Professional Documents
Culture Documents
Aim
Uploaded by
Harinder GrewalCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Aim
Uploaded by
Harinder GrewalCopyright:
Available Formats
ASYNCHRONOUS TRANSFER MODE (ATM)
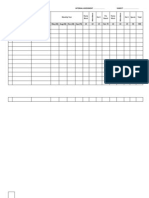
INDEX
Sr. Name of Practicals Page No. Date Signature
1.
Installation steps of WINDOWS XP.
1-8
2.
Installation steps of REDHAT LINUX.
9-20
3.
Write and explain the various commands in REDHAT LINUX Operating System. Study about Router, Hub, & Switch.
21-25
4.
26-29
5.
Comparison of network traffic policy.
30-34
6.
Familiarization with network directory services in Novell system.
35-41
7.
Memory management techniques in ATM.
42-48
8.
Data compression & its effect on network.
49-51
9.
Comparison of utilization of various resources i.e. processor, memory& hard disk. Creation & maintenance of a user account.
52-55
10.
56-58
11.
Security aspects of network system efficiency.
59-63
Gurpreet Singh
1183202
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-1
AIM: - INSTALLATION STEPS OF WINDOWS XP.
REQUIREMENTS: Hardware requirements: CD/DVD, PC. Software requirements: Operating system of window XP.
THEORY:This procedure demonstrates how to install Windows XP Professional. The procedure to install Windows XP home edition is very similar to the professional edition All versions of Windows XP CD are bootable. In order to boot from CD/DVD-ROM you need to set the boot sequence. Look for the boot sequence under your BIOS setup and make sure that the first boot device is set to CD/DVD-ROM. You can then perform the following steps to install Windows XP: Steps1 : Start your PC and place your Windows XP CD in your CD/DVD-ROM drive. Your PC should automatically detect the CD and you will get a message saying "Press any key to boot from CD". Soon as computer starts booting from the CD your will get the following screen:
Step 2 - At this stage it will ask you to press F6 if you want to install a third party Raid or SCSI driver. If you are using an IDE Hard Drive then you do not need to press F6.
Step 3 - Press S to specify that you want to install additional device. Step 4 - You will be asked to insert the floppy disk with the Raid or SCSI drivers. Press enter after you have inserted the disk.
Gurpreet Singh
1183202
ASYNCHRONOUS TRANSFER MODE (ATM) Step 5 - You will see a list of Raid drivers for your HDD. Select the correct driver for your device and press enter.
Step 6 - You will then get a Windows XP Professional Setup screen. You have the option to do a new Windows install, Repair previous install or quit. Since we are doing a new install we just press Enter to continue.
Step 7 - You will be presented with the End User Licensing Agreement. Press F8 to accept and continue Step 8 - This step is very important. Here we will create the partition where Windows will be installed. Press C to create a partition.
Step 8 - Windows will show the total size of the hard drive and ask you how much you want to allocate for the partition you are about to create. Step 9 - Now you will see partition listed you will also have 8MB of unpartitioned space. Don't worry about that. Just leave it how it is. Windows normally has some unpartitioned space.
Gurpreet Singh
1183202
ASYNCHRONOUS TRANSFER MODE (ATM)
Step 10 - Choose format the partition using NTFS file system. This is the recommended file system. If the hard drive has been formatted before then you can choose quick NTFS format. We chose NTFS because it offers many security features, supports larger drive size, and bigger size files.
Windows will now starts formatting drive C: and start copying setup files as shown:
Step 11 - After the setup has completed copying the files the computer will restart. Leave the XP CD in the drive but this time DO NOT press any key when the message "Press any key to boot from CD" is displayed. Windows XP Setup wizard will guide you through the setup process of gathering information about your computer
Gurpreet Singh
1183202
ASYNCHRONOUS TRANSFER MODE (ATM)
Step
12
Choose
your
region
and
language.
Step
13
Type
in
your
name
and
organization.
Step
14.
Enter
your
product
key.
Step 15 - Name the computer, and enter an Administrator password. Don't forget to write
Gurpreet Singh
1183202
ASYNCHRONOUS TRANSFER MODE (ATM) Down your Administrator password.
Step
16
Enter
the
correct
date,
time
and
choose
your
time
zone.
Step
17
For
the
network
setting
choose
typical
and
press
next.
Step 18 - Choose workgroup or domain name. If you are not a member of a domain then leave default settings and press next. Windows will restart again and adjust display.
Step 19 - Finally Windows will start and present you with a Welcome screen. Click next
Gurpreet Singh
1183202
ASYNCHRONOUS TRANSFER MODE (ATM) to continue.
Step 20 - Choose 'help protect my PC by turning on automatic updates now' and press next.
Step 21 - Will this computer connect to the internet directly, or through a network? If you are connected to a router or LAN then choose: 'Yes, this computer will connect through a local area network or home network'. If you have dial up modem choose: 'No, this computer will connect directly to the internet'. Then click next.
Step 22 - Ready to activate Windows? Choose yes if you wish to active Windows over
Gurpreet Singh
1183202
ASYNCHRONOUS TRANSFER MODE (ATM) the internet now. Choose no if you want to activate Windows at a later stage.
Step 23 - Add users that will sign on to this computer and click next.
Step 24 - You will get a Thank you screen to confirm setup is complete. Click finish. Step 25. Log in, to your PC for the first time.
Step 26 - You now need to check the device manager to confirm that all the drivers has been loaded or if there are any conflicts. From the start menu select Start -> Settings -> Control Panel. Click on the System icon and then from the System Properties window select the Hardware tab, then click on Device Manager.
Gurpreet Singh
1183202
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-2
AIM:-INSTALLATION STEPS OF REDHAT LINUX.
REQUIREMENTS: Hardware requirements: CD/DVD,PC Software requirements: Operating system of REDHAT LINUX
THEORY:Installing REDHAT LINUX consists of three main steps: 1. Preparing to run a setup. 2. running a setup 3. Finishing setup and stating REDHAT LINUX To install REDHAT LINUX Workstation on your computer using the Setup disks and/or the REDHAT LINUX Workstation compact disc 1. With your computer turned off, insert the disk labeled "REDHAT LINUX Setup Boot Disk" into drive A of your computer. 2. Turn on your computer. STEPS TO Red Hat 6 RHEL Installations
1. Select Install or upgrade an existing system option on Grub Menu
Gurpreet Singh
1183202
ASYNCHRONOUS TRANSFER MODE (ATM)
2. Choose a language
3. Choose a keyboard type
4. Choose a installation media
5. Skip DVD media test (or select media test, if you want to test installation media before installation)
Gurpreet Singh
1183202
10
ASYNCHRONOUS TRANSFER MODE (ATM)
6. Red Hat 6 graphical installer starts, select next
7. Accepct Pre-Release Installation
8. Select storage devices
Gurpreet Singh
1183202
11
ASYNCHRONOUS TRANSFER MODE (ATM)
9. Insert computer name
10. Select time zone
11. Enter a password for root user
Gurpreet Singh
1183202
12
ASYNCHRONOUS TRANSFER MODE (ATM)
12. Select type of installation
Read every option info carefully. And select encrypting if needed and option to review and modify partition layout.
13. Review partition layout
Modify if needed. Default setup with ext4 and LVM looks good for desktop machine.
