Professional Documents
Culture Documents
OPENVPN - The Easy Tutorial... 2
Uploaded by
gurukosOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
OPENVPN - The Easy Tutorial... 2
Uploaded by
gurukosCopyright:
Available Formats
OPENVPN - The Easy Tutorial - Tutorial
http://www.openmaniak.com/openvpn_tutorial.php
OpenVPN Tutorial Last update: 12-03-2008 Search What is OpenVPN? Screenshots Prerequisites & Installation Tutorial OpenVPN -----SECURITY MODE----------Transparent Tunnel Static key SSL & PKI (certificates) -----CASE STUDY----------IP VPN (TUN) Ethernet VPN (TAP) VPN Advanced Settings ---------------Bridging Routing
Tool Install Ergonomy Forum
Details
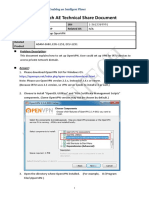
INSTALL OPENVPN: Follow the OpenVPN installation tutorial. CLIENT/SERVER ARCHITECTURE: Upon the two OpenVPN boxes, you have to declare one as server and the other as client. In some scenarios, each box can be declared as server or client, but in other scenarios you must specifically choose a device as client and the other as server. Let us see when. Before establishing the SSL VPN, the client first reaches the server on a specific port, whereas the server doesn't need to reach the client. Let's take an example where you are in a professional environment and want to establish a VPN with a device connected directly to the Internet, let's say a box at your home. In this frequent case, the client can reach the server but not the contrary. This is due to the fact that the client is located in a local network and reaches the internet via a proxy or Firewall which will substitute its own IP address or another one (Hide NAT) for the source IP address. Nevertheless, when the tunnel is created, the bi-directional traffic inside it is of course possible.
CONFIGURATION FILE: Create a file where you store your OpenVPN configuration. In our example, we will call this file config.txt and save it in the /home/user/ or "C:\Program Files\OpenVPN \config\" directory depending on whether it is a Linux/Unix or Microsoft machine. The configuration settings are presented in the next paragraphs. CLIENT/SERVER DESIGNATION: SERVER # SERVER IP ADDRESS # The Client WAN IP address is not # needed TUNNEL MODE: You can choose between an IP (TUN driver) and an Ethernet (TAP driver) tunnel. IP tunneling is also referred as routing mode, and Ethernet tunneling as bridging mode. Prefer the IP tunnel mode (default setting) unless you need to pass Ethernet traffic such as NetBIOS inside the tunnel. TUNNEL PORT: Default source and destination tunneling port is UDP 1194. You should keep the default setting unless you need to change it for Firewall reasons otherwise you can keep it. Prefer UDP ports. The use of TCP can lead to degraded performances. CLIENT # SERVER IP ADDRESS remote 100.0.0.1 #
1 of 5
2/7/2009 6:33
OPENVPN - The Easy Tutorial - Tutorial
http://www.openmaniak.com/openvpn_tutorial.php
As the majority of the applications uses TCP, if you opt for TCP tunneling, you will create a TCP over TCP tunnel. This is not recommended because in case of packets retransmissions on the interior TCP tunnel, recomputation will occur in both tunnels leading to slow performances such as high response time. Thus, prefer the UDP protocol to tunnel your application since contrary to TCP, it does not suffer from an overhead error checking mechanism.. Read this article to get details about the problems with TCP over TCP tunnels. SERVER and CLIENT
# TCP OR UDP TUNNEL # TCP tunnel proto tcp # UDP tunnel is recommended proto udp # use TCP or UDP but not both # # TCP OR UDP PORT port 1194 FIREWALL SETTINGS: You must ascertain that your OpenVPN client IP address can reach the OpenVPN server IP address and the TCP/UDP port. Here is an example of a security rule that can be implemented on the Firewall illustrated in the picture below.
