Professional Documents
Culture Documents
Cisco SAN-OS VPN Configuration
Uploaded by
IrfeeCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Cisco SAN-OS VPN Configuration
Uploaded by
IrfeeCopyright:
Available Formats
Cisco SAN-OS VPN Configuration
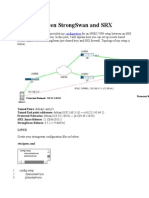
Scenario 1: Storage-to-Router with preshared secrets The following is a typical storage-to-router VPN that uses a preshared secret for authentication. 172.23.9.0/24 | |-+------------+ /-^-^-^-^--\ +-----------+ | | MDS System |=====| Internet |=====| Gateway B |-----| +------------+ \--v-v-v-v-/ BW+-----------+BL | 14.15.16.17 22.23.24.25 172.23.9.1 |-| MDS System is connected to Gateway B through Internet. MDS System's WAN (Internet) interface has the address 14.15.16.17. Gateway B connects the internal LAN 172.23.9.0/24 to the Internet. Gateway B's WAN (Internet) interface has the address 22.23.24.25. Gateway B's LAN interface address, 172.23.9.1, can be used for testing IPsec but is not needed for configuring MDS System. The IKE Phase 1 parameters used in Scenario 1 are: * * * * * * Main mode TripleDES SHA-1 MODP group 2 (1024 bits) pre-shared secret of "hr5xb84l6aa9r6" SA lifetime of 28800 seconds (eight hours) with no kbytes rekeying
The IKE Phase 2 parameters used in Scenario 1 are: * * * * * * * TripleDES SHA-1 ESP tunnel mode MODP group 2 (1024 bits) Perfect forward secrecy for rekeying SA lifetime of 3600 seconds (one hour) with no kbytes rekeying Selectors for all IP protocols, all ports, between 14.15.16.17/32 and 172.23.9.0/24, using IPv4 subnets
To set up MDS System for this scenario, use the following steps: Cisco SAN-OS 2.0(1) which supports IPSec on a "2x1GE IPS, 14x1/2Gbps FC Module/Supervisor". All configuration changes are volatile, and immediate, until the "copy running-config startup-config" command is executed, when the configuration is saved to flash and will be reloaded after a reboot. At any time, you may examine the running configuration with the command "show running-configuration", or view the saved configuration with
the command "show startup-config". Most commands can be abbreviated. Use a ? at the prompt or in a command to see options. To configure IPSec for the scenario shown in above figure, follow these steps: Enable IKE and IPSec in MDS System. MDS# config term MDS(config)# crypto ike enable MDS(config)# crypto ipsec enable Configure IKE in MDS System. MDS(config)# crypto ike domain ipsec MDS(config-ike-ipsec)# key hr5xb84l6aa9r6 address 22.23.24.25 MDS(config-ike-ipsec)# initiator version 1 address 22.23.24.25 MDS(config-ike-ipsec)# policy 1 MDS(config-ike-ipsec-policy)# encryption 3des MDS(config-ike-ipsec-policy)# hash sha MDS(config-ike-ipsec-policy)# group 2 MDS(config-ike-ipsec-policy)# lifetime seconds 28800 MDS(config-ike-ipsec-policy)# end MDS# Configure the ACL in MDS System. MDS# conf t MDS(config)# ip access-list acl1 permit ip 14.15.16.17 0.0.0.0 172.23.9.0 0.0.0.255 Configure the transform set in MDS System. MDS(config)# crypto transform-set domain ipsec tfs-02 esp-3des esp-sha1-hmac Configure the crypto map in MDS System. MDS(config)# crypto map domain ipsec cmap-01 1 MDS(config-crypto-map-ip)# match address acl1 MDS(config-crypto-map-ip)# set peer 22.23.24.25 MDS(config-crypto-map-ip)# set transform-set tfs-02 MDS(config-crypto-map-ip)# set security-association lifetime seconds 3600 MDS(config-crypto-map-ip)# set pfs group2 MDS(config-crypto-map-ip)# end MDS# Bind the interface to the crypto map set in MDS System. (2x1GE IPS, 14x1/2Gbps FC Module is in slot7 of MDS A and GigE 7/1 is connected to Internet) MDS# conf t MDS(config)# int gigabitethernet 7/1 MDS(config-if)# ip addr 14.15.16.17 255.255.255.0 MDS(config-if)# crypto map domain ipsec cmap-01 MDS(config-if)# no shut MDS(config-if)# exit MDS(config)# Configure route in MDS System. MDS(config)# MDS(config)# ip route 172.23.9.0 255.255.255.0 14.15.16.1 MDS(config)# exit MDS# Verify the configuration in MDS System. MDS# show crypto global domain ipsec security-association lifetime Security Association Lifetime: 450 gigabytes/3600 seconds