Gurpreet Singh
1183202
13
ASYNCHRONOUS TRANSFER MODE (ATM)
14. Accept write changes to disc
15. Writing changes (creating partitions) to disc
16. Configure boot loader options
Select device to install bootloader and check/create boot loader operating system list.
17. Select softwares to install and enable repositories
Gurpreet Singh 1183202 14
ASYNCHRONOUS TRANSFER MODE (ATM) This case we select Software Development Workstation and enable Red Hat Enterprise Linux 6.0 Beta Repository and select Customize now.
18. Customize package selection
Select PHP and Web Server to installation.
Select MySQL and PostgreSQL Databases.
Gurpreet Singh
1183202
15
ASYNCHRONOUS TRANSFER MODE (ATM)
Select set of Development tools like Eclipse IDE.
19. Checking dependencies for installation
20. Starting installation process
Gurpreet Singh
1183202
16
ASYNCHRONOUS TRANSFER MODE (ATM)
21. Installing packages
22. Installation is complete
Click reboot computer and remove installation media.
Gurpreet Singh
1183202
17
ASYNCHRONOUS TRANSFER MODE (ATM)
Red Hat 6 RHEL Finishing Installation
23. Selecting RHEL 6 from grub
24. Booting Red Hat 6
25. Red Hat 6 Welcome screen
Gurpreet Singh
1183202
18
ASYNCHRONOUS TRANSFER MODE (ATM)
26. Create normal user
27. Setup date and time and keep up-to-date with NTP
Gurpreet Singh
1183202
19
ASYNCHRONOUS TRANSFER MODE (ATM)
28. Login Red Hat 6 Gnome Desktop
29. Red Hat (RHEL) 6 Gnome Desktop, empty and default look
Gurpreet Singh
1183202
20
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-3
AIM:-WRITE AND EXPLAIN THE VARIOUS COMMANDS IN REDHAT LINUX OPERAING SYSTEM.
REQUIREMENTS: Hardware requirements: CD/DVD,PC Software requirements: Operating system of REDHAT LINUX
THEORY:To get a Linux shell, you need to start a terminal. That terminal, in turn, runs a Linux command shell. There are many such shells, include csh, Bourne shell, and the Korn Shell. On most Linux distributions today, the default shell is the Bourne again shell (bash). (Yes, Linux users have long loved puns.) That $ sign? In Linux, the dollar sign stands for a shell variable. These are variables that the shell, and any shell program, can use. Some are set as default when you start your Linux PC. For example, $SHELL; $LOGNAME is your login name; and $PATH identifies the directories in which your shell searches for commands. COMMANDS OF LINUX:1. USERADD COMMAND: This command is used to add a new user. Syntax: [ggs@localhost ~]# useradd username 2. PASSWD COMMAND: This command is used to create a password on the username. Syntax: [ggs@localhost ~]# passwd username 3. LS COMMAND: This command is used to show the list of present directories. Syntax: [ggs@localhost ~]$ ls 4. TIME COMMAND:
Gurpreet Singh
1183202
21
ASYNCHRONOUS TRANSFER MODE (ATM) This command is used to show the current time. Syntax: [ggs@localhost ~]$ time 5. CAT COMMAND: This command is used to show the contents of file. Syntax: [ggs@localhost ~]$ cat filename 6. CLEAR COMMAND: This command is used to clear the screen/window. Syntax: [ggs@localhost ~]$ clear 7. DATE COMMAND: This command is used to show the current date. Syntax: [ggs@localhost ~]$ date 8. PWD COMMAND: This command is used to show the name of present working directory. Syntax: [ggs@localhost ~]$ pwd 9. MKDIR COMMAND: This command is used to create a new directory. Syntax: [ggs@localhost ~]$ mkdir dirname 10. RMDIR COMMAND: This command is used to remove or delete the directory. Syntax: [ggs@localhost ~]$ rmdir dirname 11. TOUCH COMMAND: This command is used to create a new file. Syntax: [ggs@localhost ~]$ touch filename
Gurpreet Singh
1183202
22
ASYNCHRONOUS TRANSFER MODE (ATM) 12. CD COMMAND: This command is used to change the directory. Syntax: [ggs@localhost ~]$ cd dirname 13. VIM COMMAND: This command is used to open the file. Syntax: [ggs@localhost ~]$ vim filename 14. ESC :SET NU COMMAND: This command is used to insert a number in starting of each line in open file. Syntax: [ggs@localhost ~]$ esc :set nu 15. ESC :SET NONU COMMAND: This command is used to remove a number from starting of each line in open file. Syntax: [ggs@localhost ~]$ esc :set nonu 16. SU USERNAME COMMAND: This command is used to open other used id. Syntax: [ggs@localhost ~]$ su username 17. ESC :WQ COMMAND: This command is used to save the file. Syntax: [ggs@localhost ~]$ esc :wq 18. CTRL+Z COMMAND: This command is used to cancel the editing in file. Syntax: ctrl+z 19. HISTORY COMMAND: This command is show the previous command history. Syntax:
Gurpreet Singh
1183202
23
ASYNCHRONOUS TRANSFER MODE (ATM) [ggs@localhost ~]$ history 20. INIT 0 COMMAND: This command is used to shutdown the computer. Syntax: [ggs@localhost ~]$ init 0 21. INIT 6 COMMAND: This command is used to restart the computer. Syntax: [ggs@localhost ~]$ init 6 22. REBOOT COMMAND: This command is used to restart the computer. Syntax: [ggs@localhost ~]$ reboot 23. LS LD COMMAND: This command is used to show the list of directories and files. Syntax: [ggs@localhost ~]$ ls ld 24. LS A COMMAND: This command is used to show the hidden files for root handling. Syntax: [ggs@localhost ~]$ ls a 25. LS R COMMAND: This command is used to show the file in recursively. Syntax: [ggs@localhost ~]$ ls r 26. LS LD??R* COMMAND: This command is used to show the name of those files and directories whose third letter is r. Syntax: [ggs@localhost ~]$ ls ld??r*
Gurpreet Singh
1183202
24
ASYNCHRONOUS TRANSFER MODE (ATM) 27. LS LD[A-Z]* COMMAND: This command is used to show the name of those files and directories whose starting or first letter lies between a to z. Syntax: [ggs@localhost ~]$ ls ld[a-z]* 28. LS -1 COMMAND: This command is used to show the i) ii) iii) Syntax: [ggs@localhost ~]$ ls -1 Name of files in black, Name of directories in blue, Name of hidden files and directories with tild (~) symbol.
Gurpreet Singh
1183202
25
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-4
AIM: - STUDY ABOUT ROUTER, HUB AND SWITCH.
REQUIREMENTS: Hardware requirements: HUB, ROUTER & SWITCH.