Because of to the simplicity of the OpenVPN configurations, problems establishing a connection are often due to IP or port restrictions on the client and/or server side. ETHERNET/IP TUNNEL: You can choose to build either Ethernet (Bridged) or IP (Routed) VPNs with the help of respectively the TAP or TUN network drivers. TAP/TUN are available on all the platforms and are already bundled with the Linux 2.4 kernel or higher. Prefer TUN (default setting) unless you need to pass Ethernet traffic such as NetBIOS inside the VPN. To check whether or not the TUN/TAP drivers are properly loaded: #lsmod | grep tun tun 12672 1 Note that the "tun" driver is also the TAP driver. If you don't receive any answer, you can load the kernel module as follows: #modprobe tun SERVER and CLIENT
# ETHERNET OR IP TUNNEL # "dev tun" will create a routed IP tunnel dev tun # "dev tap" will create an Ethernet tunnel dev tap # use "dev tun" or "dev tap" but not both OPENVPN SECURITY ARCHITECTURE: Transparent tunnel: OpenVPN just tunnels the data without authentication, confidentiality, or integrity. In other words there is no security checks whatsoever, and the data can be read as it passes through the tunnel. SERVER and CLIENT
# Client AND Server configs # No integritiy (hash function # algorithm) auth none # No encryption (cipher algorithm) cipher none Preshared keys: A secret and permanent key is shared between the VPN gateways. First create the preshared keys with the preshared keys creation tutorials.
2 of 5
2/7/2009 6:33
OPENVPN - The Easy Tutorial - Tutorial
http://www.openmaniak.com/openvpn_tutorial.php
SERVER and
CLIENT
# PRESHARED KEYS # Linux system static /home/user/openvpn/key.txt # Windows system static "C:\\Program Files\\OpenVPN\\config\\key.txt" #openvpn /home/teddybear/openvpn/config.txt >openvpn "C:\Program Files\OpenVPN\config\config.txt" SSL/TLS: - SSL/TLS server or client: SERVER # SSL/TLS SERVER tls-server - Certificates and public keys: Each device must have its private and public keys, the latter being included in a certificate. The CA (Certification Authority) certificate must also be owned by each OpenVPN device. See the PKI Tutorial to understand the Public Key Infrastructure and know how to create private keys and certificates. SERVER # CERTIFICATES AND PRIVATE KEY # Authority certificate (CA public key) ca ca.key # Server certificate (server public key) cert server.crt # Server private key key server.key - Diffie-Hellmann (DH) settings: Once the OpenVPN peers are sure about each other's identity, DH can be used to create a shared secret key for the hash function and the cipher algorithm. By combining a DH private key with the other OpenVPN box DH public key, it is possible to calculate a shared secret that only the two OpenVPN peers know. See the SSL Tutorial to get information about how to create the DH settings. CLIENT # CERTIFICATES AND PRIVATE KEY # Authority certificate (CA public key) ca ca.key # Client certificate (client public key) cert client.crt # Client private key key client.key # SSL/TLS CLIENT tls-client CLIENT
SERVER # Diffie-Hellman settings dh dh1024.pem
CLIENT # No DH setting on the client #
