Professional Documents
Culture Documents
Is 906 StudentManual
Uploaded by
PauloOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Is 906 StudentManual
Uploaded by
PauloCopyright:
Available Formats
IS-906: WORKPLACE SECURITY AWARENESS
This course has been developed by the National Protection and Programs Directorate/Office of Infrastructure Protection, U.S. Department of Homeland Security, and is being hosted by the Emergency Management Institute (EMI). For more information or to address questions or comments about this course, please contact IP_Education@HQ.dhs.gov.
IS-906: Workplace Security Awareness
COURSE INTRODUCTION Visual 1
Key Points Welcome to the Workplace Security Awareness course. This course provides guidance to individuals and organizations on how to improve security in the workplace.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 1
IS-906: Workplace Security Awareness
COURSE INTRODUCTION Visual 2
Key Points Review the administrative matters listed on the visual.
Page 2
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
COURSE INTRODUCTION Visual 3
Key Points By the end of this course, you should be able to: Identify potential risks to workplace security. Describe measures for improving workplace security. Determine the actions to take in response to a security situation.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 3
IS-906: Workplace Security Awareness
THE IMPORTANCE OF WORKPLACE SECURITY Visual 4
Key Points Why is workplace security awareness important for all employees?
Page 4
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
THE IMPORTANCE OF WORKPLACE SECURITY Visual 5
Key Points Workplace security is important to address risk, which is the potential for an unwanted outcome from an incident, event, or occurrence. The three components of risk to consider are: Threat: A natural or manmade occurrence, individual, entity, or action that has or indicates the potential to harm life, information, operations, the environment, and/or property. Vulnerability: Physical features or operational attributes that render an entity open to exploitation or susceptible to a given hazard. Vulnerabilities may be associated with physical factors (e.g., a broken fence), cyber factors (e.g., lack of a firewall), or human factors (e.g., untrained guards). Consequence (Impact): The effect of an event, incident, or occurrence. For the purposes of the National Infrastructure Protection Plan, consequences are divided into four main categories: public health and safety, economic, psychological, and governance impacts.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 5
IS-906: Workplace Security Awareness
THE IMPORTANCE OF WORKPLACE SECURITY Visual 6
Key Points We live in a world of ever-increasing risk. No workplace whether a construction site, office building, factory floor, or retail store is immune. Risks threaten worker safety, employee morale, and a companys economic livelihood. Employees are often the target of these threats, as well as the organization's first line of defense against them. Security is a shared responsibility and employees are an integral part of an organizations security solution.
Page 6
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
THE IMPORTANCE OF WORKPLACE SECURITY Visual 7
Key Points Organizations today employ a number of security measures to reduce risk, such as concrete barriers, obstructions, and gates. But no matter what type of security measures an organization puts in place, it is important for ALL employees to be vigilant about anything unusual at the workplace that could threaten security. In this course you will learn that when observing a situation that may threaten security, you should: Determine the kinds of behaviors and activities that should be reported. Report these activities and behaviors to the appropriate supervisor or security personnel. Never confront the situation alone.
Please note that the actions described throughout this training are options to consider. Whenever possible and applicable, employees should comply with established company policies and procedures.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 7
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 8
Key Points This course presents the following common threats and describes measures employees can take in each area to promote a secure workplace: Access and Security Control Threats Criminal and Terrorist Threats Workplace Violence Threats Information and Cyber Threats
This section of the course will focus on access and security control threats.
Page 8
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 9
Key Points The first threat to the workplace covered in this course is unauthorized access to sensitive areas or information by persons, equipment, or materials. It is important to secure access points by: Limiting the number of access points. Using appropriate locks (e.g., padlock, keyed cylinder, or electronic entry control system). Controlling doors and other entrances. Restricting access to key areas; roofs; and heating, ventilation, and air conditioning (HVAC) systems. Using access identification systems such as employee badges, card readers, keypads, and biometric identification. Posting signs at access points and restricted access areas.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 9
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 10
Key Points Typical access control procedures include: Identification checks or searches (e.g., employee badge checks, biometrics). Procedures to limit who has keys and identification cards and how they can be obtained. Search or verification procedures for delivery of materials, equipment, or supplies. Current database of employee-owned vehicles, and protocols for investigating illegally parked cars. Limited access by contractors, vendors, and temporary employees. Training for mailroom and receiving personnel in recognizing suspicious items.
Page 10
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 11
Key Points Many facilities have systems for access control and visitor management deployed throughout the property. These systems often grant access to individuals based on their function at the workplace. Facilities may use ID badges or picture IDs for quick identification of personnel while providing the appropriate level of access control. Many badge types work with proximity readers, allowing employees to use the badge as a key.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 11
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 12
Key Points If the workplace uses ID badges or other ID security measures, employees should keep the following procedures in mind: Wear the badge on the outermost garment at all times while in the workplace. Never allow piggybackingletting an individual follow through opened access doors. Never lend or borrow badges when another employee has forgotten his or her badge. Never allow visitors to share another persons badge. Only one person should be cleared through an entry point on a given badge. Report a lost badge to the appropriate security personnel, manager, or human resources representative immediately.
Sources: Chemical Security Awareness Training/Protect Your Workplace Campaign: Report Suspicious Behavior and Activity Poster
Page 12
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 13
Key Points Scenario: Image 1. Image 2. Image 3. Kathy, an employee, is entering through a secure access door with a card reader. She scans her ID to unlock the door. A man with his hands full of boxes approaches the door as Kathy opens it. Kathy does not know the man. He asks her to hold the door open for him. Kathy allows the man with the boxes to enter the building through the door she has opened. She feels uncomfortable allowing the door to close when his hands clearly are full.
What should Kathy have done differently?
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 13
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 14
Key Points Nonemployees should wear a visitor's badge and should be escorted at all times. For more information on specific workplace security policies, participants should refer to the organization's security officer or management representative. If the workplace does not use an ID badge system, employees may follow other appropriate recognition methods (for example, vest, hat, or uniform) and apply the recognition procedures and reporting requirements taught in this course.
Page 14
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 15
Key Points Scenario: You decide to take a quick break from your work and go talk to a coworker next door. After a few minutes, you need to use the restroom. You realize you do not have your badge. When you return to your desk to retrieve it, its not there. Thats strangeyou thought you left it on your desk. What should you do?