THEORY:NETWORKING DEVICES :Computer networking devices are units that mediate data in a computer network. Computer networking devices are also called network equipment, Intermediate Systems (IS) or InterWorking Unit (IWU). Units which are the last receiver or generate data are called hosts or data terminal equipment. Computer network devices also known as communication devices and they constitute a data communication network. These devices are routers, switches, hubs, LAN cards, gateway, modems, hardware firewall, CSU/DSU, ISDN terminals and transceivers. In an Ethernet or WAN network, the data communication cannot be performed without these devices. ROUTER A router is a device that forwards data packets between computer networks, creating an overlay internet work. A router is connected to two or more data lines from different networks. When a data packet comes in on one of the lines, the router reads the address information in the packet to determine its ultimate destination. Then, using information in its routing table or routing policy, it directs the packet to the next network on its journey. Routers perform the "traffic directing" functions on the Internet\ A data packet is typically forwarded from one router to another through the networks that constitute the internet work until it gets to its destination node. A router is a communication device that is used to connect two logically and physically different networks, two LANs, two WANs and a LAN with WAN. The main function of the router is to sorting and the distribution of the data packets to their destinations based on their IP addresses. Routers provides the connectivity between the enterprise businesses, ISPs and in the internet infrastructure, router is a main device. Cisco routers are widely used in the world. Every router has routing software, which is known as IOS. Gurpreet Singh 1183202 26
ASYNCHRONOUS TRANSFER MODE (ATM) Router operates at the network layer of the OSI model. Router does not broadcast the data packets.
Routers may also be used to connect two or more logical groups of computer devices known as subnets, each with a different sub-network address. The subnets addresses recorded in the router do not necessarily map directly to the physical interface connections. A router has two stages of operation called planes:
Control plane: A router records a routing table listing what route should be used to forward a data packet, and through which physical interface connection. It does this using internal pre-configured addresses, called static routes.
Forwarding plane: The router forwards data packets between incoming and outgoing interface connections. It routes it to the correct network type using information that the packet header contains. It uses data recorded in the routing table control plane.
ETHERNET HUB:An Ethernet hub, active hub, network hub, repeater hub or hub is a device for connecting multiple Ethernet devices together and making them act as a single network segment. A hub works at the physical layer (layer 1) of the OSI model. The device is a form of
Gurpreet Singh
1183202
27
ASYNCHRONOUS TRANSFER MODE (ATM) multiport repeater. Repeater hubs also participate in collision detection, forwarding a jam signal to all ports if it detects a collision. The central connecting device in a computer network is known as a hub. There are two types of a hub i.e. active hub and passive hub. Every computer is directly connected with the hub. When data packets arrives at hub, it broadcast them to all the LAN cards in a network and the destined recipient picks them and all other computers discard the data packets. Hub has five, eight, sixteen and more ports and one port is known as uplink port, which is used to connect with the next hub.
A network hub is an unsophisticated device in comparison with, for example, a switch. A hub does not examine or manage any of the traffic that comes through it: any packet entering any port is rebroadcast on all other ports. Effectively, it is barely aware of frames or packets and mostly operates on raw bits. Consequently, packet collisions are more frequent in networks connected using hubs than in networks connected using more sophisticated devices. NETWORK SWITCH:A network switch or switching hub is a computer networking device that connects network segments. Switches may operate at one or more layers of the OSI model, including data link and network. A device that operates simultaneously at more than one of these layers is known as a multilayer switch. An Ethernet switch operates at the data link layer of the OSI model to create a separate collision domain for each switch port. With 4 computers (e.g., A, B, C, and D)
Gurpreet Singh
1183202
28
ASYNCHRONOUS TRANSFER MODE (ATM) on 4 switch ports, A and B can transfer data back and forth, while C and D also do so simultaneously, and the two conversations will not interfere with one another. In the case of a hub, they would all share the bandwidth and run in half duplex, resulting in collisions, which would then necessitate retransmissions. Using a switch is called micro segmentation. This allows computers to have dedicated bandwidth on point-to-point connections to the network and to therefore run in full duplex without collisions.
Like the router, a switch is an intelligent device that maps the IP address with the MAC address of the LAN card. Unlike the hubs, a switch does not broadcast the data to all the computers; .it sends the data packets only to the destined computer. Switches are used in the LAN, MAN and WAN. In an Ethernet network, computers are directly connected with the switch via twisted pair cables. In a network, switches use the three methods to transmit the data i.e. store and forward, cut through and fragment free.
Gurpreet Singh
1183202
29
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-5
AIM: - COMPARISON OF NETWORK TRAFFIC POLICY. REQUIRMENTS: Hardware requirements: PC, ROUTER, SWITCH Software requirements: Network traffic policy algorithm THEORY:Traffic management is the act of managing network traffic, providing service guarantees to user connections and ensuring optimal utilization of resources. The scope and nature of traffic management depends upon a number of factors like the switching technique used, the degree of flexibility provided, the performance measures provided and the extent of statically multiplexing done. To provide service guarantees and ensure optimal resource utilization, several Elements of traffic management are used. The important ones are listed below: 1. Traffic Shaping 2. 3. Flow Control Congestion Control
1. TRAFFIC SHAPING:Traffic shaping alters the traffic characteristics of the connection, and delivers a more predictable traffic to the network. Traffic shaper is usually applied before the user traffic enters the network boundary. Shaping increases the chance of a traffic conforming to the parameters of the traffic contract. There are many schemes used for traffic shaping, the most common being the Leaky bucket technique. Leaky Bucket Technique:Consider a bucket of volume V units, with a hole at its bottom through which fluid leaks Out at constant rate R units/ time-unit. Simultaneously, a tap pours fluid into the bucket Intermittently. If at any time the tap starts pouring into the bucket at a rate more than R Units/time unit, the fluid will start accumulating in the bucket. If the rate exceeds for a Long time, the bucket may eventually fill up and start overflowing. Further, as long as there is any water in the bucket, the rate at which the water leaks out of the bucket is
Gurpreet Singh
1183202
30
ASYNCHRONOUS TRANSFER MODE (ATM) always R units/sec. the rate is zero if the bucket is empty.
This idea of regulating the rate of fluid flow using the leaky bucket can be Applied to network traffic as well. Consider the leaky bucket to be a buffer with constant output rate of R units/time-unit. Now, the following operations are permissible: 1. If there is any data in the buffer, the packets are transmitted at a constant rate. 2. If the rate at which packets arrive exceeds the output rate, the buffer will start filling up gradually. 3. If a packet arrives and there is not enough space, the packet is dropped. Using the three steps mentioned above, the output of the leaky bucket can be controlled.
Gurpreet Singh
1183202
31
ASYNCHRONOUS TRANSFER MODE (ATM) 2. FLOW CONTROL:Flow control is a mechanism to control the flow of data between the sender and the receiver so that the receivers buffers do not overflow. Flow control is necessary when a fast processor is communicating with a slow processor. Flow control is necessary to achieve synchronization between the sending capacity of the sender and the processing capacity of the receiver. Flow control mechanisms are broadly classified into two categories: window-based flow control and rate-based flow control. WINDOW BASED FLOW CONTROL:In a typically window based flow control implementation, the source maintains a transmission windows. Packets towards the left of the window are those which have been acknowledged by the receiver. The transmission window contains (1). Packets that have been sent, but are waiting for an acknowledgement and (2) packets that can be sent without the arrival of subsequent acknowledgements. Towards the right of the window are packets that can be sent only after one or more packets of the current transmission window is acknowledged. If at any time the receiver is short of buffer space, it withholds the transmission of acknowledgement. In this manner, the receiver checks the flow of packets.