MDS# show crypto map domain ipsec Crypto Map cmap-01 1 ipsec Peer = 22.23.24.25 IP ACL = acl1 permit ip 14.15.16.17 255.255.255.255 172.23.9.0 255.255.255.0 Transform-sets: tfs-02, Security Association Lifetime: 450 gigabytes/3600 seconds PFS (Y/N): Y PFS Group: group2 Interface using crypto map set cmap-01: GigabitEthernet7/1 MDS# show crypto transform-set domain ipsec Transform set: tfs-02 {esp-3des esp-sha1-hmac} will negotiate {tunnel} MDS# show crypto spd domain ipsec Policy Database for interface: GigabitEthernet7/1, direction: Both # 0: deny udp any port eq 500 any # 1: deny udp any any port eq 500 # 2: permit ip 14.15.16.17 255.255.255.255 172.23.9.0 255.255.255.0 # 127: deny ip any any MDS# show crypto sad domain ipsec interface: GigabitEthernet7/1 Crypto map tag: cmap-01, local addr. 14.15.16.17 protected network: local ident (addr/mask): (14.15.16.17/255.255.255.255) remote ident (addr/mask): (172.23.9.0/255.255.255.0) current_peer: 22.23.24.25 local crypto endpt.: 14.15.16.17, remote crypto endpt.: 22.23.24.25 mode: tunnel, crypto algo: esp-3des, auth algo: esp-sha1-hmac tunnel id is: 1 current outbound spi: 0x900b01e (151040030), index: 0 lifetimes in seconds:: 3600 lifetimes in bytes:: 4718592000 current inbound spi: 0x38fe700e (956198926), index: 0 lifetimes in seconds:: 3600 lifetimes in bytes:: 4718592000 MDS# show crypto ike domain ipsec key key hr5xb84l6aa9r6 address 22.23.24.25 MDS# show crypto ike domain ipsec policy Priority 1, auth pre-shared, lifetime 28800 secs, encryption 3des, hash sha, DH group 2 MDS# show crypto ike domain ipsec sa Tunn Local Addr Remote Addr Encr Hash Auth Method Lifetime ------------------------------------------------------------------------------1* 14.15.16.17[500] 22.23.24.25[500] 3des sha preshared key 28800 ------------------------------------------------------------------------------NOTE: tunnel id ended with * indicates an IKEv1 tunnel
You might also like
- Design Network by Irfee: DHCP + Enterprise WPA2 AuthenticationDocument12 pagesDesign Network by Irfee: DHCP + Enterprise WPA2 AuthenticationIrfee100% (1)
- How To Configure Role Based CliDocument5 pagesHow To Configure Role Based CliIrfeeNo ratings yet
- DNS + DHCP + HTTPS ServerDocument14 pagesDNS + DHCP + HTTPS ServerIrfee100% (1)
- Lan2lan VPNDocument6 pagesLan2lan VPNFelix BlasioNo ratings yet
- Seven Steps To SubnettingDocument4 pagesSeven Steps To SubnettingIrfeeNo ratings yet
- Packet Tracer Activity Configure IP ACLs To Mitigate AttacksDocument3 pagesPacket Tracer Activity Configure IP ACLs To Mitigate AttacksIrfeeNo ratings yet
- Configuring Devices For Use With Cisco Configuration Professional (CCP) 2.5Document8 pagesConfiguring Devices For Use With Cisco Configuration Professional (CCP) 2.5Irfee100% (1)
- Operations Management - Bottlenecks - Critical Path - Line BalancingDocument16 pagesOperations Management - Bottlenecks - Critical Path - Line BalancingIrfee100% (1)
- Configuring ASA 5510 Basic Settings and Firewall Using CLIDocument18 pagesConfiguring ASA 5510 Basic Settings and Firewall Using CLIIrfee75% (8)
- Network Plumbing: Configuring Secure Shell On Routers and Switches Running Cisco IOSDocument10 pagesNetwork Plumbing: Configuring Secure Shell On Routers and Switches Running Cisco IOSIrfeeNo ratings yet
- Vertical Integration or Outsourcing - Nokia - Ford - Toyota - IBM - Intel - Toshiba - MatsushitaDocument8 pagesVertical Integration or Outsourcing - Nokia - Ford - Toyota - IBM - Intel - Toshiba - MatsushitaIrfee100% (1)
- Jet Red - Human Resourse Management - Performance MGMT CycleDocument21 pagesJet Red - Human Resourse Management - Performance MGMT CycleIrfee100% (2)
- Aflac Insurcance Comapny's Marketing DescionsDocument2 pagesAflac Insurcance Comapny's Marketing DescionsIrfee0% (1)
- Just in Time Management - US Vs JapanDocument5 pagesJust in Time Management - US Vs JapanIrfee100% (1)
- Agri EntrepreneurshipDocument7 pagesAgri EntrepreneurshipIrfeeNo ratings yet
- Delta Model: CiscoDocument21 pagesDelta Model: CiscoIrfeeNo ratings yet