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 15
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 16
Key Points Employees should challenge unknown or suspiciously behaving people encountered within employee-only or secure areas if they: Are not wearing appropriate identification. Are not accompanied by an appropriate escort. Have an appearance that is inconsistent with the workplace dress code (for example, overly casual clothing). Appear to be lost or are asking for directions to specific areas.
Note: These standard access security control procedures are based on industry best practices. However, they may not reflect the policies of participant workplaces. You should contact a manager or security to learn the specific workplace policy for approaching such individuals.
Page 16
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 17
Key Points Scenario: Anne has a lot on her mind. When she sees a man she does not recognize trying to open a door down the hall, she hesitates for a split second, but then smiles when he turns to face her. After all, we all like to be friendly to a new face. The man smiles back as they pass each other. What should Anne do differently?
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 17
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 18
Key Points If encountering someone without proper identification (as per workplace requirements), employees should: Follow any established policies and procedures regarding surveillance of suspicious or unknown persons. Approach the person if comfortable doing so. Employees who feel threatened by the situation should not approach the person, and never put themselves in harm's way. Notify security or the appropriate manager and provide a description, location, and direction the person is traveling.
Page 18
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 19
Key Points Activity Purpose: To reinforce your understanding of the best way to approach an unknown individual. Instructions: Working as a team: 1. Create a list of five techniques to use when approaching an unknown individual. 2. Record the list on chart paper. 3. Select a spokesperson and be prepared to present your teams list in 5 minutes.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 19
IS-906: Workplace Security Awareness
ACCESS AND SECURITY CONTROL THREATS Visual 20
Key Points If you see an individual without a required badge or an escort you need to take the time to report the situation rather than proceeding or ignoring it. When observing a situation that may threaten security, always report it to security or the appropriate supervisor.
Page 20
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 21
Key Points The next section will focus on criminal and terrorist threats.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 21
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 22
Key Points All organizationsfrom hotels, banks, and grocery stores to manufacturing plants and nonprofit organizationscan be venues for criminal or terrorist activities. Employees should be alert to any persons who behave suspiciously or engage in unusual actions; these behaviors may be indications of criminal or terrorist activity. Employees should: Have an understanding of how criminals or terrorists could use the workplace facility for their own purposes. Promptly alert security personnel, management, and appropriate authorities when observing suspicious behavior or unusual items or activity. Report something if it looks or feels wrong. Security is everyone's responsibility.
Page 22
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 23
Key Points What are some examples of suspicious behaviors?
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 23
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 24
Key Points Scenario: Early one morning, Jill is arriving at work. As she approaches the elevator, she sees a woman in front of her looking up at the security camera. Jill thinks she sees the woman take a picture with a camera phone. What should Jill do?
Page 24
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 25
Key Points In addition to suspicious behavior, employees should be alert for unusual or suspicious items, such as: Changed or unusual situations around the workplace such as tampered heating, ventilation, and air-conditioning (HVAC) units, abandoned vehicles, damaged fencing, or missing property. Suspicious packages or items, especially: o Large amounts of unusual substances (e.g., acetone, peroxide, or drain cleaner). o Fumes, odors, or liquids coming from a package. o Disassembled electrical components such as wires, circuit boards, or batteries. o Plans, drawings, schematics, or maps.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 25
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 26
Key Points Employees should immediately notify a supervisor or security person of the following: A breach in the security perimeter, such as a door that is propped open A suspicious package or item
Employees should never approach or attempt to open or inspect suspicious packages.
Page 26
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 27
Key Points Scenario: Kim and Joyce are having a conversation as they walk from the parking lot toward their office. While they are talking, Joyce notices that a hole has been cut in the fence around their building. What should Kim and Joyce do?
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 27
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 28
Key Points Organizations today employ a number of security measures (e.g., concrete barriers, obstructions, and gates) to control vehicle and pedestrian access to their facilities. However, security and access control measures can be compromised. For example, security passes can be removed from employee or other authorized vehicles and used to gain unauthorized access to secure areas. All employees should be alert for: Unattended or suspicious vehicles: Abandoned vehicles may be used to hide suspicious or stolen items, or worse, they could contain explosives for use in a terrorist act. Changes in vehicle patterns: Commonly seen vehicles such as mail trucks, delivery trucks, buses, or taxis may be suspicious if seen at unusual times or circumstancesfor example, a second mail delivery, an idle delivery truck, a bus on a different route, or a taxi circling the building numerous times.
(Continued on the following page.)
Page 28
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 28 (Continued) Employees should: Report abandoned vehicles parked on the property or adjacent to the workplace. Be on the lookout for private vehicles loading or unloading unusual or suspicious items on or around the property. Be alert for familiar vehicles arriving at unusual, unscheduled, or inappropriate times. Report observations to security personnel or an appropriate supervisor immediately. Observe and, if possible, write down a suspicious vehicle's license plate number and description (make, model, color, body damage, bumper stickers, and accessories). Not take any other action except to observe and report the vehicle. As a secondary means of reporting, notify local law enforcement.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 29
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 29
Key Points Scenario: James and Sanjay are walking back from lunch when James sees a van with no license plates sitting in a no-parking zone in front of the loading dock. When James steps toward the vehicle for a better look, the person in the driver seat crouches down to avoid being seen. Sanjay tells James theyd better keep walking, as they are running late. The men go back into the building without telling anyone about the incident. What should Sanjay and James have done?
Page 30
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 30
Key Points Bomb threat calls should be taken seriously. Use the following procedures: Keep calm. Keep the caller on the line as long as possible. Record every word spoken by the caller on a form such as a bomb threat checklist (sample provided on the following page). Obtain as much information as possible about the threat without antagonizing or threatening the caller. Pay particular attention to peculiar background noises and to anything that can be gleaned from the caller's voice, such as gender, accent, and speech pattern. Report the incident immediately to a security officer, a manager, and/or a supervisor.
Employees should talk to a supervisor or security representative about the organization's bomb threat policy. Bomb threat checklists are extremely valuable and should be made available at all workstations. Review the sample bomb threat checklist. A sample bomb threat checklist is found on the following page.
Sources: Department of Homeland Security Bomb Threat Checklist and U.S. Postal Inspection Service Guide to Mail Center Security
(Continued on the following page.) IS-906: Workplace Security Awareness Student Manual
March 2012
Page 31
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 30 (Continued)
Page 32
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 31
Key Points Employees should be alert for threatening or suspicious mail or packages that might contain a bomb or hazardous substance. This includes: Letters or packages with suspicious contents such as white powder or photographs of the workplace. Letters or packages with oil or grease spots, an inaccurate address, or excessive postage and/or packaging.