In the simplest form of window based flow control called sop and wait, the source waits for an acknowledgement after sending every packet. The Acknowledgement from the Gurpreet Singh 1183202 32
ASYNCHRONOUS TRANSFER MODE (ATM) receiver acts as a permission for sending the next packet. The above scheme can be improved by making a minor modification. Instead of allowing just one packet, the source is allowed to send multiple packets, where the number of packets that the sender can send, without receiving an acknowledgement, is referred to as the window size. The window size is fixed for the entire duration for which the connection remains active. Such scheme is called static window based flow control. RATE-BASED FLOW CONTROL:In rate based flow control mechanism, instead of limiting the amount of data sent by a sender, the rate at which data is sent is controlled. In this flow control technique, the sender starts with some initial data rate. The initial rate is fixed at the time of establishment of the connection. Depending on resource availability, the receiver may request the sender to (1) increases the rate or (2) decrease the rate or (3) leave it unchanged. The sender alters its data rate according to the indication received from the receiver.
4. CONGESTION & ITS CONTROL: congestion is a situation when the demand for a limited resource exceeds its supply. In communication network, congestion occurs when the available network resources are not enough to meet the demands. Congestion is one of the most prominent problems in network design. Whenever congestion occurs, the buffer starts overflowing. Subsequently, the packets start getting dropped. To prevent overflows, it is desirable to have large buffers. Causes of congestion:The following are the main causes of congestion:
Gurpreet Singh
1183202
33
ASYNCHRONOUS TRANSFER MODE (ATM) 1. over commitment of shared resources 2. growing disparities in communication link speeds 3. system breakdown 4. non-conformance Congestion control mechanism: - congestion control mechanism is divided into two categories: 1. preventive congestion control 2. reactive congestion control Preventive congestion control:- One of the simplest way to prevent congestion is to build a network that is capable of carrying the worst case user traffic. A different approach to congestion prevention would be to reserve some portion of the bandwidth exclusively for handling transient overload conditions. This is a more practical approach and used in more practical approach and used in many public frame relay and ATM networks. Traffic contracting is another congestion prevention technique. Traffic contracting ensures that the demand from the existing connections does not exceed available resources. Reactive congestion control: - mechanisms to ease out congestion, once it has occurred, come under the reactive congestion control techniques. There are two reactive congestion control techniques. 1. packet discard 2. congestion notification
Congestion control algorithms. When too many packets are present in an N/W.
Gurpreet Singh
1183202
34
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-6
AIM: - FAMILIARIZATION WITH NETWARE DIRECTORY SERVICES (NDS) IN NOVELL SYSTEM. REQUIREMENTS: Software requirements: NetWare network operating system.
THEORY:NOVELL: Novell is a multinational software and services company. It is a wholly owned subsidiary of The Attachmate Group. It specializes in network operating systems, such as Novell NetWare; systems management solutions, such as Novell ZEN works; and collaboration solutions, such as Novell GroupWise and Novell Vibe. Novell was instrumental in making the Utah Valley a focus for technology and software development. Novell technology contributed to the emergence of local area networks, which displaced the dominant mainframe computing model and changed computing worldwide. Today, a primary focus of the company is on developing open source software for enterprise clients. INTRODUCTION TO NETWARE:NetWare is a network operating system developed by Novell, Inc. It initially used cooperative multitasking to run various services on a personal computer, with network protocols based on the archetypal Xerox Network Systems stack. The NetWare NOS consists of server and client applications. The client application is designed to run on a variety of client operating systems. The server application can be accessed by client users from computers running MS-DOS, Microsoft Windows (versions 3.x, 95, and 98, and Windows NT), OS/2, AppleTalk, or UNIX. NetWare is often the NOS of choice in mixed operating-system environments. In small networks, however, NetWare can be expensive and complicated for an inexperienced network technician to install and administer.
Gurpreet Singh
1183202
35
ASYNCHRONOUS TRANSFER MODE (ATM) Its versions: Version 3.2 of NetWare is a 32-bit NOS that supports Windows (versions 3.x, 95, and 98 and Windows NT), UNIX, Mac OS, and MS-DOS environments. With NetWare version 4.11, also called Intranet Ware, Novell introduced its new NOS, Novell Directory Services (NDS). Version 5, the latest version to be released, addresses the integration of LANs, WANs, network applications, intranets, and the Internet, into a single global network. Novell Directory Services (NDS) provides name services as well as security, routing, messaging, management, Web publishing, and file and print services. Using X.500 directory architecture, it organizes all network resources, including users, groups, printers, servers, and volumes. NDS also provides a single-point logon for the user; with it, a user can log on to any server on the network and have access to all their usual user rights and privileges. NETWARE SERVICES With NetWare Client installed, any client workstation can take full advantage of the resources provided by a NetWare Server. The following is a summary of some of the more important services provided. FILE SERVICES NetWare file services are part of the NDS database. NDS provides a single-point logon for users and allows users and administrators alike to view network resources in the same way. SECURITY NetWare provides extensive security, including:
Logon security Provides authentication verification based on user name, passwords, and time and account restrictions.
Trustee rights Controls which directories and files a user can access and what the user is able to do with them.
Gurpreet Singh
1183202
36
ASYNCHRONOUS TRANSFER MODE (ATM)
Directory and file attributes Identifies the kinds of actions that can be carried out on a file (viewed, written to, copied, made shareable or non-shareable, or deleted).
PRINTING SERVICES Printing services are transparent (invisible) to the user of a client computer. Any print request from a client is redirected to the file server, where it is handed off to the print server and finally to the printer. (The same computer can serve as both file server and printer server.) You can share printer devices that are attached to the server, to a workstation, or directly to the network by means of the devices' own network interface card (NIC). NetWare print services can support up to 256 printers. SENDING MESSAGES TO OTHERS By using some simple commands, users can send a short message to other users on the network. Messages can be sent to groups as well as to individuals. If all the intended recipients are in the same group, address the message to the group rather than to each individual. Users can also disable or enable this command for their workstations. When a user disables the command, no broadcast messages will be received by that workstation. INTEROPERABILITY Full NOS interoperability is not always possible. This is especially true when two dissimilar networks, such as NetWare and Windows NT, are being connected. A NetWare environment, centered on its directory services, and Windows NT, operating on a domain model, are inherently incompatible. To overcome this problem, Windows NT developed NWLink and GSNW, discussed earlier, that allow them to interoperate. These services allow a server on the Windows NT network to act as a gateway to the NetWare network. Any workstations on the Windows NT network can request resources or services available on the NetWare network, but they must make the request through the Windows NT server. The server will then act as a client on the NetWare network, passing requests between the two networks.
Gurpreet Singh
1183202
37
ASYNCHRONOUS TRANSFER MODE (ATM) NETWARE DIRECTORY SERVICES (NDS): NetWare Directory Services (NDS) is a globally distributed network database that replaces the bindery used in previous versions of NetWare. Novell eDirectory (formerly known as Novell Directory Services, sometimes referred to as Netware Directory Services) is an X.500-compatible directory service software product initially released in 1993 by Novell for centrally managing access to resources on multiple servers and computers within a given network. As part of NetWare 4.0, NDS maintains information about all network resources (users, groups, servers, volumes, printers, and so on) in a hierarchical tree structure. Network resources can be organized in the tree independent of their physical location. Thus network users can access any network resource they have rights to, without having to know the exact location of that resource. In NetWare 4.0's NetWare Directory Services (NDS), the "Directory" provides structure to a company's computer network system. This tree structure allows you to closely represent the way in which companies are typically organized. Instead of the "flat" organization of the old NetWare Bindery, NDS provides a hierarchical structure which can greatly simplify the administrative tasks of large, complex networks. EDirectory is a hierarchical, object oriented database used to represent certain assets in an organization in a logical tree. Other NOSs provide client software for interoperability with NetWare servers. For example, Windows NT provides Gateway Services for NetWare (GSNW). With this service, a Windows NT server can obtain access to NetWare file and print services.