- Creative EconomyDocument7 pagesCreative EconomyIrfee100% (1)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (588)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (400)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (345)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (121)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- VPN JUNIPER-FORTI v2Document5 pagesVPN JUNIPER-FORTI v2Alberto Huamani CanchizNo ratings yet
- Fortigate Study Guide Page 237: "By Default, Logs Older Than 7 Days Are Deleted From Disk (Log Age Is Configurable) "Document50 pagesFortigate Study Guide Page 237: "By Default, Logs Older Than 7 Days Are Deleted From Disk (Log Age Is Configurable) "Martin CastañedaNo ratings yet
- 350 701 2Document43 pages350 701 2Ashraf SaeedNo ratings yet
- Asa Lab Manual PDFDocument114 pagesAsa Lab Manual PDFJulian Gomez50% (2)
- Q1Document25 pagesQ1download pack100% (1)
- L2Tp/Ipsec Remote Access VPN Configuration ExampleDocument4 pagesL2Tp/Ipsec Remote Access VPN Configuration ExampleBruno PereiraNo ratings yet
- Configuring Ipsec Site-To-Site VPN Using SDMDocument35 pagesConfiguring Ipsec Site-To-Site VPN Using SDMrajkumarlodhNo ratings yet
- How To Configure Nokia Mobile VPN For Nokia IP VPN Gateway CRDocument16 pagesHow To Configure Nokia Mobile VPN For Nokia IP VPN Gateway CRVictor DikediNo ratings yet
- IPSEC Between StrongSwan and SRXDocument5 pagesIPSEC Between StrongSwan and SRXSon Tran Hong NamNo ratings yet
- GSMA IR.51-v4.0 IMS Profile For Voice Video SMS Over WiFiDocument16 pagesGSMA IR.51-v4.0 IMS Profile For Voice Video SMS Over WiFidjati hidayatNo ratings yet
- h12 711 PDFDocument4 pagesh12 711 PDFrefka babouriNo ratings yet
- Cisco IPSEC High Availability Solution - Stateful Failover For IPsecDocument16 pagesCisco IPSEC High Availability Solution - Stateful Failover For IPsecBehnam BagheriNo ratings yet
- NAT Traversal NAT-T in IPSEC VPNDocument6 pagesNAT Traversal NAT-T in IPSEC VPNSideral Luján CarriónNo ratings yet
- Exam NSE7 - EFW-6.0: IT Certification Guaranteed, The Easy Way!Document52 pagesExam NSE7 - EFW-6.0: IT Certification Guaranteed, The Easy Way!jacostapl_579802982No ratings yet
- Aaa Accounting Through Aaa Local Authentication Attempts Max-FailDocument14 pagesAaa Accounting Through Aaa Local Authentication Attempts Max-Failobee1234No ratings yet
- Juniper Secure Connect Administrator GuideDocument113 pagesJuniper Secure Connect Administrator GuidePhuong TranNo ratings yet
- Exam Nse7 - Efw: IT Certification Guaranteed, The Easy Way!Document45 pagesExam Nse7 - Efw: IT Certification Guaranteed, The Easy Way!ivoNo ratings yet
- BRKSEC 3052 TroubleshootingDocument133 pagesBRKSEC 3052 Troubleshootingvch801No ratings yet
- Juniper SRX Series & GreenBow IPSec VPN Client Software Configuration (English)Document13 pagesJuniper SRX Series & GreenBow IPSec VPN Client Software Configuration (English)greenbowNo ratings yet
- Ciena Encryptor ManualDocument46 pagesCiena Encryptor Manualsrotenstein3114No ratings yet
- CH 32 Security in The Internet IPSec SSLTLS PGP VPN and Firewalls Multiple Choice Questions and Answers PDFDocument9 pagesCH 32 Security in The Internet IPSec SSLTLS PGP VPN and Firewalls Multiple Choice Questions and Answers PDFIshaNo ratings yet
- Virtual Private Network Architecture: Cati Charging and Accounting Technology For The InternetDocument30 pagesVirtual Private Network Architecture: Cati Charging and Accounting Technology For The InternetTHE_ROMILNo ratings yet
- 15 0 ePDG AdminDocument121 pages15 0 ePDG AdminĐăng Đào HảiNo ratings yet
- Ac Admin 302Document420 pagesAc Admin 302omoboyNo ratings yet
- Checkpoint Packet FlowDocument3 pagesCheckpoint Packet FlowSurajKumarNo ratings yet
- Fortigate Firewall CommandlineDocument11 pagesFortigate Firewall Commandlinepyayheinhtet.bhNo ratings yet
- User 2Document21 pagesUser 2EdoNo ratings yet
- 28 - 21gratisexam - 312-50v10 v2020-01-10 by Brian 160qDocument73 pages28 - 21gratisexam - 312-50v10 v2020-01-10 by Brian 160qsanaladresNo ratings yet
- Network Assessment Checklist - NSE4 Exam PDFDocument19 pagesNetwork Assessment Checklist - NSE4 Exam PDFZokou Oscar FabriceNo ratings yet
- ASA5500 - Configuration - Guide - 8.4 and 8.6 - VPN - Configuring LAN-to-LAN VPNsDocument1 pageASA5500 - Configuration - Guide - 8.4 and 8.6 - VPN - Configuring LAN-to-LAN VPNschassisdNo ratings yet