This DH shared secret could be compared to the OpenVPN preshared key. These keys will be used by the symmetric ciphers and hash functions algorithms as shown in the two next paragraphs. CIPHER ALGORITHM SERVER and # CIPHER ALGORITHM cipher AES-256-CBC - The confidentiality is ensured with symmetric ciphers such as 3DES or AES to protect the data from being read. The OpenVPN default cipher algorithm is Blowfish. To check the available algorithms: #openvpn --show-ciphers DES-CBC 64 bit default key (fixed) IDEA-CBC 128 bit default key (fixed) RC2-CBC 128 bit default key (variable) DES-EDE-CBC 128 bit default key (fixed) DES-EDE3-CBC 192 bit default key (fixed) DESX-CBC 192 bit default key (fixed) BF-CBC 128 bit default key (variable) RC2-40-CBC 40 bit default key (variable) CAST5-CBC 128 bit default key (variable) RC5-CBC 128 bit default key (variable) RC2-64-CBC 64 bit default key (variable) AES-128-CBC 128 bit default key (fixed) AES-192-CBC 192 bit default key (fixed) AES-256-CBC 256 bit default key (fixed) CLIENT
3 of 5
2/7/2009 6:33
OPENVPN - The Easy Tutorial - Tutorial
http://www.openmaniak.com/openvpn_tutorial.php
CBC for Cipher Block Chaining is a cryptography operational modes used to encrypt data with a cipher block algorithm like the AES, DES or Blowfish. CBC uses small piece of data, instead of processing an entire block at a time, other cryptography operational mode are EBC, OFB, CFB. CBC mode is recommended. HASH FUNCTION ALGORITHM - The Integrity uses hash function algorithms to protect the data from being altered. HMAC is often used in addition with SHA1 or MD5. The OpenVPN default hash functions are HMAC-SHA1. To check the available algorithms: #openvpn --show-digests MD2 128 bit digest size MD5 128 bit digest size RSA-MD2 128 bit digest size RSA-MD5 128 bit digest size SHA 160 bit digest size RSA-SHA 160 bit digest size SHA1 160 bit digest size RSA-SHA1 160 bit digest size DSA-SHA 160 bit digest size DSA-SHA1-old 160 bit digest size MDC2 128 bit digest size RSA-MDC2 128 bit digest size DSA-SHA1 160 bit digest size RSA-SHA1-2 160 bit digest size DSA 160 bit digest size RIPEMD160 160 bit digest size RSA-RIPEMD160 160 bit digest size MD4 128 bit digest size RSA-MD4 128 bit digest size SERVER and CLIENT
# HASH FUNCTION ALGORYTHM auth MD5 "openvpn --show-tls" displays the cipher and message authentication code (MAC) used during the SSL/TLS negotiation. They should not be confounded with the cipher and MAC used to secure the OpenVPN tunnel. IP ADDRESSES: Choose the IP addresses you want to use inside the tunnel. Static IP addresses: In routed mode, two IP addresses (local and remote) inside a 30 bits subnet mask must be chosen. In bridge mode, one IP address for the local OpenVPN box and a subnet mask including the server IP address are chosen. SERVER # IP ADDRESSING # IP mode example: # Server IP: 10.8.0.1 ; Client IP: 10.8.0.2 ifconfig 10.8.0.1 10.8.0.2 # Bridge mode example # Server IP: 10.8.0.1 ifconfig 10.8.0.1 255.255.255.0 # Use bridged or routed settings but not # both # Client and Server must use the same # tunnel mode Dynamic IP addresses: In this case, the server owns a static IP address and provides IP addresses to the clients as a DHCP server. SERVER # DHCP SETTINGS # DHCP range # Server will take the first IP address server 10.8.0.0 255.255.255.0 OPTIONAL SETTINGS: OpenVPN offers a very large number of optional settings. Refer to the OpenVPN man page for assistance. LOG