Gurpreet Singh
1183202
38
ASYNCHRONOUS TRANSFER MODE (ATM)
NDS OBJECTS:The NDS Directory tree is formed by placing "objects" in a hierarchical tree structure. There are many different objects in a network. In NDS terminology, the term "object" is used to mean any item which can exist in the network structure. The Directory tree is made up of three types of objects: Objects that can contain other objects are referred to as container objects. Other objects are simply endpoints that do not contain other objects. These objects are referred to as leaf objects. The special object called [Root] is automatically created at the top of the Directory tree. Example of Directory tree objects.
Gurpreet Singh
1183202
39
ASYNCHRONOUS TRANSFER MODE (ATM)
NDS PROPERTIES:NDS properties are another important component in the Directory. All objects have properties. Each property can have at least one value; many of the properties can have multiple values. Rights for a given property apply to all of its values. You enter the information, or values, about the object into data fields for each property. For example, a User object includes the following properties:
Login Name Telephone Number E-mail Address Password Restrictions Group Membership Address And others
ACCESS CONTROL LISTS:-
All objects can also have a property known as the Access Control List (ACL). The ACL property warrants special examination because it controls access to both the object and its properties. For both the object and its properties, it lists who has rights (trustees) and what those rights are (rights assignments). INHERITED RIGHTS:-
In the NetWare Directory, object and property rights flow from the top of the structure down the tree. When rights flow down the tree, they are known as inherited rights.
Gurpreet Singh
1183202
40
ASYNCHRONOUS TRANSFER MODE (ATM) Inheritance is one of the most important areas to understand regarding the Directory rights. Rights flow (or are inherited) in the NetWare Directory from the top of the tree downward. However, the only rights that are inherited are [Object Rights] and [All Properties Rights]. FILE SYSTEM AND NDS RIGHTS:-
In NetWare 4.0, Supervisor rights to the volumes of a given server derive from Write management of the server object itself. In other words, any user which has at least Write rights to the ACL of the specified server's object will have Supervisor rights at the root of each of the specified server's volumes. Another important thing to remember is that file system rights are granted to trustees, and trustees can be any NDS objects, not just users and groups. For example, if [Root] is made a trustee with Read rights in a given file system directory, all users (anywhere in the NDS tree) have the Read right in that directory. This is true because all users are security equivalent to [Root].
Gurpreet Singh
1183202
41
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-7
AIM: - MEMORY MANAGEMENT TECHNIQUES IN ATM. THEORY:A GENERIC SWITCHING ARCHITECTURE:ATM switch is its ability to buffer cells and quickly relay them without cell loss. However, ATM switches not only relay cells but must also perform control and management functions in order to support both asynchronous and synchronous traffic as well as connectionless and connection-oriented traffic. An ATM switch contains a set of input and output ports, which are utilized to interconnect to users, other switches, and other network elements. It also has interfaces to exchange control and management information with special purpose networks (i.e. network management systems). According to ATM standards, the switching functions of ATM switches are categorized into 3 planes based on the Broadband ISDN model: 1. User plane (U-plane) 2. Control plane (C-plane), 3. Management plane (M-plane). 1. User plane:The User planes relay user information cells from input ports to appropriate output Ports by processing cell headers. It is useful to note that in the User plane, cell payloads are carried transparently through the network. Therefore, this cell relay function can be divided into 3 major blocks: The input module at the input port. The cell switch matrix that performs the routing function. The output modules at the output ports.
2. Control plane:The Control plane deals with call establishment and release of virtual path/virtual channel connections. Information in control cells payload is not transparent to the network because it contains signaling information required for setting-up connections. 3. Management plane:The Management plane provides management functions to ensure correct and
Gurpreet Singh
1183202
42
ASYNCHRONOUS TRANSFER MODE (ATM) efficient network operation. The management function can further be divided as follows: Fault management Performance management Configuration management Security management Accounting management Traffic management
ATM SWITCHING ARCHITECTURE The generic model consists of the following blocks: Input modules Output models Cell switch fabric, Connection admission control (CAC) Switch management
Input modules:The input module performs the termination of incoming signals and the extraction of ATM cell stream. This task involves signal conversion and recovery, overhead processing, and cell delineation and rate decoupling. Furthermore, the input module performs the following function on each ATM cell: Error checking of the header information using HEC field Validation and translation of VPI/VCI values Determination of destination output ports Passing signaling cells to CAC and Operations and Management (OAM) cells to switch management Usage/network parameter control for each VPC/VCC Addition of internal tags with internal routing and performance monitoring information for use only within the switch. Output modules:These prepare the ATM cell streams for physical transmission by: removing and processing the internal tag
Gurpreet Singh
1183202
43
ASYNCHRONOUS TRANSFER MODE (ATM) possible translation of VPI/VCI values HEC field generation possible mixing of cells from CAC and Switch Management with outgoing cell streams cell rate decoupling mapping cells to SONET payloads and generation of SONET overhead conversion of the digital bit stream to an optical signal
A Generic Switch Model Cell Switch Fabric The cell switch fabric is primarily responsible for routing of data cells and possibly signaling and management cells as well. Since the remainder of this paper focuses on the cell switch fabric, the next section is devoted to exploring its various components in considerable detail. Connection admission control:The connection admission control (CAC) is a set of procedures that include actions taken by the network to grant or deny a virtual connection. In other words, CAC establishes, modifies, and terminates virtual path/virtual channel connections. Switch Management The Switch Management has the overall responsibility of providing key information for managing the switch and the network. It performs tasks that include the following: Configuration management of switch components
Gurpreet Singh
1183202
44
ASYNCHRONOUS TRANSFER MODE (ATM) Security control for switch database Usage measurements of switch resources Traffic management Administration of management information base Network Management
ATM SWITCHING TECHNIQUES Within an ATM switch, the cell switch fabric plays a very key role. Its main responsibility is to relay ATM cells as quickly as possible. The cell switch fabric accomplishes this by performing 2 major functions: Concentration, expansion, multiplexing/demultiplexing of traffic Routing and buffering of traffic
The cell switch fabric concentrates traffic received at the input ports for better resource utilization. Lower bit rate traffic are aggregated and multiplexed onto higher bit rate for the switch to perform switching of traffic at standard interface speed from input to output ports. Let us now look at the various design techniques implemented by vendors to enable the switch to perform its main task of relaying ATM cells. Its types:1. Shared Memory Switch 2. Shared Bus Switch 3. Crossbar Switch 4. Multistage Switching 5. Banyan/Delta Switching. 1. SHARED MEMORY SWITCH
The Shared Memory Switch is a technique that uses a common memory for the storage of cells and switching fabric. Incoming cells are multiplexed onto a single line to the switch and are placed in queues. Then, based on cell headers information and internal tags, the switching function (memory controller) decides the order in which cells are move from the input queues to the output queues and ultimately onto the output ports.