If you encounter a suspicious mail item or package you should: Isolate the item. Do not open or handle it. If a letter or package contains a suspicious substance, evacuate the area and immediately wash affected body parts (such as hands) with soap and water. Contact a manager or security. Retain written threats and associated packaging/envelopes unless directed to destroy them by management or security procedures.
Sources: U.S. Postal Inspection Service Guide to Mail Center Security and DHS Best Practices for Safe Mail Handling
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 33
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 32
Key Points Employees should be aware of both potential theft and diversion. Theft is an unlawful or unauthorized acquisition by force or stealth: By an insider (member of staff), or By an outsider (someone who is not a member of the staff).
Diversion is an unlawful or unauthorized acquisition by fraud or deceit. The type of deception can vary. Diversion may include payment, but there is fraud or deceit involved, such as the improper purchase of items that are restricted. What is an example of diversion?
Page 34
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 33
Key Points An employee may detect theft by noticing a container breach. For example, a container in a warehouse that is supposed to be full may be missing some of its contents. Container discrepancies should immediately be reported to the appropriate supervisor or to security. Although there may be a reasonable explanation for a discrepancy, shortages should be reported so managers can evaluate the situation. Theft can be an indicator of a much larger problem facing security.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 35
IS-906: Workplace Security Awareness
CRIMINAL AND TERRORIST THREATS Visual 34
Key Points Scenario: Jermaine works in the warehouse of a large hardware store. Lately, he has been noticing his coworker Elaine placing jugs of paint thinner into her car. What should Jermaine do?
Page 36
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
WORKPLACE VIOLENCE THREATS Visual 35
Key Points The next section will focus on workplace violence threats.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 37
IS-906: Workplace Security Awareness
WORKPLACE VIOLENCE THREATS Visual 36
Key Points A current employee, a former employee, or an acquaintance of a current or former employee may have the potential to carry out violent behavior at the workplace. Intuitive managers and coworkers may notice indicators of potentially violent behavior in an employee. Employees who observe these indicators in a coworker should, in accordance with the organizations policy, alert a manager, security, or human resources. Potentially violent employees typically do not just snap, but may display behavioral indicators over longer periods of time. If these behaviors are recognized at the outset, they often can be managed and treated.
Source: DHS Active Shooter Booklet
Page 38
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
WORKPLACE VIOLENCE THREATS Visual 37
Key Points Activity Purpose: To help you understand the indicators of potentially violent behavior. Instructions: Working as a team: 1. Create a list of five indicators of potentially violent behavior. 2. Record your list on chart paper. 3. Select a spokesperson and be prepared to present your list in 5 minutes.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 39
IS-906: Workplace Security Awareness
WORKPLACE VIOLENCE THREATS Visual 38
Key Points Recent active shooter incidents demonstrate the importance of being prepared to respond to workplace violence. The following resources provide additional information on identifying and responding to workplace violence: Active Shooter Booklet (http://www.dhs.gov/xlibrary/assets/active_shooter_booklet.pdf): This booklet provides guidance to individuals, including managers and employees, who become involved in an active shooter situation, and discusses how to react when law enforcement responds. Active Shooter Pocket Guide (http://www.dhs.gov/xlibrary/assets/active_shooter_pocket_card.pdf): This guide provides a brief overview of how best to respond to an active shooter situation. Active Shooter Poster (http://www.dhs.gov/xlibrary/assets/active_shooter_poster.pdf): This poster describes how to respond to an active shooter, as well as how to recognize signs of potential workplace violence. The resources listed above also are available for download at FEMAs Emergency Management Institute Independent Study Web site under the course IS-907 Active Shooter: What You Can Do (http://training.fema.gov/EMIWeb/IS/IS907.asp). (Continued on the following page.)
Page 40
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
WORKPLACE VIOLENCE THREATS Visual 38 (Continued) The Active Shooter Awareness Virtual Roundtable (Webinar) (https://connect.hisn.gov/asaware2011), Department of Homeland Security (2011): This roundtable will better prepare you to deal with an active shooter situation and to recognize dangerous behavior before it turns deadly.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 41
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 39
Key Points The next section will focus on information and cyber threats.
Page 42
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 40
Key Points Typically, a workplace uses computers to manage day-to-day operations. Organizations control access to computers through computer accounts and passwords. If an unauthorized person obtains the account name and/or password, the security process can fail. Other types of information or intellectual propertysuch as copyrights, trademarks, patents, industrial design rights, and trade secretsmay be stored on paper in locked offices or other secure areas. If unauthorized people gain access to those areas by circumventing security protocols, the information may be compromised. Today, portable electronic devices (e.g., laptop computers, thumb drives, smart phones, etc.) have a large storage capacity that allows for the storage of thousands of files, which may include sensitive information. For example, a handheld device may contain names, contact lists, company proprietary information, and even passwords. Gaining unauthorized access to these types of devices can severely impact an organizations security.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 43
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 41
Key Points Scenario: As Betty walks toward the loading dock to wait for a delivery, she notices someone looking into one of the trash bins behind the building. The man looks around and sees Betty looking at him. He smiles as he quickly turns away from the trash bins. What should Betty do?
Page 44
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 42
Key Points Organizations need to collect and store information to serve their clients and customers. The more a business knows about its customers, the more able it is to meet their needs. Information about clients and customers often is sensitive and needs to be protected from unauthorized access. Clients and customers trust that businesses follow common privacy law principles based on the Federal laws listed on the visual.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 45
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 43
Key Points Personally identifiable information (PII) is any information that permits the identity of an individual to be inferred directly or indirectly. Employees of organizations that collect PII must protect it by: Applying the need to know principle before disclosing PII to other personnel. (Literally, other personnel must demonstrate a valid and work-related need to know the information.) Challenging the need for the requested PII before sharing it. Considering PII materials as for official use only materials. Limiting the collection of PII for authorized purposes only.