SETTINGS: The log verbosity is configured from 0 (minimum) to 15 (maximal). For a normal use, the "2" and "4" verbose levels will already provide sufficient logs. # Verbosity level. CLIENT # CLIENT ACCEPTS SERVER OPTIONS # The client should accept options pushed # by the server pull CLIENT # IP ADDRESSING # IP mode example: # Server IP: 10.8.0.1 ; Client IP: 10.8.0.2 ifconfig 10.8.0.2 10.8.0.1 # Bridge mode example # Client IP: 10.8.0.2 ifconfig 10.8.0.2 255.255.255.0 # Use bridged or routed settings but not # both # Client and Server must use the same # tunnel mode
4 of 5
2/7/2009 6:33
OPENVPN - The Easy Tutorial - Tutorial
http://www.openmaniak.com/openvpn_tutorial.php
#0 #1 #3 #9
-----
quiet except for fatal errors. mostly quiet, but displays non-fatal network errors. medium output, good for normal operation. verbose, good for troubleshooting SERVER and CLIENT
# LOG VERBOSITY # log verbosity setting, 0=min 15=max verb 3
OPENVPN USER: For security reasons, it's always better to run a software without the root privileges. You can reduce the OpenVPN daemon's privileges after initialization in order to operate as user "nobody". Another interesting security point is to limit the right OpenVPN has to access files after initialization with "chroot". Note that these two security settings are available under Linux/UNIX systems, but not under Windows. Another reason to prefer opens source tools like Linux OS ... SERVER and CLIENT
# OPENVPN SECURITY - Linux only # OpenVPN User user nobody # After initialization, OpenVPN can only # access a directory # The directory can be empty # OpenVPN process limitation chroot /etc/openvpn/ LAUNCH OPENVPN: Use the following syntax to launch OpenVPN. #openvpn path-to-config-file Below are two examples with Linux and Windows. The config file is "config.txt": #openvpn /home/teddybear/openvpn/config.txt >openvpn "C:\Program Files\OpenVPN\config\config.txt" LOG CHECK: The log should end will the following line: Initialization Sequence Completed This indicates that the OpenVPN tunnel has been created successfully. CONNECTIVITY TESTS: Ping is a common utility to check IP connectivities. The VPN gateway should ping the tunnel IP address of the other. For example, in our scenario, we ping the client tunnel IP address from the server: ping 10.8.0.2 OPENVPN PROCESS CHECK: Coming soon ...
Here are some OpenVPN default values: SETTING: Src & dest port: Tunnel mode: Symmetric cipher: Hash functions: Compression: Tunnel MTU: Verbose mode: Top of the page VALUE: UDP 1194 IP tunnel (tun mode) Blowfish - CBC (128 bits) HMAC - SHA1 (160 bits) NO 1500 bytes 0
5 of 5
2/7/2009 6:33
You might also like
- OpenVPN Installation and Configuration TutorialDocument6 pagesOpenVPN Installation and Configuration Tutorialsaulparada0% (1)
- Open VPNDocument105 pagesOpen VPNDusanNikolicNo ratings yet
- OpenVPN Server Ubuntu + Mikrotik ClientDocument11 pagesOpenVPN Server Ubuntu + Mikrotik ClientRaul Céspedes IchazoNo ratings yet
- How to set up OpenVPN in 15 stepsDocument7 pagesHow to set up OpenVPN in 15 stepsNguyễn Văn TânNo ratings yet
- OpenvpnDocument86 pagesOpenvpnIvar GarciaNo ratings yet
- Openvpn Client Server With ShorewallDocument5 pagesOpenvpn Client Server With ShorewallansaarNo ratings yet
- Tài liệu Open VPNDocument11 pagesTài liệu Open VPNhiệu úy mô kimNo ratings yet