Gurpreet Singh
1183202
45
ASYNCHRONOUS TRANSFER MODE (ATM) Here incoming cells are converted from serial to parallel form, and written sequentially to a dual port Random Access Memory. A memory controller decides the order in which cells are read out of the memory, based on the cell headers with internal routing tags. Outgoing cells are demultiplexed to the outputs and converted from parallel to serial form.
2. SHARED BUS/MEDIUM SWITCH The Shared Bus Switch approach utilizes a bus or dual bus architecture to switch cell traffic. Cell traffic is carried through the bus for transmission. With this technique, frame based traffic can also be supported since the busses operates in cell mode. Therefore, the traffic is diced into 48-octet pieces with 5-byte header attached for transmission onto the bus. It is easy to see that frame based traffic can be converted to ATM cells and vice versa with this approach
Shared Bus Switch
3. CROSSBAR SWITCH:The Crossbar Switch is a simple matrix-like space division technique that physically interconnects any of the N inputs to any of the N outputs at crosspoints.
Gurpreet Singh
1183202
46
ASYNCHRONOUS TRANSFER MODE (ATM) Therefore, a crossbar switching fabric consists of N2 crosspoints. It is easy to see that this approach will be difficult to implement for large switches
Crossbar Switching 4. MULTISTAGE SWITCH:The Multistage Switching uses a similar concept to the crossbar switch technique. However, it is designed with a more tree-like structure to reduce the N squared cross points requirement yielding a more economical arrangement. Basically, the inputs and output lines are divided into subgroups of N inputs and N outputs
Multistage Switching 5. BANYAN/DELTA SWITCH:The Banyan/Delta Switching is a concept of an interconnection of stages of switching elements. This technique allows only one path of connection existing between an input to the final output port. With this approach, the routing of traffic is quite simple and straightforward. However, it has one major drawback in that cells may be blocked if Gurpreet Singh 1183202 47
ASYNCHRONOUS TRANSFER MODE (ATM) more than one arrives at a switching element at the same time.
Banyan-Delta Switching
Gurpreet Singh
1183202
48
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-8
AIM: - DATA COMPRESSION AND ITS EFFECT ON NETWORK. THEORY:DATA COMPRESSION:Compression is the process of reducing the size of the data. In computer science and information theory, data compression, source coding or bit-rate reduction involves encoding information using fewer bits than the original representation. Compression can be either lossy or lossless. Lossless compression reduces bits by identifying and eliminating statistical redundancy. No information is lost in lossless compression. Lossy compression reduces bits by identifying marginally important information and removing it. Data compression is particularly useful in communications because it enables devices to transmit or store the same amount of data in fewer bits. Objective of data compression The objective of compression is to reduce the amount of data required to store or transmit digital information. Digital information can take many forms. Some common types of digital information are: textual documents such as email messages, memos, letters, and other documents images such as drawings, illustrations, and photographs; and Temporal media or signals that change over time, such as audio and video.
For each of these types there are standard ways of storing or transmitting the information, Which have been determined by convenience, simplicity, and tradition. Typically, the price of this convenience is a larger data size than is absolutely necessary to convey the information. Data Compression in Technology: Data compression affects most aspects of computing today. In fact many websites use compression to reduce the amount of physical traffic they send and save time. As a developer you're probably familiar with archive utilities that compress files into archives with one of these extensions.
Gurpreet Singh
1183202
49
ASYNCHRONOUS TRANSFER MODE (ATM)
Ace Rar Zip BZ2
Types of data compression There are two types of compression. 1. Lossless 2. Lossy 1. Lossless:Data compression techniques in which no data is lost. The PKZIP (Files that have been compressed using PKWARE are said to be zipped. Decompressing them is called unzipping.) compression technology is an example of lossless compression. For most types of data, lossless compression techniques can reduce the space needed by only about 50%. For greater compression, one must use a lossy compression technique. Note, however, that only certain types of data -- graphics, audio, and video -- can tolerate lossy compression. You must use a lossless compression technique when compressing data and programs. 2. Lossy compression:Data compression techniques in which some amount of data is lost. Lossy compression technologies attempt to eliminate redundant or unnecessary information. Most video compression technologies, such as MPEG, use a lossy technique. ITS AFFECT ON NETWORK: Data compression reduces the size of data frames to be transmitted over a network link. Reducing the size of a frame reduces the time required to transmit the frame across the network. From the point of view of storing, compression is used in backups, for image and sound, internal data of programs, or to compress the program itself. Real applications can be found on image standard like JPEG, or audio standards like MP3, both helped a lot in the multimedia revolution. Also a very important side of this is archivers, commonly called compressors, like ZIP or ARJ. Gurpreet Singh 1183202 50
ASYNCHRONOUS TRANSFER MODE (ATM) Resources like hard disk space, money or time are saved. Data compression provides a coding scheme at each end of a transmission link that allows characters to be removed from the frames of data at the sending side of the link and then replaced correctly at the receiving side. Because the condensed frames take up less bandwidth, we can transmit greater volumes at a time. Compression may not always be appropriate, and can be affected by the following things:
No Standards: Although Cisco IOS software supports several compression algorithms, they are proprietary and not necessarily interoperable. Both ends of a compression transaction must support the same algorithms.
Data Type: The same compression algorithm yields different compression ratios depending upon the type of data undergoing compression. Certain data types are inherently less compressible than others, which can realize up to a 6:1 compression ratio. Cisco conservatively averages Cisco IOS compression ratios at 2:1.
Already Compressed Data: Trying to compress already compressed data, such as JPEG or MPEG files can take longer then transferring the data without any compression at all.
Processor Usage: Software compression solutions consume valuable processor cycles in the router. Routers must also support other functions such as management, security, and protocol translations; compressing large amounts of data can slow down router performance and cause network latency.
The highest compression ratio is usually reached with highly compressible text files. Compressing data can cause performance degradation because it is software, not hardware compression. While configuring compression, use caution with smaller systems that have less memory and slower CPUs.
Gurpreet Singh
1183202
51
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-9
AIM: - COMPARISION OF THE UTILIZATION OF VARIOUS RESOURCES THAT IS PROCESSOR, MEMORY AND HARD DISK.
REQUIREMENTS: Hardware requirements: Processor, Hard Disk, CPU Software requirements: Operating system
THEORY:PROCESSOR:The processor one of the more difficult components to optimize, as the behavior of every other component affects it, e.g. lack of memory causes increased paging, which increases processor usage, fragmented disk drives increase processor usage, hardware interrupts keep the processor busy and applications and services place many demands on the processor. Thus, to optimize the processor you need to examine counters for many other objects, not just the processor itself.
Useful Processor counters include the following: Processor Time:-Threshold near 100%. A fully-utilized processor (100 percent) is not necessarily a sign of a performance bottleneck, so although Processor Time
Gurpreet Singh
1183202
52
ASYNCHRONOUS TRANSFER MODE (ATM) may indicate a potential bottleneck, this is not in itself enough to suggest a solution. You should check Memory Pages/sec to determine whether lack of memory is causing excessive paging.
Interrupts/sec:-
Threshold
varies.
malfunctioning
hardware
device,
particularly a network card, can send excessive interrupts to the processor. Compare this counter with a baseline: a significant increase in the counter without a corresponding increase in system activity may indicate a bad device.