Source: DHS Handbook for Securing Sensitive Personally Identifiable Information
Page 46
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 44
Key Points Examples of PII include: Name. Social Security number. Mailing address/ZIP code. Telephone number. Account numbers. Date and place of birth. Biometric identifiers (e.g., fingerprints). Certificate/license numbers. Vehicle identifiers including license plate numbers. Internet protocol (IP) addresses. Email addresses. Photographic facial images.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 47
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 45
Key Points To safeguard PII or confidential information, employees should: Store sensitive information in a designated room or area that has access control measures to prevent unauthorized access by visitors or members of the public (e.g., locked desk drawers, offices, and file cabinets). Destroy all sensitive information by the appropriate methods (e.g., burn bag or paper shredder) when it is no longer needed. Never email sensitive information to unauthorized individuals. Never leave sensitive information on community printers. Take precautions to avoid the loss or theft of computer devices and removable storage media. Notify an immediate supervisor if a privacy incident has occurred.
Source: DHS Handbook for Securing Sensitive Personally Identifiable Information
Page 48
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 46
Key Points Just as with physical security, all employees play an integral role in keeping their organization's information from ending up in the wrong hands. One easy, common-sense solution is to adhere to a clean desk policy. Here are some simple steps: Set or schedule a date or time to clear paperwork. Use secure recycling bins for office paper that is no longer needed. Do not print emails or sensitive documents unnecessarily. If possible, handle each piece of paper only onceact on it, file it, or dispose of it. Consider scanning paper items and storing them on a computer. Always clear desktops or workspaces before going home.
Source: Safeguarding Sensitive but Unclassified (For Official Use Only) Information
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 49
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 47
Key Points Scenario: 1. Maria stops by and drops a sensitive document onto Pete's desk for Pete to photocopy. A visitor walks up and waits patiently while Maria and Pete are talking. Maria leaves. 2. The visitor asks Pete if Maria is available to answer a few questions for him. Pete smiles and says that Maria was just here and offers to catch her before she reaches her office. The visitor watches as Pete goes after Maria. 3. The visitor reaches for the folder to look inside it. What should Pete have done differently?
Page 50
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 48
Key Points Social engineering is one of the simplest, most common, and most successful methods for obtaining information. It is essentially the act of tricking people into revealing personal information, passwords, or other information that can compromise a security system. Social engineers can be very convincing and can trick or coerce people into revealing information through: Telephone Interactions: In a telephone social engineering attack, the hacker contacts the victim pretending to be someone else, such as a service technician or fellow employee, and attempts to gather information that may seem innocuous to the victim. Face-to-Face Interactions: Social engineers may try to collect information about their victims at trade shows or conferences related to the victims line of work, personal interest, or hobby. Typically, the social engineer will strike up conversations with potential victims. The event gives them a common interest to break the ice. Social engineers may also go as far as setting up a display or booth to collect information under the pretense of offering a solution or a product related to the event. Email/Web Interactions: Social engineering also can be conducted via email, postal mail, surveys, or other forms of written contact.
(Continued on the following page.)
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 51
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 48 (Continued) Be suspicious of anyone requesting information, especially by phone, Web, or email, and always verify the identity of the person or organization making the request. Before entering personal information online, verify that the URL starts with https:// and that you see a closed padlock icon in your browser (often found in the lower right-hand corner of your screen). Contact the organization by telephone if there is any doubt as to the authenticity of an email or Web site. Contact security if anyone requests your account name or password(s).
Page 52
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 49
Key Points Scenario: Jeans calls an employee she is targeting named Mark. She tells him that there was an attempt to hack into the company network over the weekend and that she needs to determine if there was any unauthorized access to his user account. Jean requests Marks user name and password and he provides her the information. What should Mark have done differently?
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 53
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 50
Key Points Activity Purpose: To reinforce your understanding of how and when social engineering can take place. Instructions: Working as a team: 1. On the following page in the Student Manual, write a fictional scenario in which an act of social engineering takes place. There is an example provided. 2. Describe what the employee in your scenario should have done differently. 3. Select a spokesperson and be prepared to present your scenarios in 5 minutes. (Continued on the following page.)
Page 54
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 50 (Continued) Scenario EXAMPLE: It is late on Thursday afternoon and George is trying to finish his report before the end of the day. A few of his coworkers come by his desk and invite him to take a break with them for coffee in the cafeteria downstairs. Luckily, George finds himself at a good stopping point, so it is a perfect time for him to leave his desk for a few minutes. George goes with his coworkers. In a rush, George leaves the document that he was working on open on his computer screen. What Should Be Done Differently? EXAMPLE: George should not have left his workstation unsecured. It is possible that this may be a situation where social engineering is taking place. One of his coworkers may have lured George away from his desk in an attempt to allow another individual to gain unauthorized access to his computer. You should always log off or lock your computer, and secure any important papers and personal belongings (e.g., purse, BlackBerry) before leaving your work area.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 55
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 51
Key Points In the cyber world, a threat is any person, event, or environmental factor that could impact or harm a protected object. Vulnerability is a weakness that can be exploited by a threat. It is the hole through which a threat gains access to protected objects or information. Common cyber threats and vulnerabilities include those listed on the visual. Details are provided below. Active Threats: Hackers: Hackers attempt to gain unauthorized access to computer networks or systems by intentionally bypassing or compromising their security. Hackers may exploit their illegal access by stealing information or otherwise causing harm to the system or its owners, customers, or users. Cyber Warfare: Cyber warfare is the use of computers and other devices to attack an enemy's information systems as opposed to an enemy's armies or factories. Malicious Code: Malicious code is any software or program designed to disrupt the normal operation of a computer by allowing an unauthorized process to occur or by granting unauthorized access. Often, the term virus is used to refer to all types of malicious code, but malicious code comes in many forms, including:
(Continued on the following page.)
Page 56
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 51 (Continued) o o o o o Viruses Worms Trojan horses Adware Spyware
Information Gathering: Terrorists and other criminals use cyber tools as part of their information-gathering and espionage activities. Identity Theft: Identity theft occurs when someone uses your personal identifying information, like your name, Social Security number, or credit card number, without your permission, to commit fraud or other crimes.
Systems Threats: Peer-to-Peer Software: Peer-to-peer (P2P) software provides direct access to another computer. Some examples include file sharing, Internet meeting, or chat messaging software. Some P2P programs also have remote-control capabilities. Remote-control software and sites allow users to take control of a computer from another computer somewhere else in the world.
Source: Individual Use and Operation of DHS Information Systems/Computers, DHS Management Directive 4900
Loss of Removable Media: Removable media are data storage devices that can easily be removed and transported. The most common forms of removable media are: o Compact discs (CDs). o Portable hard drives. o USB drives (thumb drives, flash drives, mini drives, micro vaults, memory sticks, and pen drives). The storage capacity and small physical size of these devices make them difficult to control. They offer a convenient means of stealing data from or loading data onto another computer.