- OpenVPN MikrotikDocument10 pagesOpenVPN MikrotikcamiloNo ratings yet
- OpenVPN 2.1Document68 pagesOpenVPN 2.1NeezmalNo ratings yet
- Pfsense OpenVPN TutorialDocument12 pagesPfsense OpenVPN Tutorialnavynmr3917100% (5)
- Openvpn - Build Secure Virtual Private Networks (VPN)Document20 pagesOpenvpn - Build Secure Virtual Private Networks (VPN)api-32211564No ratings yet
- 1xHOWTO Open VPNDocument26 pages1xHOWTO Open VPNFlorencio CoquillaNo ratings yet
- Linksys Rv082 VPN Router Interoperability Profile: C o M C OmDocument11 pagesLinksys Rv082 VPN Router Interoperability Profile: C o M C OmhackergenomaNo ratings yet
- DFL-Series VPN Configuration LabDocument102 pagesDFL-Series VPN Configuration LabLuis Diego Salas QuesadaNo ratings yet
- 01 - OpenVPNDocument47 pages01 - OpenVPNridaNo ratings yet
- OpenVPN - ArchWiki Guide to Basic Installation and ConfigurationDocument20 pagesOpenVPN - ArchWiki Guide to Basic Installation and ConfigurationBoubacarNo ratings yet
- Openvpn Belum SolvedDocument19 pagesOpenvpn Belum SolvedFamroziNo ratings yet
- Name Synopsis: Openvpn (Options ... )Document53 pagesName Synopsis: Openvpn (Options ... )Ed BedfordNo ratings yet
- Openvpn ManDocument35 pagesOpenvpn ManAnish ParameswaranNo ratings yet
- OpenVPN Setup Guide for VPN Server and ClientDocument3 pagesOpenVPN Setup Guide for VPN Server and Clientdarmi antiNo ratings yet
- AWS VPN Connection ConfigurationDocument5 pagesAWS VPN Connection ConfigurationArun ChinniNo ratings yet
- VPN 0ab8ac0559c93c0ffDocument5 pagesVPN 0ab8ac0559c93c0ffrahul.psNo ratings yet
- Openvpn - How To Set Up A Slackware Server and A Slackware ClientDocument13 pagesOpenvpn - How To Set Up A Slackware Server and A Slackware ClientebortolinNo ratings yet
- Vpnserver: Securing A Small Wireless Network Using VPNDocument5 pagesVpnserver: Securing A Small Wireless Network Using VPNpichuskiNo ratings yet
- Virtual Private Network (VPN) : IpsecDocument4 pagesVirtual Private Network (VPN) : Ipsecabhineet sharmaNo ratings yet
- OpenVPN and IPv6Document15 pagesOpenVPN and IPv6doggermaNo ratings yet
- F5 TcpdumpDocument14 pagesF5 TcpdumpNETRICH IT SolutionsNo ratings yet
- Snooping de DHCPDocument41 pagesSnooping de DHCPionrivas3355No ratings yet
- Lab 10: Vpns - Ipsec Remote Access VPN: 10.1 DetailsDocument24 pagesLab 10: Vpns - Ipsec Remote Access VPN: 10.1 Detailscharles81No ratings yet
- OpenVPN - How To Set Up A Slackware Server and A Slackware ClientDocument16 pagesOpenVPN - How To Set Up A Slackware Server and A Slackware Clientvpalmar8871No ratings yet
- Troubleshooting OpenVPNDocument16 pagesTroubleshooting OpenVPNgalarragaNo ratings yet
- A VPN Gateway SetupDocument6 pagesA VPN Gateway Setupachmadzulkarnaen100% (1)
- Fire Up Cpan On UbuntuDocument17 pagesFire Up Cpan On UbuntuHarguilar NhangaNo ratings yet
- Open VPNDocument49 pagesOpen VPNAnoop K JayanNo ratings yet
- Open VPNDocument21 pagesOpen VPNkhaluma6022No ratings yet
- Setting Up OpenVPN Server On Centos 7Document13 pagesSetting Up OpenVPN Server On Centos 7Abu FadilahNo ratings yet
- Setting Up OpenVPN Server On UbuntuDocument35 pagesSetting Up OpenVPN Server On UbuntuAbu FadilahNo ratings yet
- Setup OpenVPN Server and Client in 40 StepsDocument48 pagesSetup OpenVPN Server and Client in 40 StepsPapaFrancesco Rodrigo CislaghiNo ratings yet