System Processor Queue Length:- Threshold 2. A queue length that is regularly above 2 suggests that threads are backing up as they wait for processor attention.
MEMORY:Memory refers to the physical devices used to store programs (sequences of instructions) or data on a temporary or permanent basis for use in a computer or other digital electronic device. The term primary memory is used for the information in physical systems which are fast (i.e. RAM), as a distinction from secondary memory, which are physical devices for program and data storage which are slow to access but offer higher memory capacity. Primary memory stored on secondary memory is called "virtual memory". The term "storage" is often used in separate computers of traditional secondary memory such as tape, magnetic disks and optical discs (CD-ROM and DVD-ROM). The term "memory" is often associated with addressable semiconductor memory, i.e. integrated circuits consisting of silicon-based transistors, used for example as primary memory but also other purposes in computers and other digital electronic devices. The semiconductor memory is organized into memory cells or bitable flip-flops, each storing one binary bit (0 or 1). The memory cells are grouped into words of fix word length, for example 1, 2, 4, 8, 16, 32, 64 or 128 bit. Each word can be accessed by a binary address of N bit, making it possible to store 2 raised by N words in the memory. This implies that processor registers normally are not considered as memory, since they only store one word and do not include an addressing mechanism.
Gurpreet Singh
1183202
53
ASYNCHRONOUS TRANSFER MODE (ATM) Some common memories are:1. RAM (random-access memory):This is the same as main memory. When used by itself, the term RAM refers to read and write memory; that is, you can both write data into RAM and read data from RAM. This is in contrast to ROM, which permits you only to read data. Most RAM is volatile, which means that it requires a steady flow of electricity to maintain its contents. As soon as the power is turned off, whatever data was in RAM is lost. 2. ROM (read-only memory):Computers almost always contain a small amount of read-only memory that holds instructions for starting up the computer. Unlike RAM, ROM cannot be written to. 3. PROM (programmable read-only memory):A PROM is a memory chip on which you can store a program. But once the PROM has been used, you cannot wipe it clean and use it to store something else. Like ROMs, PROMs are non-volatile. 4. EPROM (erasable programmable read-only memory):An EPROM is a special type of PROM that can be erased by exposing it to ultraviolet light. 5. EEPROM (electrically erasable programmable read-only memory):An EEPROM is a special type of PROM that can be erased by exposing it to an electrical. There are two main types of semiconductor memory: Volatile and Non-volatile. Examples of non-volatile memory are:Flash memory and ROM/PROM/EPROM/EEPROM memory. Examples of volatile memory are:Primary memory (typically dynamic RAM, DRAM), and fast CPU cache memory (typically static RAM, SRAM, which is fast but energy-consuming and offer lower memory capacity per area unit than DRAM).
Gurpreet Singh
1183202
54
ASYNCHRONOUS TRANSFER MODE (ATM) HARD DISK: -
A magnetic disk on which you can store computer data. The term hard is used to distinguish it from a soft, or floppy, disk. Hard disks hold more data and are faster than floppy disks. A hard disk, for example, can store anywhere from 10 to more than 100 gigabytes, whereas most floppies have a maximum storage capacity of 1.4 megabytes. A single hard disk usually consists of several platters. Each platter requires two read/write heads, one for each side. All the read/write heads are attached to a single access arm so that they cannot move independently. Each platter has the same number of tracks, and a track location that cuts across all platters is called a cylinder. For example, a typical 84 megabyte hard disk for a PC might have two platters (four sides) and 1,053 cylinders. In general, hard disks are less portable than floppies, although it is possible to buy removable hard disks.
Gurpreet Singh
1183202
55
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-10
AIM: - CREATION AND MAINTENANCE OF A USER ACCOUNT.
REQUIREMENTS: Hardware requirements:PC Software requirements: Operating system of window NT & window XP or 2000
THEORY:In order to run the Server securely as a service, we need to create a user account for it in Windows. To create a user account in Windows XP Professional or Windows 2000: 1) After we install the Server, open the Computer Management console. (e.g., on the Desktop, right-click My Computer, then click Manage.) 2) Expand the Local users and groups node, right-click Users, and then click New User. The New User dialog box appears. 3) Create the user account (e.g., GSFTPServer), click Create, and then click Close. 4) Close the Computer Management console. 5) In Administrative Tools, click Local Security Policy. The Local Security Settings dialog box appears. 6) Expand the Local Policies node, and then click User Rights Assignment. 7) In the right pane, in the Policy column, double-click Act as part of the operating system. The Properties dialog box appears. 8) Click Add user or Group. The Select Users or Groups dialog box appears. 9) Select the new user we just added (GSFTPServer), click Add, and then click OK. 10) If necessary, assign permissions for this user account in Windows. 11) Assign the server to the new user account and log the server on as a service. To create a user account in Windows NT: 1) After we install the server, open the User Manager (Control Panel > Administrative Tools > User Manager). 2) On the main menu, click File, then click New User to create a new user account for "GSFTPServer". The User Properties dialog box. 3) Provide the Server's information, as shown below, and then click OK. Gurpreet Singh 1183202 56
ASYNCHRONOUS TRANSFER MODE (ATM)
4) On the main menu bar, click Policies, and then click User Rights. The User Rights Policy dialog box appears. 5) Select the Show Advanced User Rights check box. 6) In the Right list, click Act as part of the operating system.
Gurpreet Singh
1183202
57
ASYNCHRONOUS TRANSFER MODE (ATM)
7) Click Add. The Add Users and Groups dialog box appears. 8) Make sure that the drop-down list at the top of this dialog has our own computer selected. Click the Show Users button and select GSFTPServer from the list.
9) Click Add. 10) Click OK in both dialogs. 11) Assign permissions for this user account in Windows. 12) After assigning permissions, we should assign the server to the new user account we have created and then log the server on as a service.
Gurpreet Singh
1183202
58
ASYNCHRONOUS TRANSFER MODE (ATM)
PRACTICAL NO:-11
AIM:-
SECURITY
ASPECTS
OF
NETWORK
SYSTEM
EFFICIENCY.
THEORY:NETWORK SECURITY:Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password. SECURITY MANAGEMENT:Security management for networks is different for all kinds of situations. A home or small office may only require basic security while large businesses may require highmaintenance and advanced software and hardware to prevent malicious attacks from hacking and spamming. Homes & Small Businesses:
A basic firewall or a unified threat management system. For Windows users, basic Antivirus software. An anti-spy ware program would also be a good idea. There are many other types of antivirus or anti-spy ware programs out there to be considered.
Gurpreet Singh
1183202
59
ASYNCHRONOUS TRANSFER MODE (ATM)
When using a wireless connection, use a robust password. Also try to use the strongest security supported by your wireless devices, such as WPA2 with AES encryption.
If using Wireless: Change the default SSID network name, also disable SSID Broadcast; as this function is unnecessary for home use. (However, many security experts consider this to be relatively useless).[5]
Enable MAC Address filtering to keep track of all home network MAC devices connecting to your router.
Assign STATIC IP addresses to network devices. Disable ICMP ping on router. Review router or firewall logs to help identify abnormal network connections or traffic to the Internet.
Use passwords for all accounts. For Windows users, Have multiple accounts per family member and use nonadministrative accounts for day-to-day activities.
Raise awareness about information security to children.