Passive Threats: Passive threats cause damage without intending to do so. They are unpredictable and difficult to guard against. Even with the best of security systems in place, it is still important to back up information and have disaster recovery plans in place. Examples of passive threats include: o Natural hazards o Power failures o Software glitches o Human error
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 57
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 52
Key Points Some of the protective measures to address potential cybersecurity threats are identified on the visual. They include: Firewalls and virus protection systems. Password procedures. Information encryption software. Computer access control systems. Computer security staff background checks (at initial hire and periodically thereafter). Computer security staff training and 24/7 on-call technical support. Intrusion detection systems. System recovery and restoration plans, including redundant and backup systems and offsite backup data storage.
Page 58
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 53
Key Points Employees should never give their user names or passwords to anyone and should create a strong password that: Includes a minimum of eight characters with a combination of: o Alpha characters in both uppercase and lowercase; o Numbers; and o Special characters (- ! @ # $ % ^ & * ( ){ } [ ] | + \ - < > ? /) or alternate alpha characters. Does not consist solely of a dictionary word in any language, proper noun, name of person/child, pet, or fictional character. Does not use information that a hacker could easily obtain or guess about you, such as a Social Security number, address, birth date, or telephone number.
What are some good strong passwords?
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 59
IS-906: Workplace Security Awareness
INFORMATION AND CYBER THREATS Visual 54
Key Points Scenario: Youve spent a long morning working on some sensitive and confidential documents. When lunchtime arrives, you decide to go out with some coworkers. What should you do before leaving your office? What should you do before you leave?
Page 60
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
COURSE SUMMARY Visual 55
Key Points DHS launched the If You See Something, Say Something (http://www.dhs.gov/files/reportincidents/see-something-say-something.shtm) campaign as part of the national Suspicious Activity Reporting initiative. The campaign is a simple and effective program to raise public awareness of indicators of terrorism, crime, and other threats and emphasize the importance of reporting suspicious activity to the proper transportation and law enforcement authorities. The campaign emphasizes that everyone should: Be vigilant. Take notice of surroundings. Report suspicious items or activities to local authorities immediately.
Note: The If You See Something, Say Something campaign was originally used by New Yorks Metropolitan Transportation Authority (MTA), which licensed the use of the trademarked slogan to DHS to help with antiterrorism and anticrime efforts.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 61
IS-906: Workplace Security Awareness
COURSE SUMMARY Visual 56
Key Points Actions taken at the workplace will be dependent upon circumstances. However, all employees can contribute to workplace security by: Identifying threats and vulnerabilities that affect workplace security. Avoiding complacency. Observing with all senses. Being aware of unusual events and activities. Noticing unusual or suspicious behavior. Knowing whom to call if something is not right. Getting assistanceNOT attempting to handle a potential situation alone.
Remember, security is everyones job. Take it seriously.
Page 62
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
COURSE SUMMARY Visual 57
Key Points Additional helpful resources related to workplace security are listed in the Student Manual. The resources include training, Web pages, a video (pictured on the visual), and several publications. Training Chemical Security Awareness Training (https://chemicalsecuritytraining.dhs.gov/) is an interactive tool available free to chemical facilities nationwide to increase security awareness. The training is designed for all facility employees, not just those traditionally involved in security. IS-106.12 Workplace Violence Awareness Training 2012 (http://training.fema.gov/EMIWeb/IS/is106.12.asp) is designed to give employees awareness of violence in the workplace, how to recognize the warning signs, and what actions to take to prevent or minimize violence. IS-907 Active Shooter: What You Can Do (http://training.fema.gov/EMIWeb/IS/IS907.asp) provides guidance to individuals, including managers and employees, so that they can prepare to respond to an active shooter situation. IS-912 Retail Security Awareness: Understanding the Hidden Hazards (http://training.fema.gov/EMIWeb/IS/is912.asp) is to make persons involved in commercial retail operations aware of the actions they can take to identify and report suspicious purchases or thefts of products that actors could use in terrorist or other criminal activities.
(Continued on the following page.)
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 63
IS-906: Workplace Security Awareness
COURSE SUMMARY Visual 57 (Continued) Web Pages DHS Federal Protective Services Ensuring Building Security Web page (http://www.dhs.gov/files/programs/gc_1269012811362.shtm) provides guidance for handling building emergencies, including suspicious mail, phone threats, bomb or weapon threats, and chemical or biological threats. If You See Something, Say Something Campaign1 (http://www.dhs.gov/files/reportincidents/see-something-say-something.shtm) is a DHS program to raise public awareness of indicators of terrorism and violent crime. Password Meter (http://www.passwordmeter.com) is an interactive tool that helps you gauge the strength of your password.
Videos If You See Something, Say Something (http://www.dhs.gov/files/reportincidents/seesomething-say-something.shtm) is a video for the general public that provides information about potential indicators of criminal and terrorist activity and describes the importance of reporting suspicious activity to the proper State and local law enforcement authorities. Whats in Store: Ordinary People, Extraordinary Events (http://www.dhs.gov/files/programs/gc_1259859901230.shtm#3) is a video for retail and shopping center employees that provides information to help employees identify and report suspicious activities and threats in a timely manner.
Publications DHS Active Shooter materials describe how to respond when an active shooter is in your vicinity. Materials include: o Active Shooter Booklet (http://www.dhs.gov/xlibrary/assets/active_shooter_booklet.pdf). o Active Shooter Pocket Card (http://www.dhs.gov/xlibrary/assets/active_shooter_pocket_card.pdf). o Active Shooter Poster (http://www.dhs.gov/xlibrary/assets/active_shooter_poster.pdf). DHS Best Practices for Safe Mail Handling (http://www.dhs.gov/xlibrary/assets/isc_safe_mail_handling-2007.pdf) identifies best mailroom operations practices used by Federal agencies. DHS Bomb Threat Checklist (https://chemicalsecuritytraining.dhs.gov/TRIPwire_Bomb_Threat_Call_Procedures.pdf) includes bomb threat call procedures and a handy checklist for recording bomb threat information.
(Continued on the following page.)
If You See Something, Say Something used with permission of the New York Metropolitan Transportation Authority (MTA).