- The Implementation of COAP SecurityDocument9 pagesThe Implementation of COAP SecurityMohamed Yassine GaraliNo ratings yet
- Centos 6 Easy OpenVPN 1.2 Install GuideDocument11 pagesCentos 6 Easy OpenVPN 1.2 Install Guideworld1capitalNo ratings yet
- Konfigurasi OpenVPN Pada MikrotikDocument51 pagesKonfigurasi OpenVPN Pada MikrotiknuNo ratings yet
- OpenVPN Configuration Step by Step GuideDocument24 pagesOpenVPN Configuration Step by Step GuideMechanicalLatestNo ratings yet
- Racoon Road Warrior ConfigurationDocument20 pagesRacoon Road Warrior Configurationapi-3801485100% (1)
- Callmanager and Ios Gateway DSP Farm Configuration Example: Document Id: 62959Document8 pagesCallmanager and Ios Gateway DSP Farm Configuration Example: Document Id: 62959bala097No ratings yet
- How To Configure OpenVPN Shared Key Tunnels Using PfSense and OpenWRTDocument6 pagesHow To Configure OpenVPN Shared Key Tunnels Using PfSense and OpenWRTcrisao23No ratings yet
- Orbit OpenVPN Feature GuideDocument24 pagesOrbit OpenVPN Feature GuideDavid José Barrios ItriagoNo ratings yet
- OvenMediaEngineDocument167 pagesOvenMediaEnginecephas01No ratings yet
- 08 - Linux ITNSA - OpenVPNDocument20 pages08 - Linux ITNSA - OpenVPNSiskaAmaliaNo ratings yet
- Openvpn HowtoDocument24 pagesOpenvpn HowtoMark ReevesNo ratings yet
- EdgeRouter - L2TP IPsec VPN Server - Ubiquiti Networks Support and Help CenterDocument11 pagesEdgeRouter - L2TP IPsec VPN Server - Ubiquiti Networks Support and Help CenterFlorian MarinNo ratings yet
- View TCP/IP settings and troubleshoot with ipconfig and pingDocument9 pagesView TCP/IP settings and troubleshoot with ipconfig and pingRonald MangeroNo ratings yet
- How To Set Up OpenVPN Server in 5 Minutes On Ubuntu Linux - NixcraftDocument50 pagesHow To Set Up OpenVPN Server in 5 Minutes On Ubuntu Linux - NixcraftDilamar JrNo ratings yet
- CCNP Security Secure Lab GuideDocument150 pagesCCNP Security Secure Lab Guidebkaraqa67% (3)
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- LEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingFrom EverandLEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingNo ratings yet
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksFrom EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNo ratings yet
- OpenVPN Building and Integrating Virtual Private NetworksFrom EverandOpenVPN Building and Integrating Virtual Private NetworksRating: 4.5 out of 5 stars4.5/5 (2)
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- M - Cely VC50Document19 pagesM - Cely VC50gurukosNo ratings yet
- Mame Cabinet DesignDocument1 pageMame Cabinet DesigngurukosNo ratings yet
- iATKOS ML2 Installation GuideDocument13 pagesiATKOS ML2 Installation GuideinvntrsNo ratings yet
- LINUX: Routing For Multiple Uplinks - ProvidersDocument2 pagesLINUX: Routing For Multiple Uplinks - ProvidersgurukosNo ratings yet
- Assembly For BegginersDocument68 pagesAssembly For BegginersGorciu Cristina100% (1)
- ProxySG Required PortsDocument8 pagesProxySG Required PortsbooksmagicNo ratings yet
- Paloalto FW RequirementsDocument5 pagesPaloalto FW RequirementsAbrham GidayNo ratings yet
- Huawei CX600 Metro Services Platform V600R002 Product BrochureDocument8 pagesHuawei CX600 Metro Services Platform V600R002 Product Brochureสุรเชษฐ์ ทองมั่นNo ratings yet