Medium businesses:
A fairly strong firewall or Unified Threat Management System Strong Antivirus software and Internet Security Software. For authentication, use strong passwords and change it on a bi-weekly/monthly basis.
When using a wireless connection, use a robust password. Raise awareness about physical security to employees. Use an optional network analyzer or network monitor. An enlightened administrator or manager. Use a VPN, or Virtual Private Network, to communicate between a main office and satellite offices using the Internet as a connectivity medium. A VPN offers a solution to the expense of leasing a data line while providing a secure network for the offices to communicate. A VPN provides the business with a way to communicate between two in a way mimics a private leased line. Although the
Gurpreet Singh
1183202
60
ASYNCHRONOUS TRANSFER MODE (ATM) Internet is used, it is private because the link is encrypted and convenient to use. A medium sized business needing a secure way to connect several offices will find this a good choice.[7]
Clear employee guidelines should be implemented for using the Internet, including access to non-work related websites, sending and receiving information.
Individual accounts to log on and access company intranet and Internet with monitoring for accountability.
Have a back-up policy to recover data in the event of a hardware failure or a security breach that changes, damages or deletes data.
Disable Messenger. Assign several employees to monitor a group like CERT[8] which studies Internet security vulnerabilities and develops training to help improve security.
Large businesses:
A strong firewall and proxy to keep unwanted people out. A strong Antivirus software package and Internet Security Software package. For authentication, use strong passwords and change it on a weekly/bi-weekly basis.
When using a wireless connection, use a robust password. Exercise physical security precautions to employees. Prepare a network analyzer or network monitor and use it when needed. Implement physical security management like closed circuit television for entry areas and restricted zones.
Security fencing to mark the company's perimeter. Fire extinguishers for fire-sensitive areas like server rooms and security rooms. Security guards can help to maximize security.
Gurpreet Singh
1183202
61
ASYNCHRONOUS TRANSFER MODE (ATM) School:
An adjustable firewall and proxy to allow authorized users access from the outside and inside.
Strong Antivirus software and Internet Security Software packages. Wireless connections that lead to firewalls. Children's Internet Protection Act compliance. (Only schools in the USA) Supervision of network to guarantee updates and changes based on popular site usage.
Constant supervision by teachers, librarians, and administrators to guarantee protection against attacks by both internet and sneaker net sources.
An enforceable and easy to understand acceptable use policy which differentiates between school owned and personally owned devices
FERPA compliance for institutes of higher education
Large government:
A strong firewall and proxy to keep unwanted people out. Strong antivirus software and Internet Security Software suites. Strong encryption. White list authorized wireless connection, block all else. All network hardware is in secure zones. All hosts should be on a private network that is invisible from the outside. Host web servers in a DMZ, or a firewall from the outside and from the inside. Security fencing to mark perimeter and set wireless range to this. Inventory controls of government owned mobile
TYPES OF ATTACKS:Networks are subject to attacks from malicious sources. Attacks can be from two categories "Passive" when a network intruder intercepts data traveling through the network, and "Active" in which an intruder initiates commands to disrupt the networks normal operation.
Gurpreet Singh
1183202
62
ASYNCHRONOUS TRANSFER MODE (ATM) Types of attacks include:1. Passive Network 1. wiretapping 2. Port scanner 3. Idle scan 2. Active Denial-of-service attack Spoofing Man in the middle ARP poisoning Smurf attack Buffer overflow Heap overflow Format string attack SQL injection
NETWORK SECURITY FEATURES:
Comprehensive protection against viruses, spy ware, and other malware Bidirectional firewall with intrusion detection and network integrity safeguard System Guard to protect critical system files and registry Web Control to block inappropriate web-sites Protection against unauthorized termination of security functions Centrally managed deployment and administration Centrally managed malware scans on-demand Real-time event reporting and history logs
Gurpreet Singh
1183202
63
You might also like
- Junior KG - Month 1Document5 pagesJunior KG - Month 1Harinder GrewalNo ratings yet
- Methods of Rear Axle ProductionDocument24 pagesMethods of Rear Axle ProductionHarinder Grewal0% (1)
- Karam VeerDocument18 pagesKaram VeerHarinder GrewalNo ratings yet
- Ja TinderDocument23 pagesJa TinderHarinder GrewalNo ratings yet
- Methods of Rear Axle ProductionDocument24 pagesMethods of Rear Axle ProductionHarinder Grewal0% (1)
- 37243260Document91 pages37243260Harinder GrewalNo ratings yet
- ElectionDocument1 pageElectionHarinder GrewalNo ratings yet
- AimDocument63 pagesAimHarinder GrewalNo ratings yet
- Curriculum Vitae Dr. Seema Puri: Permanent Address: Contact DetailsDocument1 pageCurriculum Vitae Dr. Seema Puri: Permanent Address: Contact DetailsHarinder GrewalNo ratings yet
- Annexure A': Attested Signature and Official Seal of Attesting AuthorityDocument1 pageAnnexure A': Attested Signature and Official Seal of Attesting AuthorityHarinder GrewalNo ratings yet
- Bio-Data: Other Particulars of The FamilyDocument1 pageBio-Data: Other Particulars of The FamilyHarinder GrewalNo ratings yet
- CV Anil Kumar Sales ProfessionalDocument2 pagesCV Anil Kumar Sales ProfessionalHarinder GrewalNo ratings yet
- Career Objective: Harbhajan SinghDocument1 pageCareer Objective: Harbhajan SinghHarinder GrewalNo ratings yet
- Methods of Rear Axle ProductionDocument24 pagesMethods of Rear Axle ProductionHarinder Grewal0% (1)
- Change Name Affidavit TemplateDocument1 pageChange Name Affidavit TemplateHarinder GrewalNo ratings yet
- Dcso Jkfje Vkfjo?Eno: (Te /TKTK WKB K: FT Akl-E"Wh /Tk:'Ibk D/ Gq'Rokw NC Ok DH WHFNZR PZXHDocument2 pagesDcso Jkfje Vkfjo?Eno: (Te /TKTK WKB K: FT Akl-E"Wh /Tk:'Ibk D/ Gq'Rokw NC Ok DH WHFNZR PZXHHarinder GrewalNo ratings yet
- CV Anil Kumar Sales ProfessionalDocument2 pagesCV Anil Kumar Sales ProfessionalHarinder GrewalNo ratings yet
- Test: Mathematics Class-9 Chapter: Number Systems: Time: 1 Hrs. M. Marks: 30Document1 pageTest: Mathematics Class-9 Chapter: Number Systems: Time: 1 Hrs. M. Marks: 30Harinder GrewalNo ratings yet
- Index: Sr. No. Topic Page No. Date SignatureDocument1 pageIndex: Sr. No. Topic Page No. Date SignatureHarinder GrewalNo ratings yet
- AimDocument63 pagesAimHarinder GrewalNo ratings yet
- Bhavesh GargDocument6 pagesBhavesh GargHarinder GrewalNo ratings yet
- PerformaDocument4 pagesPerformaHarinder GrewalNo ratings yet
- Non MedicalDocument1 pageNon MedicalHarinder GrewalNo ratings yet
- Practical File of Advanced Educational Psychology 2012-2013Document2 pagesPractical File of Advanced Educational Psychology 2012-2013Harinder GrewalNo ratings yet
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5782)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (890)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (72)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)