Page 64
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
COURSE SUMMARY Visual 57 (Continued) Publications (Continued) DHS Handbook for Safeguarding Sensitive Personally Identifiable Information (http://www.dhs.gov/xlibrary/assets/privacy/privacy_guide_spii_handbook.pdf) provides stepby-step guidance on how to identify and protect sensitive PII and simple instructions for encrypting and disposing of sensitive PII. Oregon Department of Human Services: Password and User Identification Security http://www.dhs.state.or.us/policy/admin/security/090_002.htm provides guidelines for creating and protecting unique user identifications and strong passwords. Safeguarding Sensitive but Unclassified (For Official Use Only) Information (http://www.dhs.gov/xlibrary/assets/foia/mgmt_directive_110421_safeguarding_sensitive_ but_unclassified_information.pdf) provides DHS policy regarding the identification and safeguarding of sensitive but unclassified information originating within DHS or received by DHS from other governmental and nongovernmental activities. U.S. Postal Inspection Service Guide to Mail Center Security (http://about.usps.com/publications/pub166.pdf) includes guidance for protecting your work site from package bombs, bomb threats, and chemical, biological, and radiological threats.
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 65
IS-906: Workplace Security Awareness
COURSE SUMMARY Visual 58
Key Points 1. Take a few moments to review the Student Manual and identify any questions. 2. Ensure that all questions are answered. 3. When taking the test . . . Read each item carefully. Enter the answers online.
You may refer to your Student Manual when completing the test. To receive a certificate of completion, you must take the 15-question multiple-choice exam and achieve a score of 75%. If desired, you may download and print the course exam and circle your responses on the paper copy before entering them online. The online exam questions and responses, however, are randomly generated and may not match the order presented in the printable copy. You must complete your test online. Certificates will be sent electronically to the email address entered during registration. To complete the course exam: Go to the IS-906: Workplace Security Awareness course (http://training.fema.gov/EMIWeb/IS/IS906.asp). Click on Take Final Exam.
Page 66
IS-906: Workplace Security Awareness Student Manual
March 2012
IS-906: Workplace Security Awareness
COURSE SUMMARY Visual 59
Key Points .
March 2012
IS-906: Workplace Security Awareness Student Manual
Page 67
IS-906: Workplace Security Awareness
This page intentionally left blank.
Page 68
IS-906: Workplace Security Awareness Student Manual
March 2012
You might also like
- Residual Risk Reduction (R3)Document42 pagesResidual Risk Reduction (R3)Project Sales CorpNo ratings yet
- Hexavalent Chromium PresentationDocument58 pagesHexavalent Chromium PresentationGuru SamyNo ratings yet
- Crane Safety Program at University of NevadaDocument31 pagesCrane Safety Program at University of NevadaSs SelvanNo ratings yet
- Indus Safety-SyllabusDocument28 pagesIndus Safety-Syllabuskalyan1990No ratings yet
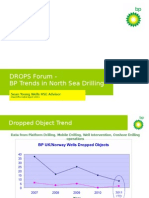
- DROPS Forum - BP Trends in North Sea Drilling: Sean Young Wells HSE AdvisorDocument7 pagesDROPS Forum - BP Trends in North Sea Drilling: Sean Young Wells HSE AdvisorMulatua SiraitNo ratings yet
- Basic Scaffolder TrainingDocument63 pagesBasic Scaffolder TrainingAfshad100% (1)
- Forklift Pedestrian SafetyDocument12 pagesForklift Pedestrian SafetyGuru Raja Ragavendran NagarajanNo ratings yet
- Scaffold Towers CatalogDocument22 pagesScaffold Towers Catalogdox4printNo ratings yet
- Accident - Incident InvestigationDocument62 pagesAccident - Incident InvestigationSubhendu HatiNo ratings yet
- Design and Implement Behavioural Safety Programme (SOH CHEE SENG)Document95 pagesDesign and Implement Behavioural Safety Programme (SOH CHEE SENG)Chauhan VineetNo ratings yet
- Office Safety PosterDocument2 pagesOffice Safety PosterAndrei MargaritNo ratings yet
- Risk Evaluation/Assessment List EF/2018-036-GENERAL/rec023Document39 pagesRisk Evaluation/Assessment List EF/2018-036-GENERAL/rec023Ionut FloricaNo ratings yet
- Problems With Safety Observation Reporting - A Construction Industry Case StudyDocument34 pagesProblems With Safety Observation Reporting - A Construction Industry Case StudyRadger Teddy ManuelNo ratings yet
- NEBOSH Favourite Questions IGC2Document5 pagesNEBOSH Favourite Questions IGC2naveed ahmadNo ratings yet
- LCM 48 Hours Advance OSH CourseDocument6 pagesLCM 48 Hours Advance OSH CourseLenaj Ebron50% (2)
- Policies - General Health and Safety SOPDocument86 pagesPolicies - General Health and Safety SOPOfficial 1960No ratings yet
- Environmental Tour ChecklistDocument6 pagesEnvironmental Tour ChecklistintanretnoNo ratings yet
- Conducting Drills and Exercises GuideDocument114 pagesConducting Drills and Exercises GuideblytonbergNo ratings yet
- Environmental Safety EssentialsDocument58 pagesEnvironmental Safety EssentialsLANSANGAN RHIZZA MAE B.No ratings yet
- Confined Space Rescue PlanDocument4 pagesConfined Space Rescue PlanFranscois Van RooyenNo ratings yet
- Tip Safety PlanDocument28 pagesTip Safety PlanTC Nihal AlcansoyNo ratings yet
- Health and Safety News - June 2009Document33 pagesHealth and Safety News - June 2009HealthSafety100% (3)
