 pages2.4.3.4 Packet TracercoleparksNo ratings yet
- BSC It AssignmentsDocument3 pagesBSC It Assignmentsapi-26125777100% (2)
- Compass Software: Features and HighlightsDocument2 pagesCompass Software: Features and HighlightsHector Ernesto Cordero AmaroNo ratings yet
- 0a-Esp8285 Datasheet enDocument31 pages0a-Esp8285 Datasheet enprofe321No ratings yet
- The Rise and Fall of NTP DDOS AttacksDocument14 pagesThe Rise and Fall of NTP DDOS AttackskxscribdNo ratings yet
- RGX4400 User ManualDocument78 pagesRGX4400 User ManualUma BakiNo ratings yet
- Adding A Second Controller To Create An HA PairDocument24 pagesAdding A Second Controller To Create An HA PairPurushothama GnNo ratings yet
- Ay 3 8910Document8 pagesAy 3 8910Przemysław WójcikNo ratings yet
- Output LogDocument480 pagesOutput LogBocsa CristianNo ratings yet
- RobotStudio 2023-1 Release NotesDocument34 pagesRobotStudio 2023-1 Release Notesduy.nguyen.2501No ratings yet
- Ccna Training Ccnav3 - New Questions 4Document31 pagesCcna Training Ccnav3 - New Questions 4Remi PaternackNo ratings yet
- Studio 5000 Logix Designer - 35.00.01 (Released 2 - 2023)Document17 pagesStudio 5000 Logix Designer - 35.00.01 (Released 2 - 2023)Everton PodencianoNo ratings yet
- COMP600 Spring Lab#5Document5 pagesCOMP600 Spring Lab#5jassica sahiNo ratings yet
- E-Commerce CH 3 (Part 1)Document44 pagesE-Commerce CH 3 (Part 1)Irfan ur RehmanNo ratings yet
- Cloud Native Fundamentals: Prasenjit Sarkar Oracle Cloud Infrastructure February 2020Document33 pagesCloud Native Fundamentals: Prasenjit Sarkar Oracle Cloud Infrastructure February 2020Harish NaikNo ratings yet
- Es ZG626 Course HandoutDocument4 pagesEs ZG626 Course Handout2023ht01598No ratings yet
- Fiber Optic Communication and Networks (ECE4005)Document64 pagesFiber Optic Communication and Networks (ECE4005)sai KarthikNo ratings yet
- Essential RUN commands for WindowsDocument2 pagesEssential RUN commands for WindowsRobiatul Adawiah RipinNo ratings yet
- User Manual - TDSL300W2Document60 pagesUser Manual - TDSL300W2dugdugdugdugi67% (3)
- Exor Logs.3Document22 pagesExor Logs.3Todd PetersonNo ratings yet
- UNIT I Embedded SystemsDocument60 pagesUNIT I Embedded SystemspremsonyNo ratings yet
- 8051 Microcontroller Logical OperationsDocument19 pages8051 Microcontroller Logical OperationsAjins Aju0% (1)
- 4.6.2 Universal Serial Bus (USB)Document18 pages4.6.2 Universal Serial Bus (USB)kollavivek_534195858100% (2)
- External Antenna Passthrough Configuration Tool For CF-20Document9 pagesExternal Antenna Passthrough Configuration Tool For CF-20Mike BurtonNo ratings yet
- Copia de ABB NPCU-01Document4 pagesCopia de ABB NPCU-01Abraham GalvánNo ratings yet
- Activity 3.5.4: Subnetting ScenarioDocument3 pagesActivity 3.5.4: Subnetting ScenarioAli HusainNo ratings yet
- Pathloss Files Conversion Methods 0 PDFDocument5 pagesPathloss Files Conversion Methods 0 PDFKyle DiopNo ratings yet
- Test Project WSC2019 ITNSA Module ADocument11 pagesTest Project WSC2019 ITNSA Module Asys admin0% (1)