- Google - Prep4sure - Professional Cloud Network Engineer - Vce.download.2023 Aug 04.by - Clyde.62q.vceDocument11 pagesGoogle - Prep4sure - Professional Cloud Network Engineer - Vce.download.2023 Aug 04.by - Clyde.62q.vceahme imtiazNo ratings yet
- 4ipnet ERN EAP705 v3.43.00 20171215Document6 pages4ipnet ERN EAP705 v3.43.00 20171215SteeveNo ratings yet
- Powered by D-Link Rg-S5750e Series Security and Multi-Services Switch Da...Document21 pagesPowered by D-Link Rg-S5750e Series Security and Multi-Services Switch Da...Kapil SinghNo ratings yet
- Iop851-W00C1: Poe Industry Ap-RouterDocument2 pagesIop851-W00C1: Poe Industry Ap-RouterBob YuNo ratings yet
- FibeAir IP-20LH: High-Capacity Multi-Carrier Trunk NodeDocument84 pagesFibeAir IP-20LH: High-Capacity Multi-Carrier Trunk NodesisfNo ratings yet
- PPP IntroDocument28 pagesPPP IntroVivek MurugaiyanNo ratings yet
- Day in The Life of A Packet: PAN-OS Packet Flow Sequence PAN-OS 6.1Document14 pagesDay in The Life of A Packet: PAN-OS Packet Flow Sequence PAN-OS 6.1Dede RizkiNo ratings yet
- F3efmgmibtyx LFS211LabsDocument118 pagesF3efmgmibtyx LFS211LabsMajo TorresNo ratings yet
- Access The Server Using An SSH TunnelDocument3 pagesAccess The Server Using An SSH Tunnelleonard1971No ratings yet
- SSH PDFDocument20 pagesSSH PDFDaniel coooperNo ratings yet
- SSH Tutorial for Linux: A Guide to Secure ShellDocument10 pagesSSH Tutorial for Linux: A Guide to Secure ShellsulekhasweetyNo ratings yet
- Remote Access in 40 CharactersDocument24 pagesRemote Access in 40 Characters25262828No ratings yet
- Configure a Multi-SA Virtual Tunnel Interface on an IOS-XE RouterDocument7 pagesConfigure a Multi-SA Virtual Tunnel Interface on an IOS-XE RouterAkash ThakurNo ratings yet
- VeloCloud Administration Guide PDFDocument403 pagesVeloCloud Administration Guide PDFМаниш Нахтвандерер100% (1)
- AhnLab TrusGuard Security SolutionsDocument85 pagesAhnLab TrusGuard Security SolutionsAms Ajaxneth100% (1)
- AWP 547 01 RelnoteDocument43 pagesAWP 547 01 RelnoteFernala Sejmen-BanjacNo ratings yet
- Netxms AdminDocument524 pagesNetxms AdminAndyNo ratings yet
- Data and Computer Communications: Tenth Edition by William StallingsDocument45 pagesData and Computer Communications: Tenth Edition by William StallingsHasanNo ratings yet
- The Keys To Using SSH: David TomaschikDocument41 pagesThe Keys To Using SSH: David TomaschikMc SalahNo ratings yet
- Configure Remote Access For Siemens PLC Through Tia PortalDocument44 pagesConfigure Remote Access For Siemens PLC Through Tia PortalNhạt'sNo ratings yet
- Diapositivas VPNDocument12 pagesDiapositivas VPNAldair TurizoNo ratings yet
- L2TP v3Document102 pagesL2TP v3berwal1916No ratings yet
- Enterprise Networking, Security, and Automation - VPN TechnologyDocument3 pagesEnterprise Networking, Security, and Automation - VPN TechnologyZulkifliNo ratings yet
- Checkpoint Interview QuestionsDocument7 pagesCheckpoint Interview Questionsneninthe420100% (1)
- VPN GateDocument14 pagesVPN GateEAKANSH GUPTANo ratings yet
- Am Server Deployment Guide For Remote Workers 8AL90345ENAA 11a enDocument170 pagesAm Server Deployment Guide For Remote Workers 8AL90345ENAA 11a ensidney SantiagoNo ratings yet
- Endpoint Security and AuthenticationDocument5 pagesEndpoint Security and AuthenticationFnan KifluNo ratings yet