- NVQ Level 6 Diploma Course SyllabusDocument1 pageNVQ Level 6 Diploma Course SyllabusNaeem AbbasNo ratings yet
- Bloodborne Pathogen Exposure Control PlanDocument6 pagesBloodborne Pathogen Exposure Control Planapi-630289708No ratings yet
- Task Exposure AnalysisDocument24 pagesTask Exposure AnalysisDaren Bundalian RosalesNo ratings yet
- Safety - Mast ClimbingDocument78 pagesSafety - Mast ClimbingparadigmanNo ratings yet
- Safety and HealthDocument2 pagesSafety and HealthGonzalo Peñafiel VelasquezNo ratings yet
- Emergency Action Plan - 3Document18 pagesEmergency Action Plan - 3Nasih TrNo ratings yet
- Stanford's Guide to Preventing Slips, Trips and FallsDocument19 pagesStanford's Guide to Preventing Slips, Trips and FallsSagar TannaNo ratings yet
- Emergency Action PlanDocument10 pagesEmergency Action Planrahardian_amandaNo ratings yet
- 2010 Safety ManualDocument290 pages2010 Safety ManualPaul Januario G. RostrataNo ratings yet
- CO Tabletop ScenariosDocument16 pagesCO Tabletop ScenariosRizkiNo ratings yet
- Machinery Safety 2Document5 pagesMachinery Safety 2erkingulerNo ratings yet
- 2.1 - Machine GuardingDocument6 pages2.1 - Machine Guardingkumar100% (1)
- Lecture 4-Material and Machine SafetyDocument142 pagesLecture 4-Material and Machine Safetydkaviti100% (1)
- Fire WardenDocument74 pagesFire Wardeneams2013No ratings yet
- Pallet Racking Inspection Checklist GuideDocument9 pagesPallet Racking Inspection Checklist GuidePiyush VirmaniNo ratings yet
- Principles of Safety ManagementDocument70 pagesPrinciples of Safety ManagementAyushi SharmaNo ratings yet
- Safety SignageDocument14 pagesSafety SignageChef ShaneNo ratings yet
- SCAT Chart - Systematic Cause Analysis Technique - SCAT ChartDocument4 pagesSCAT Chart - Systematic Cause Analysis Technique - SCAT ChartponggoooNo ratings yet
- 3M Dbi-Sala Fall Protection: Full Line CatalogDocument132 pages3M Dbi-Sala Fall Protection: Full Line CatalogBenjamin HidalgoNo ratings yet
- Emergency Action Plan TemplateDocument6 pagesEmergency Action Plan Templatearnel sungkipNo ratings yet
- Working Alone Risk AssessmentDocument4 pagesWorking Alone Risk Assessment633dNo ratings yet
- General Safety ManualDocument17 pagesGeneral Safety Manualrung_na_uy2011100% (1)
- ErgonomicDocument62 pagesErgonomicSarah Febiana100% (1)
- Fall Protection DefinitionsDocument5 pagesFall Protection DefinitionsalphadingNo ratings yet
- AAC Site Safety PlanDocument427 pagesAAC Site Safety PlanRemon Ma EaldamaNo ratings yet
- Risk AssesmentDocument23 pagesRisk AssesmentMohamed ReezaNo ratings yet
- Behavioral Based Safety Management in IndustriesDocument72 pagesBehavioral Based Safety Management in IndustriesVudugundla KodandapaniNo ratings yet
- Workplace Induction and Orientation 1Document27 pagesWorkplace Induction and Orientation 1Gilbert GillNo ratings yet
- Health Safety Environmental Manager in Houston TX Resume Fabian Gregory WomacDocument2 pagesHealth Safety Environmental Manager in Houston TX Resume Fabian Gregory WomacFabianGregoryWomacNo ratings yet
- Health and Safety Awareness TrainingDocument186 pagesHealth and Safety Awareness TrainingAbi Gemala100% (1)
- Construction Project Public Protection ANSI StandardDocument49 pagesConstruction Project Public Protection ANSI StandardJeerawatNo ratings yet
- Employee Safety and HealthDocument55 pagesEmployee Safety and Healthnida younas0% (1)
- CSHP Checklist 2011Document2 pagesCSHP Checklist 2011JenniferValle0% (1)
- 2157 EISF June 2017 Security Risk Management A Basic Guide For Smaller NGOsDocument80 pages2157 EISF June 2017 Security Risk Management A Basic Guide For Smaller NGOsHabibullah MirhazarNo ratings yet
- Tun Razak Exchange, Retail Plot 1: Appendix 4 - Emergency Response PlanDocument32 pagesTun Razak Exchange, Retail Plot 1: Appendix 4 - Emergency Response PlanMatthew Mohan PerumalNo ratings yet
- SWP Work at Height CBTDocument52 pagesSWP Work at Height CBTRasLDK100% (1)
- Everything Under The SunDocument26 pagesEverything Under The Sunms162223No ratings yet
- Connecting The Sun Shorter VersionDocument24 pagesConnecting The Sun Shorter VersionPauloNo ratings yet
- Ffi Ffi#ffiffi #Ffiffi: Tii/Ited Natioi/S F (-'QI/fIMTC ND - SCX) IAL.Document7 pagesFfi Ffi#ffiffi #Ffiffi: Tii/Ited Natioi/S F (-'QI/fIMTC ND - SCX) IAL.PauloNo ratings yet
- Executive Summary and PrefaceDocument8 pagesExecutive Summary and PrefacePauloNo ratings yet
- R IntroDocument103 pagesR Introtajjj9No ratings yet
- Structure of SunDocument10 pagesStructure of SunSony RamaNo ratings yet
- The Distance To The SunDocument6 pagesThe Distance To The SunPauloNo ratings yet
- Training Tscs06 Security TrainerDocument2 pagesTraining Tscs06 Security TrainerPauloNo ratings yet
- BCCM - Exam 2 - To Be Administered After Session 12 FinalDocument1 pageBCCM - Exam 2 - To Be Administered After Session 12 FinalPauloNo ratings yet
- BCCM - Exam 4 - To Be Administered After Session 25 FinalDocument1 pageBCCM - Exam 4 - To Be Administered After Session 25 Finaltomana mansorNo ratings yet
- Home Land Security StratPlan2015Document66 pagesHome Land Security StratPlan2015rio2jeNo ratings yet
- BCCM - Exam 3 - To Be Administered After Session 17 FinalDocument1 pageBCCM - Exam 3 - To Be Administered After Session 17 FinalPauloNo ratings yet
- BCCM - Exam 1 - To Be Administered After Session 6 FinalDocument1 pageBCCM - Exam 1 - To Be Administered After Session 6 FinalPauloNo ratings yet
- Modem ManualDocument82 pagesModem Manualcwgirlatheart100% (1)
- National Cyber Security StrategiesDocument15 pagesNational Cyber Security StrategieslimaydaNo ratings yet
- BCCM - Sessions 10 and 11 - Issue Paper Presentations and DiscussionsDocument2 pagesBCCM - Sessions 10 and 11 - Issue Paper Presentations and DiscussionsPauloNo ratings yet
- BCCM - Session 23 - Handout III - Pandemic Influenza Tabletop Exercise FinalDocument2 pagesBCCM - Session 23 - Handout III - Pandemic Influenza Tabletop Exercise FinalPauloNo ratings yet
- BCCM - Session 23 - Pandemic Preparedness, Planning and Table Top Exercise (Final)Document14 pagesBCCM - Session 23 - Pandemic Preparedness, Planning and Table Top Exercise (Final)PauloNo ratings yet
- BCCM - Session 21 - Power PointDocument18 pagesBCCM - Session 21 - Power PointPauloNo ratings yet
- BCCM - Session 22 - Power PointDocument16 pagesBCCM - Session 22 - Power PointPauloNo ratings yet
- BCCM - Session 20 - Crisis Communications IIDocument24 pagesBCCM - Session 20 - Crisis Communications IIPauloNo ratings yet
- BCCM - Course SyllabusDocument4 pagesBCCM - Course SyllabusPauloNo ratings yet
- BCCM - Session 23 - Pandemic Preparedness, Planning and Table Top Exercise (Final)Document14 pagesBCCM - Session 23 - Pandemic Preparedness, Planning and Table Top Exercise (Final)PauloNo ratings yet
- BCCM - Course SyllabusDocument4 pagesBCCM - Course SyllabusPauloNo ratings yet
- BCCM - Session 23 - Handout IV - Pandemic Influenza Business Planning ToolkitDocument33 pagesBCCM - Session 23 - Handout IV - Pandemic Influenza Business Planning ToolkitPauloNo ratings yet
- BCCM - Session 22 - Business EthicsDocument26 pagesBCCM - Session 22 - Business EthicsPauloNo ratings yet
- BCCM - Session 21 - Crisis of Confrontation, MalevolenceDocument46 pagesBCCM - Session 21 - Crisis of Confrontation, MalevolencePauloNo ratings yet
- BCCM - Session 22 - Business EthicsDocument26 pagesBCCM - Session 22 - Business EthicsPauloNo ratings yet
- BCCM - Session 22 - Business EthicsDocument26 pagesBCCM - Session 22 - Business EthicsPauloNo ratings yet
- III B Tech I Sem r10Document5 pagesIII B Tech I Sem r10kumaraswamireddyNo ratings yet
- RSA Archer Integration GuideDocument26 pagesRSA Archer Integration GuideMostafa EhabNo ratings yet
- IHE Participation Lessons from Small VendorDocument19 pagesIHE Participation Lessons from Small VendorSubhashreeNo ratings yet
- FM 3080 Hind: Fixed Mount Barcode ScannerDocument283 pagesFM 3080 Hind: Fixed Mount Barcode ScannerPaul SeckerNo ratings yet
- IaaS Solution BrochureDocument6 pagesIaaS Solution BrochureblussierttNo ratings yet
- MYD IT Solutions Technical Support Written ExamDocument2 pagesMYD IT Solutions Technical Support Written Examمحمد يوسفNo ratings yet
- DDOS - 6.0 - DDOS - Upgrade - 1Document7 pagesDDOS - 6.0 - DDOS - Upgrade - 1thi NNo ratings yet
- WireGuard - RFCDocument9 pagesWireGuard - RFCbasilis mitzelosNo ratings yet
- How To Create Signed Based Reclassification in Group ReportingDocument9 pagesHow To Create Signed Based Reclassification in Group ReportingJose EximenoNo ratings yet
- Menu - 634637063125928485 - CS6105 Compiler Design SyllabusDocument1 pageMenu - 634637063125928485 - CS6105 Compiler Design SyllabusArchit100% (1)
- TMJavaBookOne PDFDocument59 pagesTMJavaBookOne PDFRavi KushwahNo ratings yet
- Qualcomm Snapdragon 662 Mobile Platform Product BriefDocument2 pagesQualcomm Snapdragon 662 Mobile Platform Product Briefichida_hiroshiNo ratings yet
- Call Adobe Form Through ABAP Web DynproDocument47 pagesCall Adobe Form Through ABAP Web DynproGobara DhanNo ratings yet
- Proteccion df30Document406 pagesProteccion df30Rodrigo AndresNo ratings yet
- Huawei HG8245H ONT DatasheetDocument4 pagesHuawei HG8245H ONT DatasheetAgus WahyuNo ratings yet
- Class 7th 1st Q&ADocument20 pagesClass 7th 1st Q&AaddayesudasNo ratings yet
- SunziDocument18 pagesSunziJen Hui YapNo ratings yet
- ONEXAM Online Examination System Project SynopsisDocument4 pagesONEXAM Online Examination System Project Synopsisbahubali king0% (1)
- TMS Edit Controls Pack Developers GuideDocument9 pagesTMS Edit Controls Pack Developers GuideMohamed WajeedNo ratings yet
- Class 6 Sample Paper II AnnualsDocument3 pagesClass 6 Sample Paper II AnnualsmkbbhawanipatnaNo ratings yet
- Novell Groupwise: Troubleshooting: 2 Solutions To Common ProblemsDocument107 pagesNovell Groupwise: Troubleshooting: 2 Solutions To Common ProblemsEnriquePhoenixNo ratings yet
- Nipper Studio User ManualDocument30 pagesNipper Studio User ManualchiweekokNo ratings yet
- HD-VP210 Spec. V1.0 and User ManualDocument7 pagesHD-VP210 Spec. V1.0 and User ManualDitzNo ratings yet
- CIT-110 Assignment 03 Body Mass IndexDocument4 pagesCIT-110 Assignment 03 Body Mass IndexStephen RamosNo ratings yet
- Second Syllabus IT E 203 Professional Elective 2 - Web Systems and TechnologiesDocument6 pagesSecond Syllabus IT E 203 Professional Elective 2 - Web Systems and TechnologiesMichaelangelo R. SerranoNo ratings yet
- Advanced Windows Power Shell ScriptingDocument28 pagesAdvanced Windows Power Shell ScriptingDiego TorresNo ratings yet
- CTC 3D Printer ManualDocument38 pagesCTC 3D Printer ManualNimmala Ganesh100% (1)
- Apex Tutorial in Tutorial PointsDocument27 pagesApex Tutorial in Tutorial Pointsilias ahmed100% (1)
- HelpNDoc User Manual PDFDocument87 pagesHelpNDoc User Manual PDFDragos CirsteaNo ratings yet